API Attacks have become common these days in the cyber world. APIs (Application Programming Interfaces) have become an essential element of contemporary software development. In today’s advanced world, facilitating seamless communication and integration across various programs and systems is equally necessary for businesses. However, as APIs have been more widely used, likewise the API attacks have rocketed.
The top API Attacks in 2023 will be covered in this blog post. Along with insights into how identifying and mitigating these attacks is essential. This is done for maintaining strong API security measures and protecting sensitive data from malicious hackers.
Table of Contents
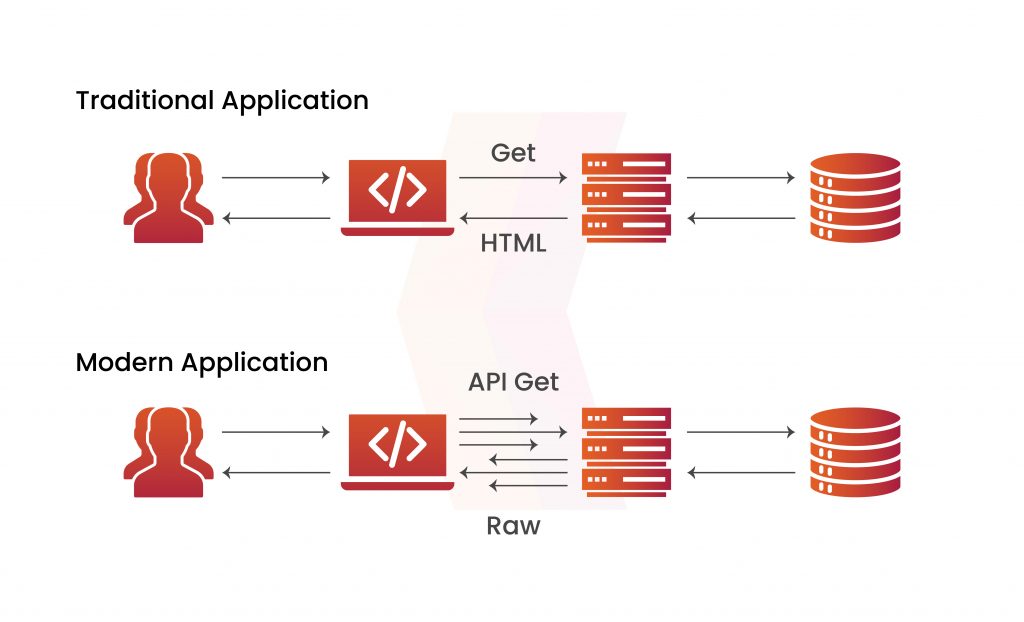
Web Application Testing v/s API Testing
API testing checks the accuracy and dependability of application programming interfaces. This is done to ensure seamless data interchange and integration between software systems. Web Application Testing focuses on verifying the user interface and functioning of a web-based application. Both are crucial for the overall performance and quality of the application.
1. Broken Object Level Authorization
Object-level authorization is an essential security strategy. It is used to limit access to specific application objects. It helps to make sure that only people with permission can access and modify sensitive data. However, inadequate implementation of object-level authorization can expose vulnerable areas in critical processes.
By manipulating API requests, unauthorized users can take leverage from this flaw. They can get access to sensitive information or carry out unethical deeds. Unauthorized parties made API queries including customer phone numbers to Uber. This has been a major provider of ride-hailing services, in one significant instance associated with this vulnerability. Implementing strong protocols and rigorous authorization checks serves to reduce this risk and ensure the integrity of API security, preventing attacks.
