
People are not aware that modern buildings are changing and have changed to an industrial control system. They are now embedded with IP-based technologies and are connected with controllers and sensors and management software. Now by this, building owners can take advantage of low-cost management of their important assets with minimal staff. The building management solution can control and monitor your building environment. BMS are used in many sectors like IT, Banking, and commercials. Many BMS provide access through the web interface where they have an admin panel. The admin staff can control the assets of their building from this BMS admin panel.
Table of Content
Introduction
BMS are really useful for managing your building but unfortunately, their web interfaces are exposed to the internet and can be accessed from anywhere on the internet. This allows threat actors to access the BMS admin panel. It has been observed that multiple BMS are prone to basic cyber attacks. Attacks like file inclusion and command injection can let an attacker do serious harm like they can control building doors, cameras, and lights or stopping other important assets.
As BMS have become so important for many infrastructures, managing their security is equally important. In this blog, we will see what are the cybersecurity issues these BMS are facing and why regularly auditing their security is important.
Building Management System
Building Management System also called the Building Automation System is a computer-based controller. It’s used for monitoring and controlling services and systems of the building. The below picture shows what are the components of BMS that can be managed through BMS. There are components like sensors, fans, boilers, HVAC Systems, Elevators, Security cameras, and card readers. Combining this is called a BMS.
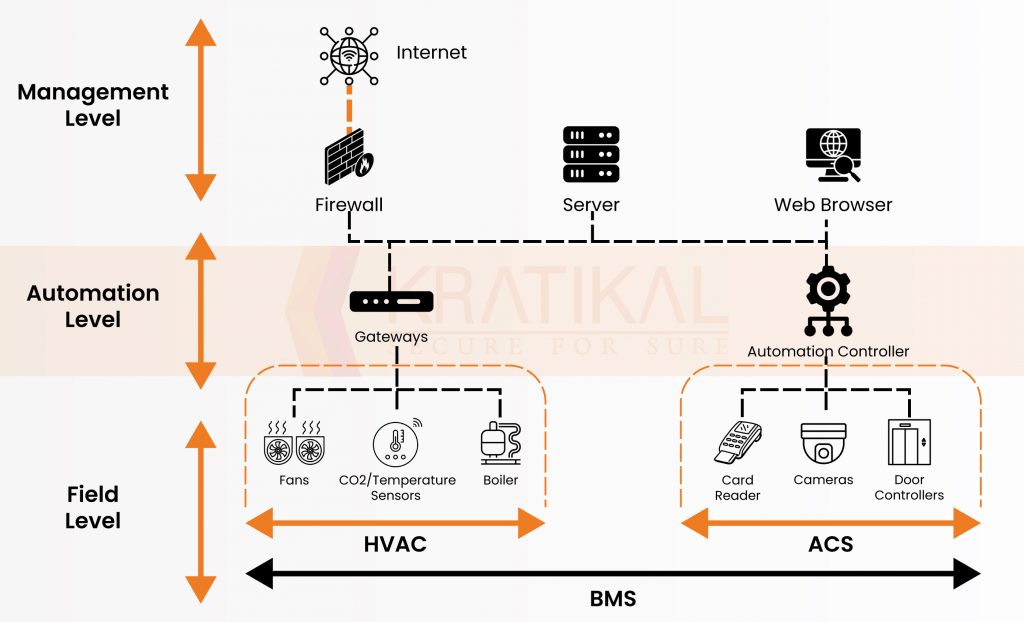
BMS allow only authorized users in a building to. There are so many organizations like the government and the health sector that use such user access control system to only allow authorized users into their facilities. Many access control systems use electronic door access controllers, these devices can be connected to other devices like fingerprint scanners, and automated gates. They can provide the functionality to manage entire access control from the internet.
Security of Building Management Systems
Remote access to these BMS can allow us easy management of a building. As the number of internet-accessible devices is increasing so is the BMS web interface. Exposing these devices to the internet, these components can be accessed by anyone over the internet. It can take little to no effort to find vulnerabilities and exploit them and this can impact highly on integrity and confidentiality.
