
How many people are aware of the new mobile banking “Trojan Virus -SOVA” that enables hackers to access legitimate logged-in sessions from customers without needing to know the banking credentials? It used to concentrate on nations like the US, Russia, and Spain, but in July 2022 it added numerous more nations, including India.
A brand-new type of banking trojan known as the SOVA virus was found in September 2021. This trojan was revealed at a hacking forum.
Table of Content
SOVA History
The variations of this virus came in March 2022. These updated versions have features like 2FA interception and session cookie theft. Threat researchers in July 2022 found a new version (v4) of the SOVA malware that was targeting more than 200 mobile apps, including banking and cryptocurrency trading apps. The malicious actors behind the SOVA banking trojan began distributing a new version of this banking trojan in May 2022. This version of SOVA malware may conceal itself under well-known Android apps, like the one we tested, which was a fake Chrome app in addition to the fake Chrome app that can also spoof apps like Amazon. Additionally, warnings about an Android malware Trojan known as SOVA have begun to be distributed to consumers by SBI, PNB, and Canara Bank.
How Did This Malware Spread and Operate?
By way of SMS phishing attacks, this malware gets disseminated. The trojan program begins gathering the list of installed apps and sending it to its command-and-control server as soon as it is set up.
This Android virus can capture screenshots, log keystrokes, steal cookies and credentials, and more. By utilizing an Android accessibility service, this banking malware can swipe and do gesture-like screen clicks, which makes it unique.
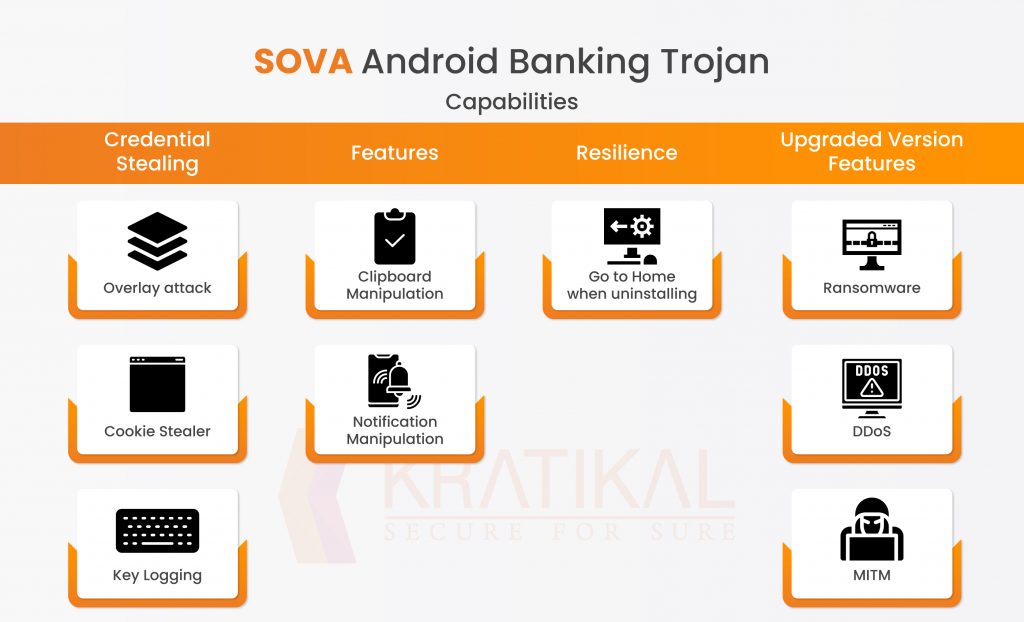
The creator of the Sova Android trojan also made available its fifth version, which can encrypt all the data on that Android phone. By misusing the accessibility feature, the Android banking trojan also makes it impossible to remove it from the Android device.
Technical Analysis of APK Permission
We conducted a static analysis of this APK to see what permissions the SOVA Android malware needs. Analysis revealed that this app is granted permission for practically everything. The following lists a few of the permits.
uses-permission android:name=”android.permission.READ_SMS”/>
<uses-permission android:name=”android.permission.READ_PHONE_NUMBERS”/>
<uses-permission
android:name=”android.permission.SYSTEM_ALERT_WINDOW”/>
<uses-permission
android:name=”android.permission.WRITE_EXTERNAL_STORAGE”/>
<uses-permission
android:name=”android.permission.WRITE_CONTACTS”/> <uses-permission
android:name=”android.permission.REORDER_TASKS”/> <uses-permission
android:name=”android.permission.CHANGE_WIFI_STATE”/> <uses-permission
android:name=”android.permission.REQUEST_INSTALL_PACKAGES”/> <uses-permission
android:name=”android.permission.READ_PHONE_NUMBERS”/> <uses-permission
android:name=”android.permission.DISABLE_KEYGUARD”/>
Let’s try to understand the above permission one by one. We will see what permission this app gets when you run it.
