
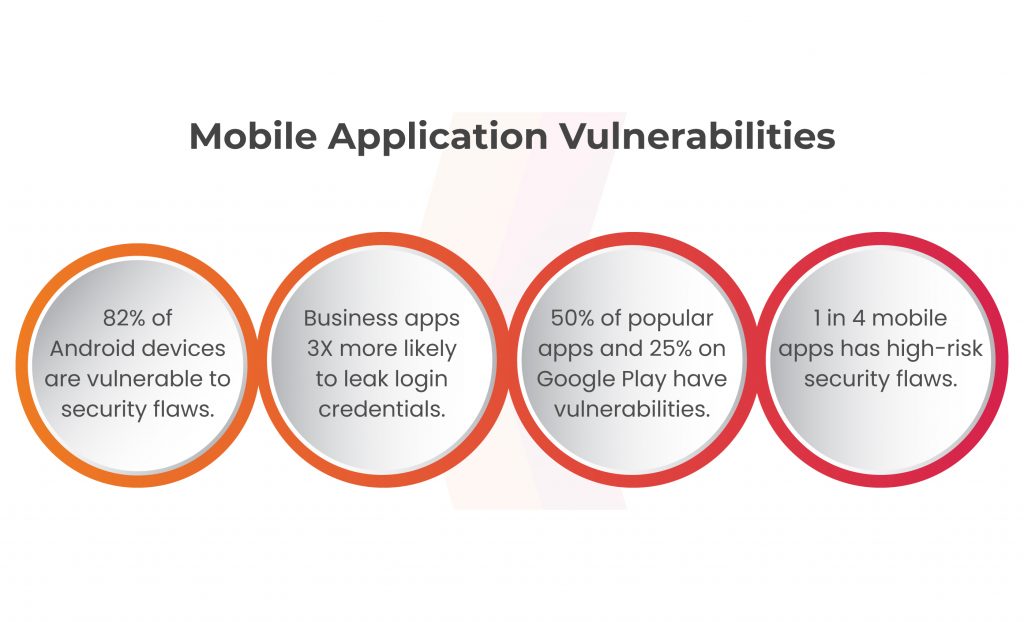
82% of Android devices and 38% of iOS devices have security vulnerabilities. Furthermore, business apps have a threefold higher chance of leaking sensitive login credentials than average apps. These findings highlight the immediate need for enhanced security measures, as one in four mobile applications contain high-risk security flaws. Mobile application testing is crucial to address these vulnerabilities and protect businesses from potential cyber-attacks.
Mobile application testing is now essential for increasing productivity, optimizing processes, and interacting with consumers in today’s digitally linked business environment. However, the prevalence of harmful mobile apps puts organizations at risk by risking private information, operational integrity, and client confidence. Organizations must prioritize mobile app testing to safeguard operations and businesses from cyber-attacks. The blog emphasizes the importance of mobile app testing for organization’s security.
Table of Content
Android vs iOS- Understanding Mobile App Security Issues
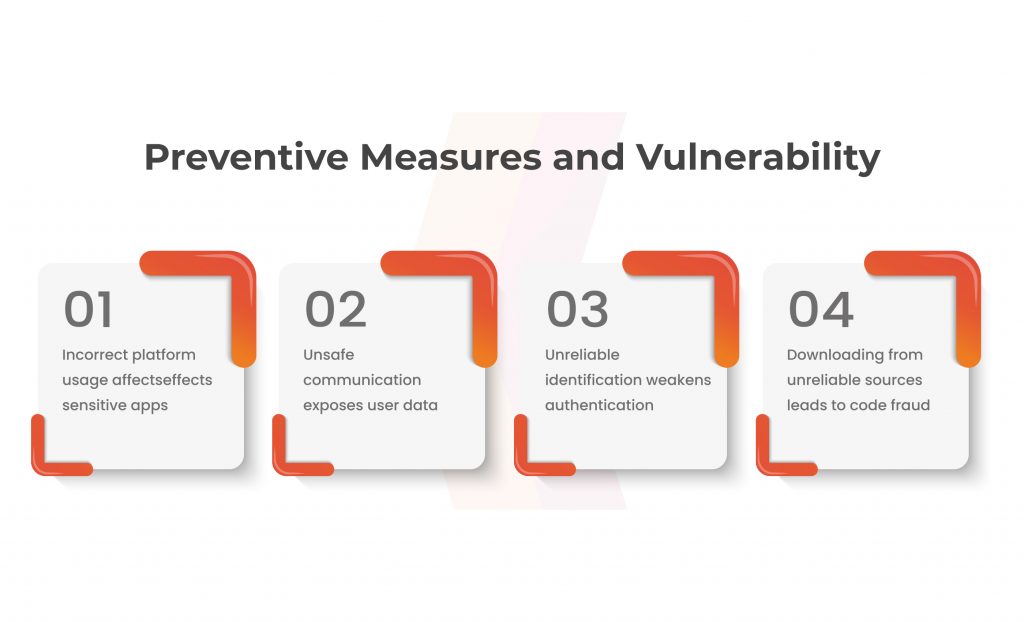
App developer’s security negligence can’t be entirely ruled out, though it may not be accurate to argue. The inadequate security infrastructure of these apps may be a contributing factor to the rising number of mobile app hacks. Now, the process for developing and releasing Android apps differs slightly from that of iOS. Because of this, each of these constructions has unique safety issues.
