The rapid adoption of Internet of Things (IoT) gadgets, which has increased connection and general performance across many aspects of our lives, has changed how we interact with the modern world. However, this progress has also brought forth unheard-of challenges in ensuring the security and privacy of those related devices. Strong protection capabilities are essential as IoT is increasingly integrated into our homes, places of work, and public infrastructure.
This blog will explain how to find vulnerabilities in IoT devices, networks, and software.
Table of Contents
What is IoT Security Testing?
IoT device security testing involves examining IoT devices to identify potential weaknesses that malicious individuals might exploit to breach your network and manipulate your confidential data. Such breaches can bring about significant economic losses, identification of risks, and damage to the recognition of each company and the device. Implementing safety features on your IoT gadgets is essential to ensure their protection in opposition to hackers and unauthorized customers.
IoT security testing aims to uncover vulnerabilities for unauthorized access, control, or theft of sensitive data by potential threat actors. IoT Penetration Testing enables businesses to strengthen the security posture of their IoT devices and networks by simulating various attack scenarios and evaluating local safety measures. This proactive approach assists in mitigating risks, ensuring data integrity, and safeguarding against potential cyber threats and attacks.
What are the threats to IoT?
As we all know, the Internet of Things or Internet-related devices are anywhere, Industrial Control systems, and smart homes, all are connected to the Internet so they may be operated from anywhere. But, as we said, they may be linked to the internet and may be accessed by way of all people.
For example searching “Server: Prismview Player” on Shodan can reveal Samsung’s electronic billboard.
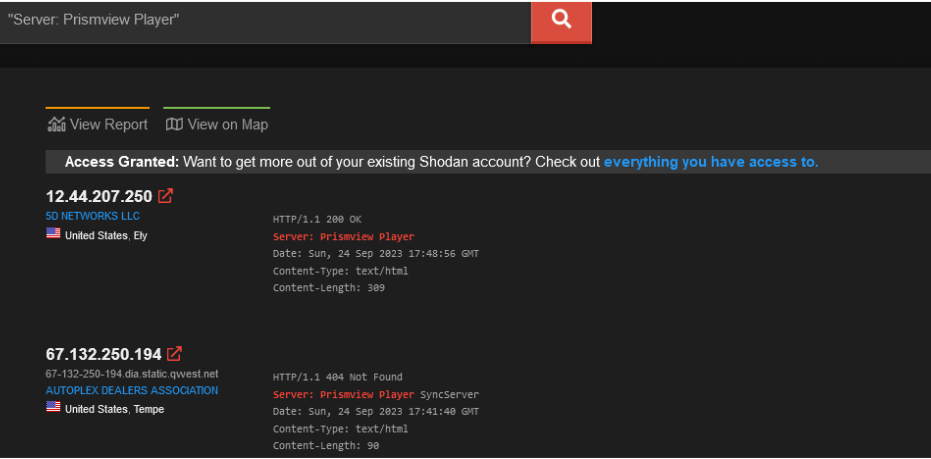
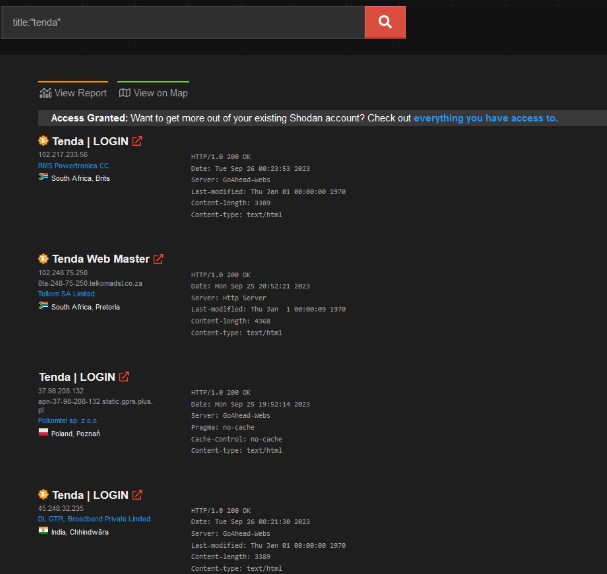
Or just adding the title:” Tenda” can reveal internet-exposed Tenda routers.
