

- 9.9 million malware attacks were detected in 2019 (source: 2020 Cyber Threat Report)
- 94% of breaches involve malware attacks, sent via email as malicious attachments
Table of Content
Malware Attacks: Definition and Types
Ever since the world has seen the dawn of modern computing, software has become as proficient as the programmers who developed them. As internet users, various wondrous software has empowered us with powerful applications to make our lives easier. These applications across diverse mediums and platforms help us, users, to work more efficiently.
But along with amazing benefits, it has also led to the development of highly malicious and downright dangerous software. The infamous malware attacks that affect our systems and businesses, reap from these malicious software programs only. One way or another we all have come across malware attacks. While some of us may have avoided it smoothly, others might have fallen victim to these attacks.
But the reality is that none of us is fully aware of ‘what is a malware attack?’ or ‘what is malware?’ in general. In this blog, we will be discussing everything about malware attacks in brief and simple terms.
What is malware and what are malware attacks?
Malware is a short term for “malicious software”. It is a computer program that is designed with malicious intent to cause damage to a computer system, server, client, or network. This malicious program comes with various threats like spyware, virus, worms, adware, trojan horses, scareware, rogue software, etc.
Malware attack, on the other hand, is a cybercrime where cybercriminals create malicious software (malware) and install them on targeted users’ devices, without their knowledge. Their purpose in carrying out this attack is either to obtain access to personal or sensitive information of users or to damage their devices for financial gain.
These attacks are carried out using various methods such as sending malware-laden emails, creating websites to download malware-laden software or files, ad pop-ups, through malicious removable media, etc. As dangerous as these methods sound, they are infamously renowned for various types of malware attacks.
Some of the most common types of malware attacks are:
- Ransomware Attack
The malware encrypts users’ access to the system, files, or personal information and demands money (ransom) in exchange for decrypting everything back to its normal form. It is the most infamous type of malware attack in which cybercriminals lock or seal the user’s system or data for a certain time period until the ransom is paid. They often increase the amount when the user misses the deadline.
Apart from financial gains, cybercriminals misuse users’ data by leaking confidential information on public websites or on the dark web. The average ransomware attack cost on enterprises is $133,000. In a WannaCry ransomware attack, the National Health Service had to face a loss of about $100 million.
- Man-in-the-browser (MitB) Attack
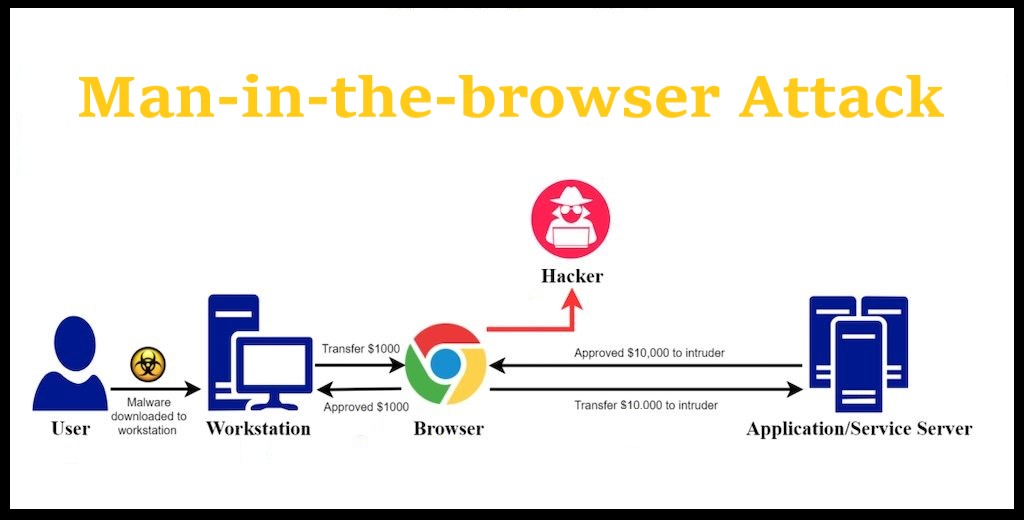
The Man-in-the-browser attack is similar to the man-in-the-middle attack. The cyber attacker injects malware into the victim’s computer, which further installs itself into the internet browser without the victim’s knowledge. The malware then records the data that is used or sent between the victim and particularly the targeted website. Once the data recorded is programmed to collect, it is then transmitted back to the cyber attacker.
- Exploit Kit
It is a malicious tool kit that is used by cyber threat actors to exploit security vulnerabilities found on the targeted user’s computer or other devices, to spread malware. This kit comes with a pre-written code that searches for vulnerabilities. Once a vulnerability is detected, this kit injects malware into the targeted user’s system through that security vulnerability.
It is one of the most effective malware attacks that cyber threat actors use. Moreover, exploit kits are one of the reasons why it is so necessary to patch all security vulnerabilities with the latest updates.