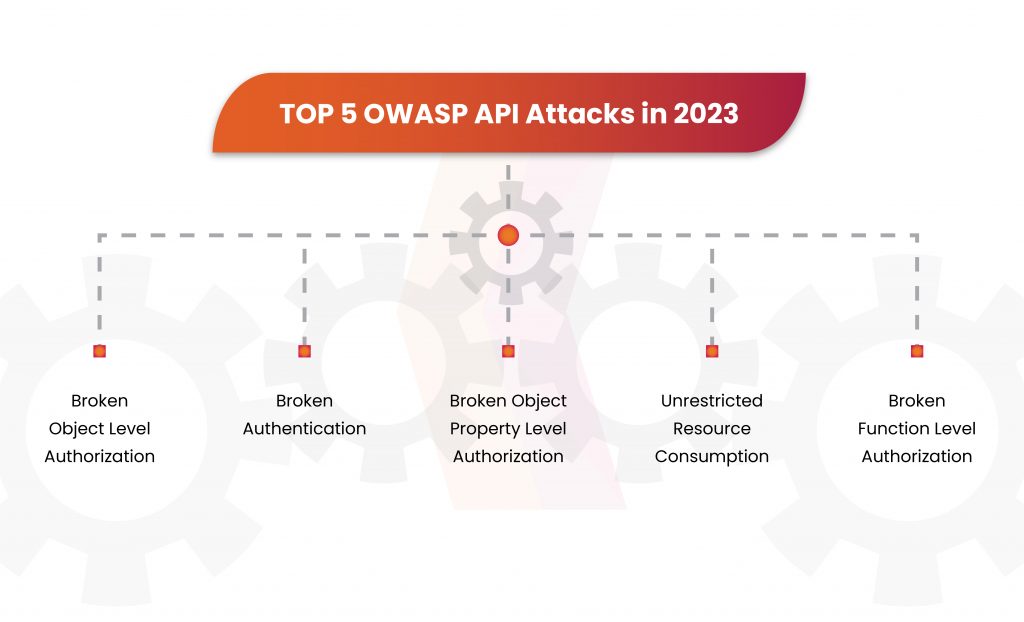
2. Broken Authentication
Authentication endpoints serve as the front door for users to access APIs securely. However, attackers often target these endpoints in an attempt to gain unauthorized entry. Weak encryption keys, ineffective password policies, inadequate session management, and improper implementation of authentication mechanisms can all contribute to broken authentication vulnerabilities.
Effective exploitation of these vulnerabilities can compromise user accounts and lead to unauthorized access to private information. To stop attackers from taking advantage of these vulnerabilities, developers, and organizations must give top priority to implementing robust cybersecurity protection measures. These can be for instance multi-factor authentication and secure credential management.
Get in!
Join our weekly newsletter and stay updated
3. Broken Object Property Level Authorization
APIs often need to validate user access to specific object properties. This action aims to prevent unauthorized users from accessing and modifying sensitive data within objects. However, the improper enforcement of authorization at the object’s property level can enable attackers. The attackers try to read, modify, add, or delete object property values that should be restricted.
Failing to validate user access to both objects and their properties opens the door for malicious actors to exploit these vulnerabilities, potentially leading to unauthorized data exposure or system manipulation. Developers must implement rigorous validation protocols and regular security audits to ensure comprehensive object property-level authorization. This would maintain the confidentiality and integrity of sensitive data.
4. Unrestricted Resource Consumption
APIs make it simple for systems and applications to communicate with one another. If this interaction isn’t adequately managed the attackers might use it to overflow APIs with requests. This could result in Denial of Service (DoS) attacks. The economy, one’s reputation, and the accessibility of services can all suffer from unchecked resource use.
For instance, a payment gateway API that charges based on the number of requests processed can suffer financial losses. If it is attacked by malicious actors and generates a high volume of submissions. Organizations should implement measures such as execution timeouts, request limits, and resource usage monitoring to prevent and identify unusual activities. These unusual activities may indicate DoS attacks and protect their APIs from resource exhaustion.
Book Your Free Cybersecurity Consultation Today!