Android App Security Issues
According to statistics on mobile app hacking, Android apps suffer greater damage than iTunes ones. A major contributing reason to this is Android’s open-supply nature. The open-source nature of Android allows for unlimited usage and source code modification for the enhancement of apps.
Android’s OS app review process has led to a proliferation of threatening mobile apps due to inadequate screening and testing.
Significant security flaws in Android applications include
- Man in the middle attacks (MITM)
- Accounts takeover through unauthorized individuals
- Unauthorized access of applications’ data
- Leaking sensitive information of the user
Significant security flaws in iOS
Due to their controlled development environment, iOS apps are often more secure than Android apps. Additionally, due to Apple’s thorough software review procedure.
Despite this, it is erroneous to think that iOS apps are secure. According to market share statistics, the affluent segment uses the iOS operating system more frequently, which makes it a prime target for hackers. In actuality, iOS has not succeeded in thwarting the attacks despite the security checks and isolated environment. Numerous iOS apps, devices, and other pieces of data have been compromised.
iOS Apps with significant security flaws include
- Preserving data locally on the device
- Jailbreaking
Testing the Security of Mobile Applications as a Solution
Mobile application security testing serves as a crucial solution to address the growing concerns of app vulnerabilities. Security testing helps developers identify and mitigate risks in mobile applications proactively. The process involves various techniques such as:
Vulnerability Assessment
To uncover any possible flaws or vulnerabilities in the program, it is essential to assess the infrastructure and security measures in place.
Penetration Testing
As implied by its name, this process entails leveraging the vulnerabilities identified during the vulnerability assessment to evaluate the potential extent of a hack through those vulnerabilities.
In simpler terms, vulnerability assessment (VA) identifies the vulnerabilities, while penetration testing (PT) provides a comprehensive understanding of their severity.
Testing Mobile Apps to Protect Business Interest
Ensuring the security and functionality of mobile apps is essential for protecting business interests and maintaining a positive user experience. By prioritizing mobile application testing, organizations can identify and address potential security holes, enhance data security, and deliver a flawless user interface. Through practices such as penetration testing, vulnerability assessments, and code reviews, businesses can locate flaws and safeguard their apps against emerging threats.
Mobile application testing also offers benefits like time savings through automation, verification of app functionality and usability, elimination of errors, and enhanced market reputation and client loyalty. Here are some of the methodologies which are followed:
Black Box
A kind of software program checking out technique known as “black box,” occasionally referred to as “behavioral testing” or “outside testing,” doesn’t require the tester to have any prior expertise of the code structure, implementation information of an utility. It is fully reliant at the wishes and specs of the software and concentrates at the enter and output of the software.
Gray Box
A software testing strategy called grey box testing, which mixes black box and white box testing, is used to test an application without having a complete grasp of its source code. It looks for and finds mistakes that have been caused by the application’s bad code structure.
Conclusion
In the dynamic business landscape, where mobile apps play a pivotal role in driving growth and success, the threat posed by vulnerable mobile apps cannot be ignored. Organizations must prioritize mobile application testing to protect their operations, customer data, and brand reputation. Kratikal offers mobile application services along with other services such as secure code review service, web application testing, cloud penetration testing and IoT. We are a CERT In empanelled organization committed to offering cyber security solutions to companies that attempt and require to improve their mobile application testing.
By investing in comprehensive testing practices, businesses can fortify their security defenses, minimize potential risks, and foster a safe and trustworthy digital environment. With mobile application testing as a cornerstone of their cybersecurity strategy, businesses can confidently navigate the digital landscape and ensure sustained success.