The risk include in these attacks are:
- Viewing access logs to track movements
- Manipulating alarm function
- Steal personal information
- Control elevator movement
- Can lock or unlock doors remotely
- Shutdown important services
Methodology
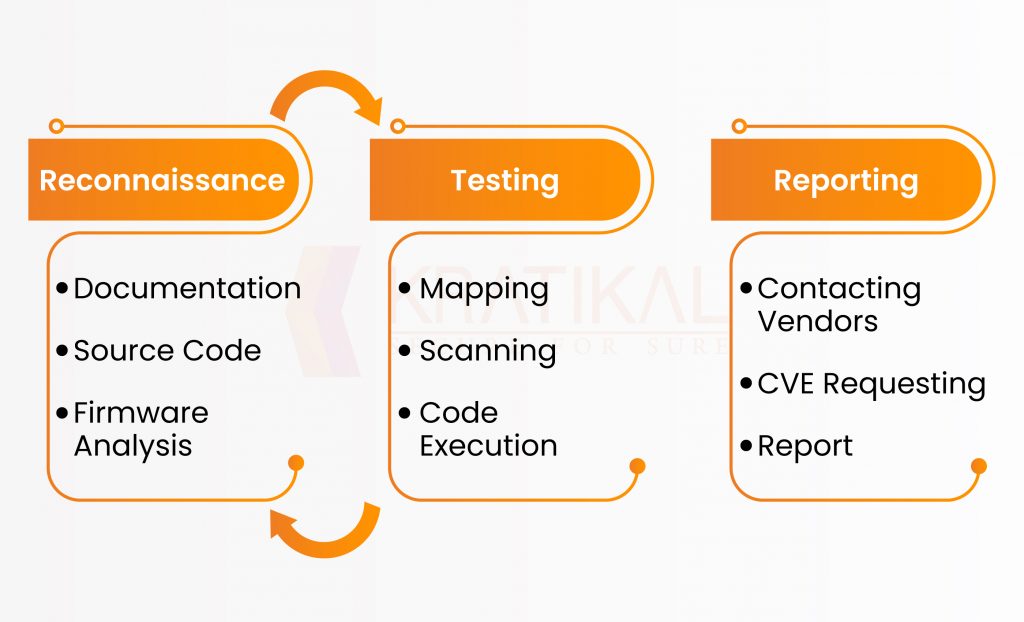
Performing security assessment is a black-box approach in this case. As security analysts have no access to such pentesting, image representation, and the steps mentioned below.
- Recon: This step includes the methodology of scanning and discovering exploitable security flaws inside the device.
- Pentesting: This step focuses on the web interface or Admin panel of the BMS component. This step includes examining most repeating issues. We selected the web interface because it’s the only way to access the BMS that’s why our focus was on exploiting the web application.
- Reporting: All discovered bugs were exploited, the vulnerabilities were reported and a CVE number was assigned.
Number of online accessible BMS –
The amount of internet-connected web interfaces of BMS is growing. A threat actor can use an IoT search engine like shodan, zoomeye, and censys to find online connected BMS. We used shodan to get an idea of how exposed these online BMS are.
The above image shows by just searching the vendor name on shodan, how many exposed devices we were able to find. There could be more than this which can be found through other search engines. As these devices are internet accessible so can be abused as BMS can be of hospitals and government organization buildings. There is also the possibility of denial of service attacks which can be done by an attacker from anywhere over the internet.
Conclusion
BMS has the ability to badly harm your structure, but it may also make managing your property easier for you if it’s properly protected. Human dependability is gone because the Building Management System uses IP-based technology and includes web interfaces that can be accessed online, where hackers may easily access and use them literally from anywhere in the globe.
We at Kratikal, a Cert-In empanelled organization, can assist you in selecting the best procedures to fulfil your BMS needs. We can create electronics and write firmware for battery management systems with a range of functions by our extensive experience in BMS design. Our engineers have extensive experience developing reliable algorithms that determine the BMS Structure.
What are your thoughts on the matter? Share your thoughts about BMS in the comment section below!


