
The internet is vital in our digital age, offering unmatched connectivity and convenience in daily life. But the internet hides a secret world known as the Dark Web behind its surface. It becomes a place for illegal activities and spawns cyber threats that impact global organizations significantly. In this blog, we’ll understand the other side of the internet and explain how the mysterious Dark Web poses risks to businesses.
Table of Content
Understanding Dark Web
The dark web are websites that are inaccessible to standard search engines like Google. Instead, to access these networks anonymously, users must use specialized software such as Tor (The Onion Router). It has become a popular destination because of the umbrella of anonymity for buying and selling hacking tools.
Since it offers a platform for anonymous communication and transactions, it is frequently linked to illicit activity. Because fraudsters use it to acquire and sell malware, hacking tools, and stolen data, the Dark Web has grown to be a serious threat to SMBs.
What role does Dark Web Play in Data Breaches?
The Dark Web is hackers’ go-to platform to monetize stolen data, evade law enforcement, and sustain the data breach ecosystem.
In the event that there is a data breach, hackers may sell the stolen information on numerous dark web markets and forums. Tor simplifies market access using encrypted networks, ensuring anonymity for buyers and sellers, facilitating secure transactions. As a result, hackers are able to commit illegal acts without disclosing their true names, hence lowering the possibility that their true identities could be discovered.
Organizations need proactive cybersecurity with regular assessments, employee training, and advanced threat detection to thwart dark web involvement in breaches. Crucial collaboration among law enforcement, cybersecurity experts, and private stakeholders is vital to thwart cyber threats and protect data.
How threat Actors Sell Data on Dark Web?
The forums are most used to sell online data, passwords, and organization PII. Because of anonymity, security, and hard-to-take-down sites, threat actors have started using forums more often.
Unlike the surface web (where you can use Google to search for content, text, file, or images), the dark web, it’s the invite only. Access to the site requires a link or invitation from the owner, ensuring exclusivity and security for authorized participants. This makes it hard for normal people to find or track if there’s any data breach activity happening online. That’s why organizations need security professionals to investigate the attack as they have the expertise to understand the root cause of the breach.
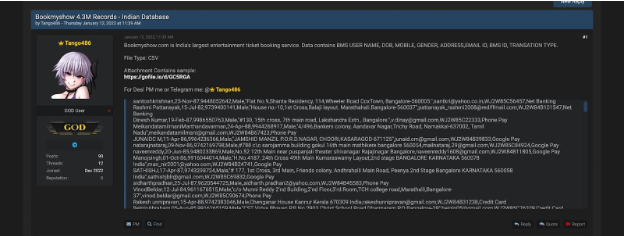
( Threat actor selling data on the hacking forum )
How can VAPT Services prevent Dark Web Threats?
In the ever-changing landscape of cybersecurity threats, Vulnerability Assessment and Penetration Testing (VAPT) services play a critical role in safeguarding organizations against the dark web’s lurking. Integrating VAPT services into cybersecurity plans empowers organizations to bolster defenses and combat threats effectively. Let’s look at how:
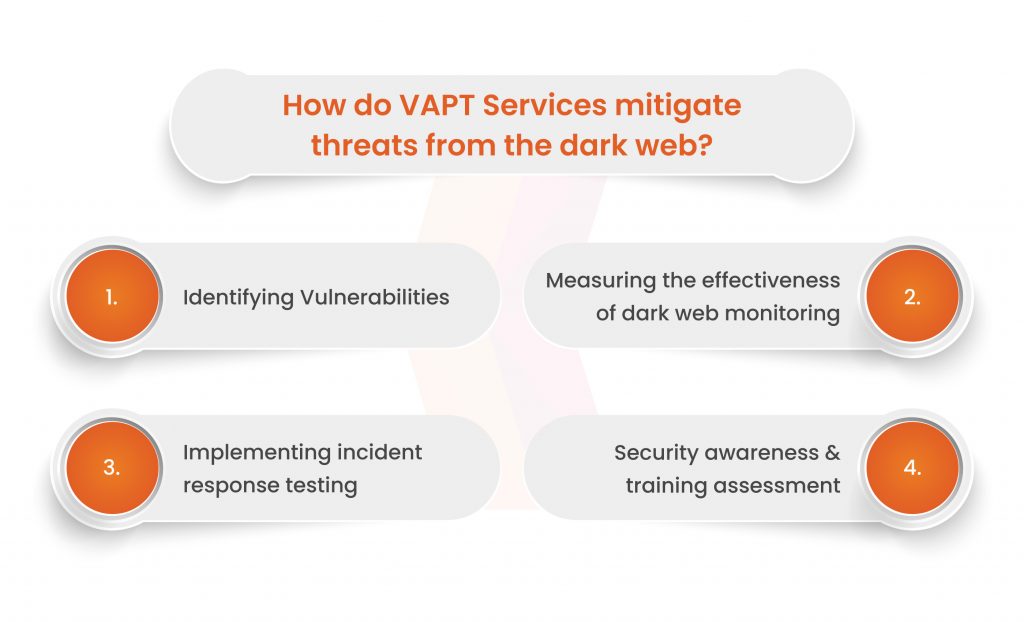
Identifying Vulnerabilities
VAPT services entail cybersecurity experts scanning organization’s infrastructure to detect vulnerabilities exploited by hackers. By proactively discovering and patching these vulnerabilities, organizations can prevent unauthorized access to sensitive data and avoid potential data breaches.
Evaluating Dark Web Monitoring Effectiveness
Organizations that leverage VAPT can access the effectiveness of the monitoring efforts. By simulating attacks that may originate from the dark web, penetration testers can evaluate how well an organization’s security systems detect and respond to potential threats. This allows organizations to fine-tune their monitoring capabilities and enhance their response mechanisms.
Testing Incident Response
Penetration testing, a critical component of VAPT services, involves simulating cyberattacks, including those that may have originated from the dark web. This enables organizations to evaluate the effectiveness of their incident response and business continuity plans in dealing with potential threats. By identifying gaps and vulnerabilities, organizations can better prepare for and mitigate the impact of actual attacks.
Assessing Security Awareness and Training
VAPT services extend beyond just technological evaluations. They can also assess an organization’s employees’ security awareness and training. This aspect is particularly relevant in combating insider threats, wherein employees may be enticed to collaborate with hackers. VAPT can help organizations strengthen their security culture, reduce the risk of insider threats and improve overall cybersecurity hygiene.
Conclusion
The Dark Web presents substantial risks, hosting illegal markets and enabling cyber threats, as hackers trade stolen data and malware. To combat these threats, organizations can leverage Vulnerability Assessment and Penetration Testing (VAPT) services. Along with other services like secure code review, online application testing, cloud penetration testing, and IoT, Kratikal also provides cybersecurity services. We are a CERT In accredited company dedicated to providing cyber security solutions to businesses that want to and need to increase their cybersecurity.
VAPT helps identify vulnerabilities, evaluate and monitor effectiveness, test incident response plans, and assess security awareness and training. By integrating VAPT services into their cybersecurity strategies, organizations can proactively mitigate the risks associated with the Dark Web and protect their valuable business data.

