How long does it take for a data breach to be detected? And how quickly can the organizations report the incident?
According to an IBM report, it takes an average of 287 days for industries to detect and contain a data breach, with a cost of $4.87 million. At this rate, a data breach discovered in January will not be considered until October of the same year.
If this much time is usually spent just identifying a breach, how long does it usually take organizations to report it?
Table of Contents
What is Cert-In?
CERT-In has caused quite a stir with the announcement of its new cyber security guidelines on 28 April 2022. The release calls for reporting of any cyber security incident, including data breaches, within 6 hours of noticing the incident to the Indian Computer Emergency Response Team (CERT-In).
CERT-In has been allowing industries to report incidents within a reasonable time so timely actions could be taken, but in the light of identifying some gaps which cause hindrance during the analysis of a security incident, a new set of guidelines have been issued.
In order to attend to these unidentified gaps, it has decided to issue directions related to information security practices, procedures, prevention, response, and reporting of cyber security incidents under sub-section (6) of section 70B of the Information Technology Act, 2000.
Which Industries to Follow Cert-In Guidelines-
- Service Providers
- Intermediaries
- Data Centers
- Government Entities
- Body Corporates
The additional guidelines shared by CERT-In in the release:

Other than the above-mentioned guidelines, CERT-In has added a few more directives for organizations to follow.
- All service providers, intermediaries, data centers, body corporates, and Government organizations are mandated to enable the logs of their ICT systems and maintain them for a period of 180 days. Indian jurisdiction will maintain the same.
- Data Centers, Virtual Private Server (VPS) providers, Cloud Service providers, and Virtual Private Network (VPN) service providers are required to register information like validated names of subscribers, validated addresses and contact numbers, etc., for a period of 5 years or longer.
- The virtual asset service providers, virtual asset exchange providers, and custodian wallet providers are required to maintain all information obtained as Know Your Customer (KYC), and records of financial transactions for a period of 5 years.
These rules will be in effect after 60 days from the issue of the release.
These rules have been mandated by CERT-In for the aforementioned industries to ensure cyber security in financial markets for citizens to protect their data, fundamental rights, and economic freedom.
After reading these rules, one must ask themselves, “What is this CERT-In?” “What is the purpose of these rules?” To understand why these rules are so important, we must first understand what CERT-In is.
CERT-In: The National Agency Handling India’s Cyber Security Concerns
The Computer Emergency Response Team (CERT) is a government-approved agency that tackles the security challenges faced by the IT sector. Every country has its own institutions that handle information security issues. Similarly, India has their own Indian Computer Emergency Response Team, also known as CERT-In, which oversees the cyber security affairs of India.
CERT-In serves as the national agency for performing multiple cyber security functions in the country under the Ministry of Electronics and Information Technology. Like any other country’s Computer Emergency Response Team (CERT), CERT-In analyzes cyber threats and handles the cyber incidents which are reported to it.
The Goals and Functions of CERT-In
CERT-In adheres to the functions prescribed in section 70B of the Acts to assist cyber users in India in implementing measures to reduce risk of cyber security incidents by:
- Collecting, analyzing, and disseminating information on cyber incidents.
- Forecasting and alerting about cyber security incidents.
- Handling emergency measures for cyber security incidents.
- Coordinating cyber incident response activities.
- Issuing guidelines, advisories, vulnerability notes, and whitepapers for cyber incidents.
Types of Incidents Dealt by CERT-In
CERT-In addresses all cyber security incidents which occur in the country with a swift response to cut down further damage or loss of information. The cyber security incidents covered by CERT-In include:
- Physical cyber security threats to human beings.
- Severe cyber security incidents on any public information framework including backbone network infrastructure.
- Large-scale attacks like identity theft, intrusion into computer resources, website defacement, etc.
- A compromised user account on a multi-user system.
Other than the above-mentioned incidents, all the other incidents are prioritized according to their severity and extent.
CERT-In EMPANELMENT
Multiple audit rounds are required to qualify for CERT-In empanelled These audits assess the applicant organization’s capabilities and technical skills. Among the audit’s various rounds are:
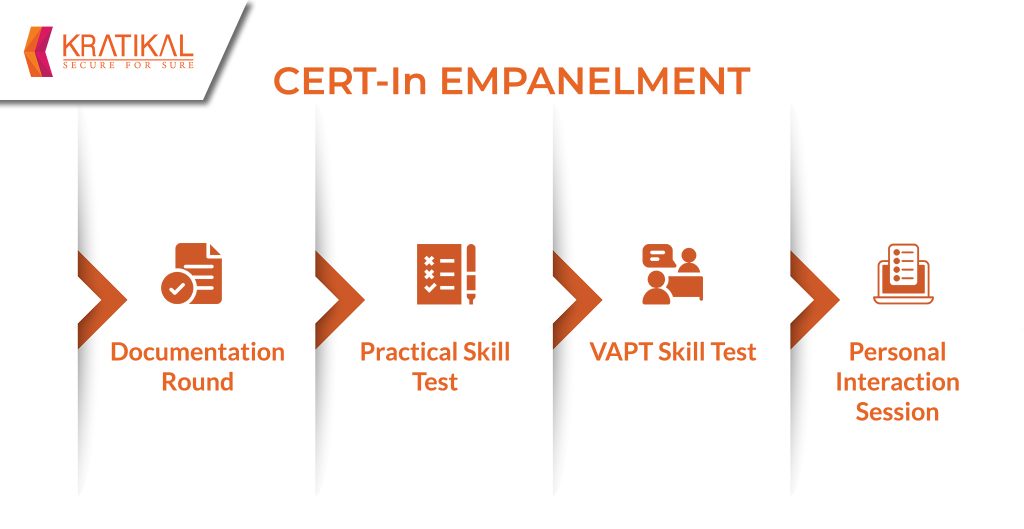
- Documentation Round: The organization is required to submit different documents in this round such as a Background verification certificate, Consent form, previous audit reports, and more.
- Practical Skill Test: After clearing the first round, the organization is then required to test their skills by detecting the known vulnerabilities in the given applications/services, and submitting the VAPT report for it.
- Vulnerability Assessment/Penetration Testing Skill Test: Different setups with different sets of vulnerabilities are hosted and participant organization is required to identify the vulnerabilities and overcome the challenges in the assigned setup.
- Personal Interaction Session: A face to face interaction with the auditor team for the empanelment review process.
If an organization clears all the required steps of the empanelment, it becomes eligible for the certificate, and is called a CERT-In empanelled Security Auditor.
KRATIKAL AS A CERT-IN EMPANELLED SECURITY AUDITING COMPANY
Kratikal Tech Pvt. Ltd. is one of the leading firms that provide Cyber Security Solutions. It was empanelled by CERT-In in 2021 for providing Information Security Auditing Services. Kratikal offers a complete VAPT testing suite which includes:
- Web Application Testing
- Network Penetration Testing
- Cloud Security Testing
- IoT Security Testing
- Medical Device Security Testing
- Secure Code Review
Kratikal has expertise in dealing with the cyber security challenges faced by organizations with complex IT infrastructures, which has led to an increase in the number of clients we serve. The Empanelment was given to Kratikal because of our exceptional technical skills and capabilities, which make us a dependable Security Auditing Firm recognized by CERT-In.
Do you believe that implementing CERT- IN guidelines will be beneficial in combating cybercrime? Please share your thoughts in the comments section below!








Leave a comment
Your email address will not be published. Required fields are marked *