Function-level authorization vulnerabilities occur when users access administrative endpoints and execute sensitive actions because they lack authorization. Attackers exploit these vulnerabilities by identifying flaws in APIs and sending legitimate API calls to endpoints that they don’t have access to.
These security gaps often arise due to inadequate monitoring of user roles, insufficient handling of hierarchical access controls, or incomplete user access verifications. For the objective of preventing unauthorized access and preserving the security and integrity of APIs, it is essential to provide strong function-level authorization mechanisms, conduct regular access reviews, and continuously monitor the identities of users.
Conclusion
Recognizing and mitigating API attacks is essential for developers and organizations looking to preserve the confidentiality, integrity, and availability of sensitive data as the use of APIs increases. By prioritizing the mitigation of these top 5 API attacks discussed in this blog post – Broken Object Level Authorization, Broken Authentication, Broken Object Property Level Authorization, Unrestricted Resource Consumption, and Broken Function Level Authorization – developers can strengthen API security measures and protect sensitive data from potential breaches.
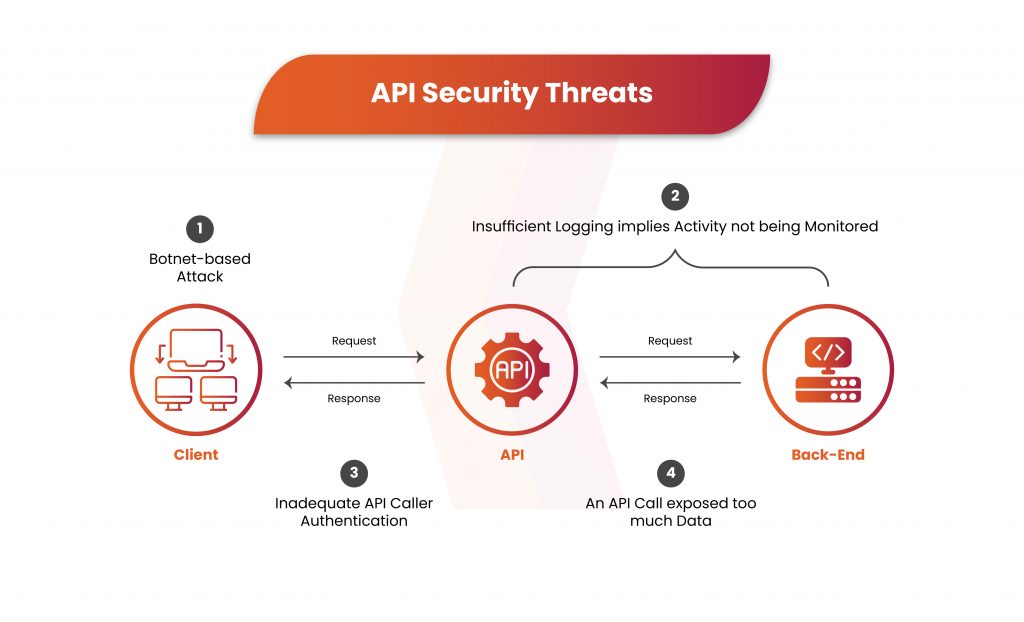
Organizations can count on Kratikal’s experience and solutions to improve their API security to meet the top 5 API vulnerabilities in 2023. Leading CERT-IN empanelled cybersecurity company, Kratikal provides thorough API security audits and VAPT solutions to pinpoint vulnerabilities and successfully counter possible hackers. Our skilled team can assist businesses with setting up reliable monitoring and logging systems, frequent security audits, and strong authentication and authorization procedures.
Staying updated on the latest security best practices, implementing robust authentication and authorization mechanisms, and implementing comprehensive monitoring and logging systems are essential steps in ensuring the security of your API ecosystem. By addressing these API attacks head-on, organizations can foster trust, protect user data, and ensure the integrity of their applications and systems amidst the evolving cyber threat landscape.








Leave a comment
Your email address will not be published. Required fields are marked *