
The ISO 27001:2022 standard for information security management systems (ISMS) is widely recognized. It is made to help businesses protect sensitive data. This helps businesses to ensure their confidentiality, integrity, and availability.
Table of Content
The Purpose of ISO 27001:2022
ISO/IEC 27001:2022 expands on the principles of its predecessor (ISO/IEC 27001:2013). It aimed to offer updated guidelines and criteria for Information Security Management. It tries to adapt to dynamic technological breakthroughs and changing business contexts. Providing updated rules and standards for the management of information security accomplishes this.
The COVID-19 pandemic has accelerated digital transformation and remote work. This prompts ISO/IEC 27001:2022 to address new concerns such as intensified cyber threats, remote workforce security, and integrating cybersecurity and information security measures.
Managing Threat Intelligence with ISO 27001
Threat intelligence is an essential component of cybersecurity. It is necessary for the detection, analysis, and reduction of a wide range of threats. Malware is also a part of such cyber risks. We cannot emphasize enough the significance of threat intelligence. Its incorporation and use in the context of ISO/IEC 27001:2022 makes it extremely essential.
Threat intelligence is a must within the framework of ISO/IEC 27001:2022. It not only supports the standard’s requirements, but it also improves an organization’s ability to secure its information assets. This is where threat intelligence comes in, allowing organizations to stay one step ahead of any cybersecurity attacks.
- Organizations are able to identify risks in their earliest phases through ongoing monitoring and the systematic collection of threat intelligence data.
- It helps to strengthen their defenses
- Be quick to react to malware outbreaks by comprehending the techniques, and practices used by hackers.
In alignment with its risk-based methodology, ISO/IEC 27001:2022 promotes implementing proactive measures, greatly strengthening them with the knowledge gained from threat intelligence. Furthermore, ISO/IEC 27001:2022 emphasizes the importance of having a clear incident response approach. When adequately featured, threat intelligence helps in the early detection of threats and gives valuable information for improving incident response strategies. Businesses can lessen the effects of cybersecurity incidents, protecting their sensitive data and upholding client’s trust.
Is Cloud Driving the Demand for ISO 27001:2022?
The increasing adoption of cloud computing has completely changed how companies operate. It has, however, raised more worries about security. As businesses work to secure their data in the cloud, being ISO/IEC 27001:2022 compliant is extremely vital.
Challenges relating to data protection, cybersecurity threats in borderless operations, regulatory compliance, etc. are brought about by this transition. Organizations may solve these problems with a structured strategy. This helps to make sure businesses can make use of the cloud’s advantages while protecting their sensitive data and complying with regulatory requirements.
ISO 27001:2022- Aligned Strategies for Malware Prevention
Some tactics businesses can work on for malware prevention:
Continuous Monitoring: Utilise real-time monitoring to keep an eye on your network for suspicious activity and malware signatures.
Incident Response Plan: Create a thorough incident response strategy that specifies steps for finding, containing, eliminating, and recovering from malware.
Employee Training: Inform employees of the value of cybersecurity cleanliness. You can achieve this by avoiding clicking on dubious links and refraining from downloading files from unreliable sources.
Patch Management: To limit vulnerabilities that malware can exploit, and keep software and systems updated with relevant security updates.
Network Segmentation: Segment your network in order to avoid the spread of malware.
Regular Backups: To ensure business continuity in the case of a malware attack, maintain regular backups of key data and test the procedures for their restoration.
Book a Free Consultation with our Cyber Security Experts

How to Get ISO 27001:2022 Compliant?
ISO/IEC 27001:2022 compliance requires an organized approach outlined below:
Risk Examination: To discover vulnerabilities, threats, and threats to the information assets of your organization, start with a thorough examination.
Policy Draft: Create comprehensive information security policies, processes, and guidelines that adhere to ISO/IEC 27001:2022 requirements and concepts.