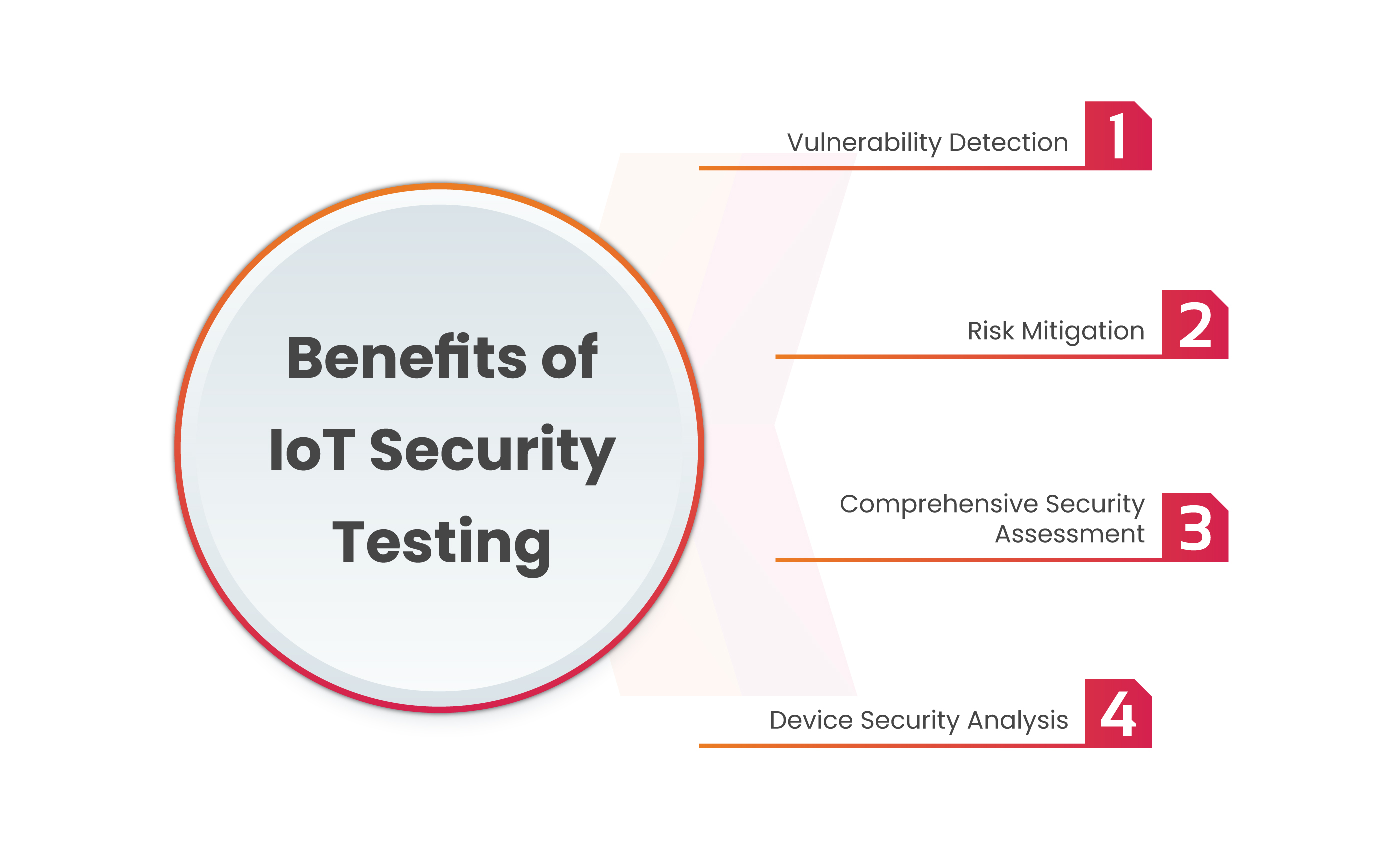
Benefits of IoT Security Testing
Vulnerability Detection
IoT penetration testing helps in the early detection of vulnerabilities in IoT devices, network architecture, or applications. By identifying these flaws before deployment or usage, organizations can proactively address and mitigate potential security risks.