- Spyware
This malware is installed on the users’ devices without their knowledge. It invades the device to steal the personal information of the user and relays it to advertisers, data companies, or external users. Spyware is usually used for tracking and selling internet usage data, capturing financial information, or stealing personal identities without the consent of the users. It is mostly classified into four types: adware, trojans, system monitors, and tracking cookies.
Besides these most common types of malware attacks, we have some real cases of the most notorious and dangerous malware attacks that took many renowned companies by storm.
5 Real Cases of Famous Malware Attacks
Below mentioned are some of the famous Malware Attacks:-
- CovidLock –
Recently in March 2020, a new trend of tracking COVID-19 cases began where every internet user downloaded its application. While people across the globe were busy surviving the pandemic, cybercriminals found the situation as a great opportunity to leverage cyber attacks. Cybercriminals designed and developed a malware-laden application to entrap people searching for information related to COVID-19.
They launched a new type of ransomware attack called CovidLock using malware where once the user installs the application, CovidLock encrypts key data on its Android device. It denies all access to the victim until they pay the demanded ransom. This ransomware infects victims through malicious files that make false promises to offer detailed information related to the disease.
- LockerGoga-

This ransomware attack made headlines in the news in 2019 for infecting Altran Technologies and the Norwegian aluminum company Norsk Hydro. The malware named LockerGaga behind this ransomware attack brought the company’s IT system to a halt. The threat actors infected systems with malicious emails, phishing scams, and credential theft. It was estimated that the attack caused damage in millions of dollars.
- Robin Hood-
The most infamous incident known as the Baltimore ransomware attack occurred in May 2019 in Baltimore, Maryland. The servers of the city were largely compromised by the ransomware variant called Robinhood. All servers were taken offline due to the attack, except the servers of the essential services.
The attackers sent a ransom note where they demanded 13 bitcoin (approx. $76, 280) in return for keys to restore access. It also stated that the price would increase if their demands were not fulfilled within four days. They also threatened that the city would permanently lose all of the data in case of delay, within 10 days. Reportedly, this dangerous attack caused financial damage of up to $18.2 million.
- Emotet, Trojan-
Emotet is a trojan that came into the limelight after the U.S. Department of Homeland Security defined it as the most destructive and highly dangerous malware. The reason being, this malware is widely used by cybercriminals for financial information thefts like bank logins, cryptocurrencies, etc.
This malware spreads via malicious emails as spam and phishing campaigns. The Chilean bank Consorcio and the city of Allentown, Pennsylvania, are the 2 most-affected cases of this malware attack. The bank suffered from damages of $2 million whereas the city faced a loss of $1 million.
- WannaCry-
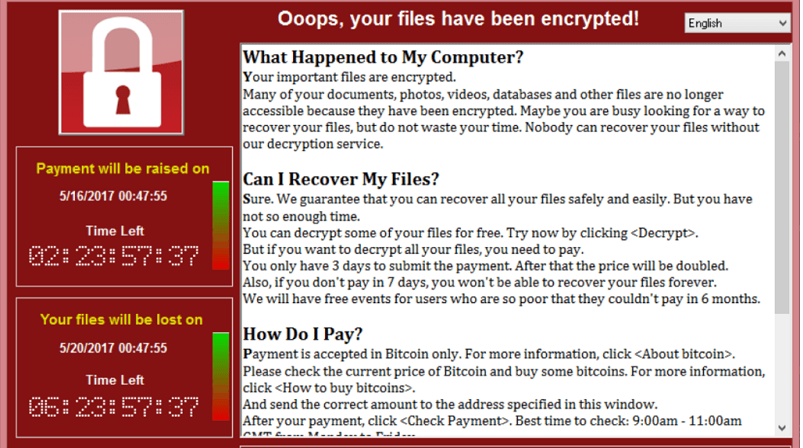
In 2017, computer systems across Britain, Spain, Russia, Ukraine, and Taiwan fell victim to a large coordinated attack. The WannaCry ransomware attack took over servers in these countries. It took control over users’ computers, files, accounts, data and demanded a ransom in return for access control. Around 230,000 computers were infected and cost $4 billion of financial damage. British hospitals were forced to dismiss patients. Whereas the creators of WannaCry ransomware asked for a paltry $300 ransom from the NHS.
Malware Attack Prevention for Your Organization
From the above-mentioned real cases of malware attacks, it can be concluded that cybercriminals are ruthless and can go beyond imagination to cause destruction. We are well aware that ever since the occurrence of the pandemic, these malware attacks have been making rounds in nearly every industry vertical now. No matter what size, scale, or type of organization it is, it won’t be a shock to see another malware attack making headlines in the news tomorrow.
Therefore, in view of the current situation, all we can do is take preventive measures in advance and implement the best cybersecurity solutions to combat malware attacks in the near future. However, the most effective preventive measure that every organization must follow is encouraging security awareness. It is the first and foremost step for every organization. It is important for employees to be well aware of the prevailing cyberattacks, and they should be trained on how to respond to such attacks.
Today, cybersecurity challenges are increasing day by day due to the new normal work-from-home policy. But companies like Kratikal offer virtual security solutions such as ThreatCop to help organizations in maintaining their cyber resilience.