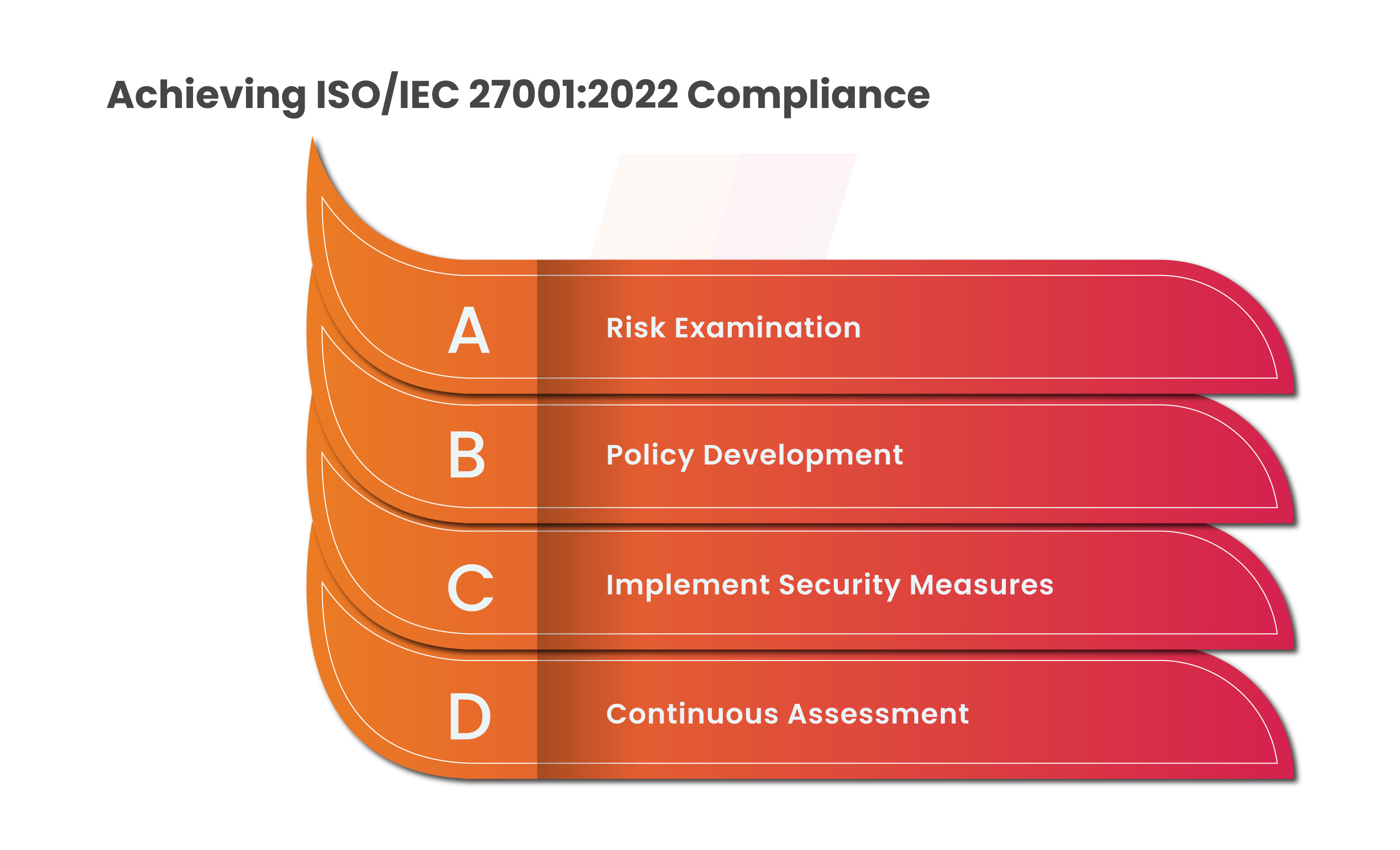
Implement Security Measures: Precautionary methods to preserve sensitive data and effectively reduce risks, such as technical controls, employee security training, and security protocols.
Continuous Assessment: Make sure your information security procedures are being used as designed by regularly monitoring and evaluating them.
In order to be compliant with ISO/IEC 27001:2022 standards and to respond to changing risks, regularly improve and optimize your information security operations.
How Kratikal Can Help Companies Be Secure and Compliant?
As a CERT-In empanelled auditor, Kratikal has the expertise to help businesses comply with ISO/IEC 27001:2022 and strengthen their cybersecurity posture. Our services can assist you with:
- Kratikal carries out in-depth analyses to determine whether your company is prepared to comply with ISO/IEC 27001:2022.
- Analyze your present information security framework for gaps and vulnerabilities to provide a roadmap for improvement.
- Help in developing policies and processes for information security in accordance with ISO/IEC 27001:2022 standards.
- To lessen security threats associated with people, provide employees with security awareness training.
- Your ability to recognize and respond to malware will increase if you incorporate threat intelligence into your security strategy.
- Create and enhance incident response plans to address malware issues and other security-related issues.
Is your company secure in a world where cyber threats are a serious concern? By becoming ISO 27001 compliant, you may take the first step towards protecting your digital assets.

