Many applications use the Windows API to integrate Windows features like security, user interface, and other system compatibility with ease. The application employs the CryptoAPI function to encrypt the data and gives developers capabilities that enable their apps to be cryptographically secure. The CryptoAPI function enables programmers to select the algorithms and protocols that best meet their requirements. This API is a suitable option for Windows-based software because it also provides certificate checks and signature verification.
This feature is susceptible due to a recent bug in Windows CryptoAPI. The issue, which affects how the API functions, has confounded and annoyed both users and developers. In this blog post, we’ll go over the crypto API vulnerability in greater detail, along with its consequences on users and possible solutions.
Table of Contents
Get in!
Join our weekly newsletter and stay updated
What is Crypto API Bug?
A CVE-2022-34689 designated flaw in the CryptoAPI function makes Windows computers susceptible to certificate spoofing. By digitally certifying a malicious executable and convincing Windows to believe that certificate, an attacker can use this vulnerability to run malicious code on the target system.
Hash collision is the cause of this vulnerability. The CryptoAPI hash collision flaw can also affect browsers; if a browser depends on this function, an attacker could fake a website’s certificate to allow intercepting SSL – TLS connections.
How does a Crypto API Bug Occur?
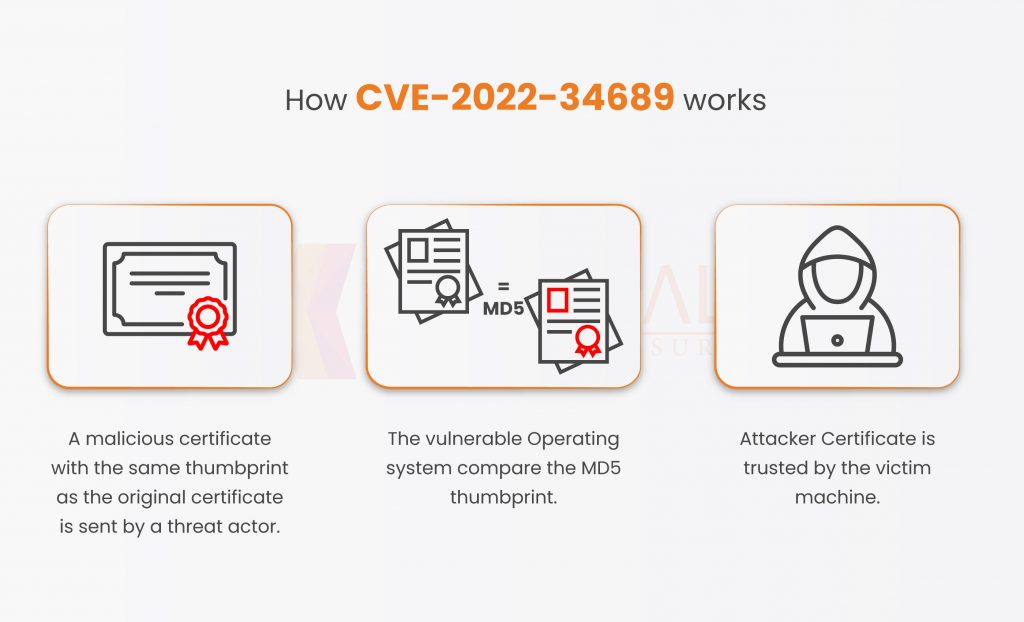
The MD5 collision occurred in the CryptoAPI certificate cache index, which is the source of the issue. This implies that two distinct blocks of data have the same hash value.
Below are the steps of how this happens.
- What an attacker does is serve a malicious certificate whose MD5 collides with the victim’s certificate cache.
- The vulnerable application compares the MD5 thumbprint ( Unique ID ).
- The victim machine trusts the attacker or the certificate issued by the attacker.
Reasons for Crypto API Bug is Dangerous
This malicious version, however, enables Windows to accept any bogus certificate or malicious software. This means that you must figure out a way to check whether a website is trustworthy before viewing it.
When you go to a bogus gmail.com website, your browser prevents you from opening or even accessing it. The CryptoAPI problem is making it possible for similar fraudulent websites and applications to function on your computer, and your browser will likewise claim that the site is trustworthy and your connection is secure.
Who is therefore impacted by this? According to a statement made by Akamai researchers, “We determined that less than 1% of visible devices in data centers are patched, leaving the rest unprotected from the exploitation of this vulnerability.”
Get in!
Join our weekly newsletter and stay updated
The exploitation of the Bug
Use a browser that implements this API for certificate verification to exploit this flaw. As soon as this function receives the certificate validation, the Man In The Middle tricks the browser into believing it is communicating with a trustworthy server.
Proof of Concept
Let’s crackdown on the PoC shown in the above picture.
- Evil_coll.cer: – This is the malicious certificate that the threat actor utilized in a collision attack with the legitimate certificate,
- Serve_website.py:- This script will manage my fictitious website’s SSL certificate. The spoof URL will be https://wwqa.microsoft.com/hello.
- Mitm_script.py: – This script acts as a Man in the Middle proxy, changing the end certificate during the TLS handshake of a “genuine” TLS server. The task is to change the end certificate with the updated certificate. As stated in the script, it will then return the modified message, which will be regarded as a full TLS handshake.
As seen in the screenshot up top, the Akamai PoC is functioning as intended. It is trusting a phony TLS connection to “microsoft.com”. Remember that this PoC was created using the Windows crypt32.dll vulnerability and Chrome version 48.
To avoid such risky vulnerabilities, make sure to patch your windows and stay up to date.
How to Mitigate the Bug?
One can take a few actions to resolve this problem and defend your company against malicious attacks. Below are the actions to be taken –
- Install the most recent version of your operating system.
- Use the Windows patch to address this issue.
Conclusion
Cybersecurity professionals must utilize clever cybersecurity solutions to stay up to date with the changes and upgrades due to the ongoing unpatched Vulnerabilities used.
To keep users safe from such exploits, the CERT-In provided several preventative measures and suggested practices. Kratikal, a Cert-In Empanelled company, can help you choose the best methods to meet your application security requirements. We can check for switch vulnerabilities, and update your system to adhere to the best security procedures. We are developing a user-friendly information system with the help of our clients and partners to combat the rising High severity Vulnerabilities that target organizations.
If you’re interested in learning more about how we identify such API Bugs, you may get in touch with us directly.








Leave a comment
Your email address will not be published. Required fields are marked *