Risk Mitigation
Organizations can understand the potential risks connected with their IoT infrastructure through safety testing. This knowledge enables the creation and application of threat mitigation strategies. This helps in reducing the likelihood and impact of security breaches.
Comprehensive Security Assessment
IoT penetration testing involves an evaluation of various aspects such as device hardware, firmware, software, communication protocols, and cloud services. This approach ensures a thorough assessment of the entire IoT ecosystem and provides insights into possible security gaps.
Device Security Analysis
Recognizing potential security risks with the device, such as open debug ports and holes in other embedded operating system components.
Best Practices for IoT Security Testing
The Internet of Things (IoT) places a high value on security, which has led to extensive study into designing and developing IoT-compatible designs and processes.
- Make sure to avoid default credentials
- Implement robust encryption methods for data storage and transmission
- Conduct IoT security testing
- Update, monitor, and effectively manage devices
Types of IoT Security Testing
IoT Penetration Testing
In IoT penetration testing, security experts identify and take advantage of security flaws in IoT devices. The security of your IoT devices is checked in the real world with IoT penetration testing. Under this, specifically, we mean evaluating the complete IoT system, not just the device or the software.
Threat Modeling
Threat modeling is a structured approach to identify, prioritize, and address potential risks, including vulnerabilities, for security measures. IoT security testing assesses threats, offering insights for security measures based on existing systems, likely attack methods, and target system analysis.
Firmware Analysis
Recognizing that firmware is a form of software akin to computer programs or applications is a fundamental concept. The unique aspect lies in its application within embedded devices, essentially compact specialized computers. These could include devices such as smartphones, routers, or even heart monitors. Analyzing firmware detects security vulnerabilities, like backdoors and buffer overflows, by extracting and examining the firmware.
Get in!
Join our weekly newsletter and stay updated
Why are businesses worried about IoT Security Testing?
Companies are concentrating on IoT security testing due to the significant implications of security in rapidly changing devices. Devices related to the Internet of Things (IoT) are vulnerable to several flaws, along with unauthorized access, statistics breaches, and cyberattacks. Any security breach can bring about massive monetary loss and damage to at least one’s recognition due to the fact these devices mechanically manage touchy and personal statistics, along with economic and health-associated facts in addition to getting the right of entry to privileges to houses and corporations.
Beyond financial losses, legal repercussions and compliance issues may arise if privacy regulations are violated. Maintaining the trust and confidence of customers is paramount, and a single security incident can erode years of hard-earned trust. Hence, robust IoT penetration testing is essential for identifying vulnerabilities, weaknesses, and potential exploits before adversaries do, enabling proactive measures to ensure a resilient and secure IoT ecosystem.
Book Your Free Cybersecurity Consultation Today!
Conclusion
It’s undeniable that the emergence of the Internet of Things has revolutionized many fields and changed the manner we interact with technology. However, this widespread integration raises a number of security troubles of its own. It is not possible to overestimate the importance of IoT protection due to the fact it’s critical for recognizing and stopping ability flaws that could be utilized by hackers.
Organizations may proactively secure their systems, safeguard sensitive data, and trust the dependability of IoT technology by utilizing thorough security audits, adhering to best practices, and regularly updating and monitoring IoT devices. In a world increasingly reliant on interconnected devices, investing in IoT security testing is an investment in a safer and more resilient digital future.
Organizations can prevent online threats by doing routine IoT security testing. Kratikal offers comprehensive cybersecurity solutions built to shield businesses from a range of cyber attacks, with a focus on protecting web applications from potential risks. Kratikal helps businesses find and fix security weaknesses before hackers can use them against them as a CERT-In-Empanelled company.









Leave a comment
Your email address will not be published. Required fields are marked *