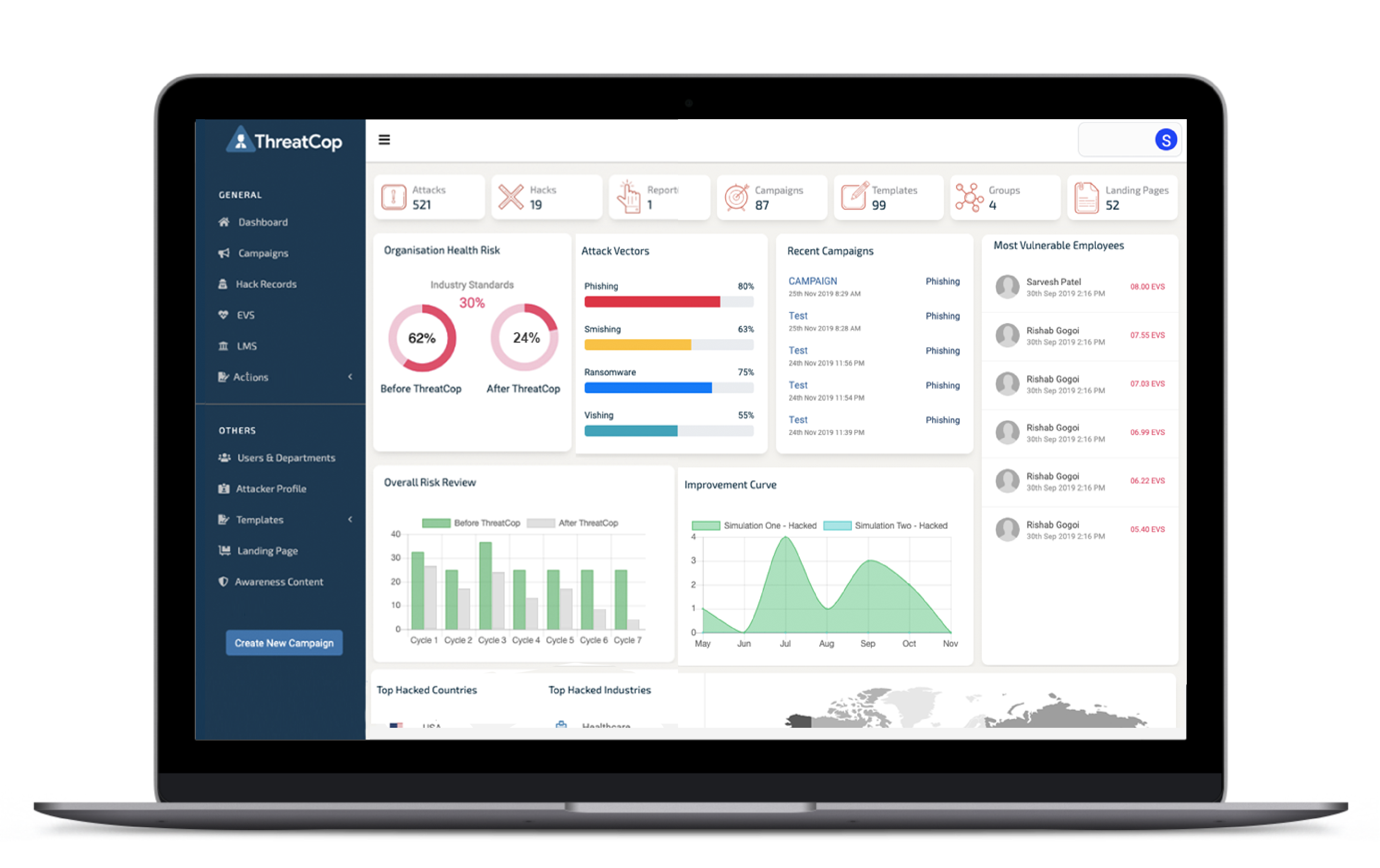
ThreatCop is a cyberattack simulation and awareness tool that develops cyber defense capability among employees in the organization. This tool assesses the real-time threat posture of the organization from people’s point of view. What sets this tool apart is its following amazing features:
- Simulates 6 most common cyber attacks
- Customized Campaigns
- Employee Threat Profile
- Hack Records of Employees
- Gamified Assessment
- Comprehensive Campaign Report
Many renowned organizations have been using ThreatCop to train their employees and have turned their employees from the weakest to the strongest link in cybersecurity. Moreover, Kratikal is offering 1 free simulation of ThreatCop for 100 users. Train your employees with 2000+ awareness content on security including videos, newsletters, case studies, etc. Besides, with ThreatCop you get zero out financial losses that are otherwise incurred due to successful cyber attacks.
Click here to learn more about ThreatCop: https://www.threatcop.ai/
Did you find this blog helpful? Let us know what you think in the comment section below!
Do You Know
Who Is The Weakest Link In The
Cyber Security Chain?
You will be shocked but…it is your EMPLOYEES!
Make your employees proactive against prevailing cyber attacks with ThreatCop!

