Modern web applications often have a function called “file add” that permits users to upload files from client apps to the server. While this option is essential for packages that rely on consumer-generated content. If used effectively, will also pose risks to capacity protection. Web application testing is vital to identify and mitigate threats. VAPT services ensure comprehensive cybersecurity for app security. This blog will explore file upload vulnerabilities, their potential effects on web application testing, and practical mitigation techniques.
Table of Content
Unregulated File Upload Vulnerabilities
Uploaded files pose a significant threat to applications, often serving as a starting point for attacks. Attackers aim to introduce code into the targeted system, which then needs execution. Allowing file uploads facilitates this initial attack phase.
Uncontrolled file uploads can result in system takeover, data overload, backend and client-side attacks, and defacement. Outcomes hinge on how the application handles uploaded files and where they are stored.
The two main issues that arise are:
- File metadata, such as path and name, often from sources like HTTP multipart encoding, can deceive the application into harmful actions, like overwriting vital files or improper storage. Rigorous validation of metadata is essential.
- Risks here depend on the file size or content along with file usage. To prevent such attacks, thoroughly assess all file-related actions within your application, considering involved processes and interpreters.
Impact of File Upload Vulnerabilities OnWeb ApplicationTesting
Web application testing is crucial in identifying and mitigating file upload vulnerabilities. Security experts must thoroughly examine the file upload functionality to ensure that all possibilities are addressed. Comprehensive testing involves assessing the application’s handling of different file types, sizes, and content. Special attention should be given to cases where the server attempts to parse or execute uploaded files. By integrating file upload testing into the overall security assessment, developers can identify vulnerabilities before malicious actors exploit them.
In the worst case, because the file’s type wasn’t properly validated, the server configuration allows some file types (like.php and.jpg) to be executed as code. In this scenario, a server-side code file that serves as a web shell might theoretically be uploaded by an attacker, giving them complete control of the server.
Book a Free Consultation with our Cyber Security Experts

Benefits Of VAPT Testing in Web Application Security
Strong online security procedures are crucial due to the serious consequences of uncontrolled file uploads. Services for Vulnerability Assessment and Penetration Testing (VAPT) are useful in this situation. VAPT testing can be used to identify, assess, and mitigate vulnerabilities in web applications, networks, and systems.
- VAPT Testing offers a thorough study and evaluation of networking infrastructure, web/mobile apps, and both.
- Secures sensitive data and information from theft, unauthorized access, and data breach.
- Identify the infrastructure’s vulnerabilities and errors that could result in cyberattacks.
- Provides the company with a better reputation by offering a secure data network.
- Safeguards companies from loss of money and reputation.
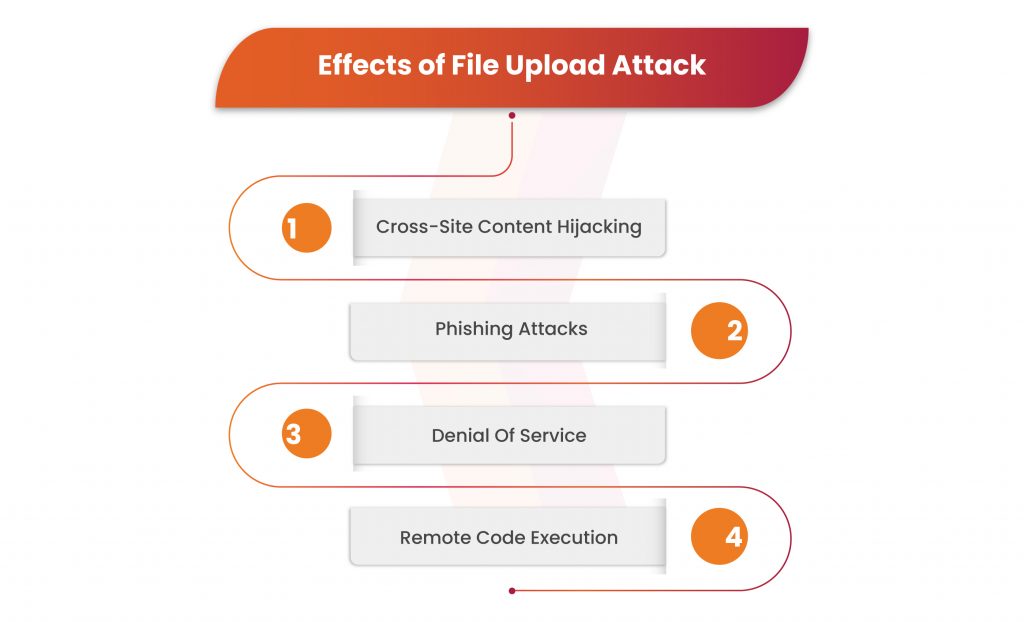
Effects Of File Upload Attack
A file upload vulnerability is a popular target for hackers due to its simplicity of use and potential for different malicious actions. Effects of file upload attack include:
Cross-Site content Hijacking
Occurs when attackers exploit susceptible server instances, enabling them to replace authentic web pages with their content.
Phishing Attacks
Hackers employ harmful scripts to deceive users and acquire confidential information illicitly.
Denial Of Service
If the application neglects to verify the quantity and dimensions of uploaded files, malicious actors can flood disk storage, overburdening the server’s responsiveness to client demands.
Remote Code Execution
Exploiting file upload commands, hackers upload web shells that grant them the ability to execute unrestricted commands on the application server.
Prevention Of File Upload Vulnerabilities
Unrestricted document uploads can serve as a backdoor for hostile actors to exploit weaknesses, compromise sensitive information, and cause havoc with the integrity of an application. A thorough approach to prevention is essential to fortifying the defenses against those cyber threats. Here are effective strategies to prevent file upload vulnerabilities and ensure the robust security of web applications.
Implement Strict Validation
Web applications should validate both the content and metadata of uploaded files. Verify that the file type matches the expected format and that the file size is within acceptable limits. Additionally, utilize whitelists to specify allowed file extensions, preventing users from uploading potentially harmful file types, such as executable files or scripts.
Store Uploaded Files
Implement a secure file storage mechanism to prevent unauthorized access to uploaded files. Store files outside the web root directory to avoid direct URL access. Apply access controls and encryption to safeguard sensitive files, ensuring that even if an attacker gains access to the server, the stored files remain protected.
Rename Uploaded Files
Assign a unique and random name to uploaded files to prevent predictable naming that could potentially be exploited by attackers. Renaming files can thwart attempts to manipulate the file’s content or execute malicious code by taking advantage of the filename.
Disable Risky File Types
Consider disabling certain high-risk file types, such as executable files (.exe) and script files (.php, .js), from being uploaded. While this may impact legitimate user activities to some extent, it significantly reduces the attack surface and potential for exploitation.
Conduct Regular VAPT Testing
Regularly conduct security testing, including Vulnerability Assessment and Penetration Testing (VAPT) services, to proactively identify and address vulnerabilities, including file upload vulnerabilities. VAPT services simulate real-world attacks to uncover vulnerabilities in your web application security defenses.
Conclusion
Allowing unauthorized report uploads in web programs can have serious negative effects on reputation, statistics loss, and safety. The process of vulnerability assessment and penetration testing (VAPT), which helps identify and address such flaws, is essential. Utilizing VAPT services allows agencies to strengthen their security posture, respond proactively to capabilities threats, and provide users with a safe and dependable online experience.