- Android. Permission. READ_ SMS: This permission allows the app to read stored SMS on your phone.
- Android. Permission. READ_ PHONE_ NUMBERS: As you can guess by the permission name this permission allows the app to read your contact number stored on your phone.
- SYSTEM_ALERT_WINDOW: This allows the app to draw on top of other apps. This is the permission this banking trojan is using to interfere with your use of other apps.
- WRITE_EXTERNAL_STORAGE: The Sova banking trojan uses this permission to modify or delete or store content on your phone storage or SD card.
- Android. Permission. WRITE_CONTACTS: Allows the app to modify the data about your contacts stored on your phone, including the frequency with which you’ve called, emailed, or communicated in other ways with specific contacts. This permission allows apps to delete contact data.
- Android. Permission. REORDER_TASKS: Allows the app to move tasks to the foreground and background. The app may do this without your input.
- Android. Permission. CHANGE_WIFI_STATE: Allows the app to connect to and disconnect from Wi-Fi access points and to make changes to device configuration for Wi-Fi networks.
- Android. Permission. REQUEST_INSTALL_PACKAGES: Allows the app to request installing packages.
- Android. Permission. DISABLE_KEYGUARD: Allows the app to disable the keylock and any associated password security. For example, the phone disables the keylock when receiving an incoming phone call, then re-enables the keylock when the call is finished.
Few Features of Permissions
The malware is granted numerous permissions, including the ability to read, send, and receive SMS, as well as the ability to read, write, and read phone numbers. get permission to launch an overlay attack when a specific application, typically a bank app, is launched. These permissions include QUERY ALL PACKAGES, REQUEST INSTALL PACKAGES, INSTALL PACKAGES, and REQUEST DELETE PACKAGES. They also include getting permission to access the victim’s phone’s location using the ACCESS FINE LOCATION, ACCESS COARSE LOCATION, and ACCESS.
Other permissions, such as DISABLE KEYGUARD, which temporarily disables the phone lock while the program is in use Move tasks between the foreground and background using the REORDER TASKS feature of the app. RECORD AUDIO the app’s ability to record audio, and CALL PHONE allows a call to be made by an application without using the dialer’s user interface. ACTION MANAGE OVERLAY PERMISSION Limiting the programs that can draw on top of other apps mitigates the overlay threat. RECEIVE BOOT COMPLETED will alert you when the system has finished booting.
There is a service called Headless Sms Send Service which uses SEND_RESPOND_VIA_MESSAGE that enables the Android trojan to send requests to other messaging apps to handle respond-via-message events for incoming calls.
Indicator of compromise
Following are the IoC to keep track of this Banking Trojan App
File type: .apk
File Hash:
- APK: 74b8956dc35fd8a5eb2f7a5d313e60ca, 0533968891354ac78b45c486600a7890, ca559118f4605b0316a13b8cfa321f65
- C2 Server: socrersutagans[.]site, Omainwpatnlfq[.]site, Satandemantenimiento[.]com wecrvtbyutrcewwretyntrverfd[.]xyz
How to Patch up with SOVA Malware?
Cybersecurity professionals must utilize clever cybersecurity solutions to stay up to date with the changes and upgrades due to the ongoing advances made to SOVA malware every few months.
To keep users safe from malware, the CERT-In provided several preventative measures and suggested practices. Kratikal, a Cert-In Empanelled company, makes operating a secure mobile payments business simpler than ever. Financial institutions can develop a risk-based mobile security plan using the most up-to-date threat intelligence for mobile banking, and they can use this special information to quickly identify malware-based fraud on clients’ mobile devices. We are developing a user-friendly information system with the help of our clients and partners to combat the rising threat of mobile malware that targets the financial industry.
If you’re interested in learning more about how we identify mobile malware on mobile devices, you may get in touch with us directly.


