WAF (Web Application Firewalls) is an essential component of any secure network infrastructure. They are designed to protect a network from external threats such as unauthorized access, malware, and other malicious attacks. WAF works by analyzing incoming and outgoing traffic, and by identifying traffic patterns web application firewalls allow or block traffic.
One popular WAF that many websites use is Cloud Flare. Cloud flare is a content delivery network (CDN) that provides security services to websites by acting as a proxy between the website and its visitors. It offers protection against various types of attacks, including Distributed Denial of Service (DDoS) attacks, and helps to speed up website loading times. While Cloud Flare is a powerful security tool, it is not foolproof, and there are ways to bypass it.
In this blog, we will explore some techniques used to bypass Cloud Flare and gain unauthorized access to a website. We will examine the various methods used by attackers to bypass Cloud Flare and the steps that website owners can take to protect their websites from these attacks.
Table of Contents
Get in!
Join our weekly newsletter and stay updated
TECHNIQUES USED TO BYPASS CLOUDFARE
- Using Shodan Query
The Shodan search engine allows users to find internet-connected devices and systems. By searching for specific keywords or phrases, users can uncover websites, servers, and other devices that may be publicly accessible.
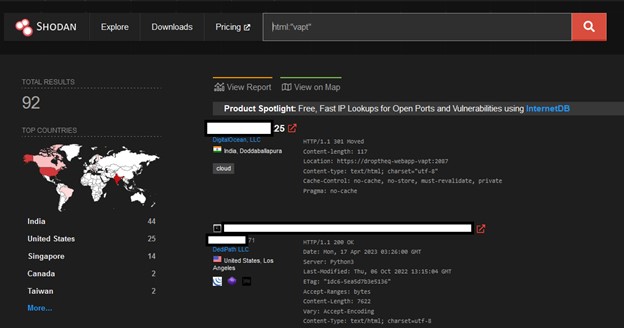
One technique for bypassing Cloud Flare’s protections is to use the Shodan search query HTML:”title of the page” to find the origin server IP address of a website protected by Cloud Flare. By using a Shodan query that looks for the HTML title of the page, it may be possible to find the website’s origin server IP address, even if it is behind a Cloud flare proxy.
Once the origin server IP address is identified, it can be used to directly access the website, bypassing Cloud Flare’s protections. This can be useful for conducting further reconnaissance or launching attacks that may be blocked by Cloud Flare’s defenses.
For example, As Per the below image, html:”VAPT” is used in the Shodan query that will show all the website’s real IPs hidden behind Cloud Flare.
2. Using Censys search
Censys.io uses a variety of scanning techniques to gather data about devices and networks, including port scans, TLS handshakes, and HTTP requests. This data is then analyzed to identify the operating system, software, and services running on each device, as well as to determine the security posture of the device or network.
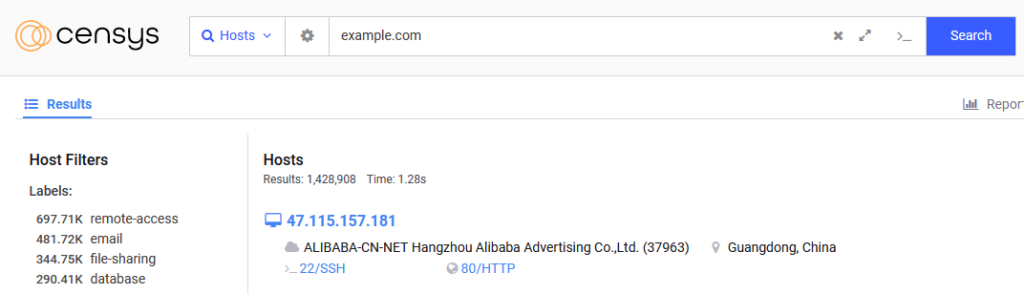
The attacker just needs to enter the domain name in the search.censys.io search and it will show all the resulting IPs associated with that specific domain.
Please find below the screenshot where the target domain name and censys are revealing the real IP of the website.
3. Searching subdomain
The other hosting IPs for the target domain can also be obtained by performing subdomain enumeration. This will also reveal the target domain’s true IP address, which is concealed by Cloudflare.
There are several ways to collect the subdomains of a website, and in our situation, we may accomplish so by using the open-source program Knockpy.
Simply begin with Knockpy target.com, and you will get a list of subdomains along with the IP address where they are hosted.
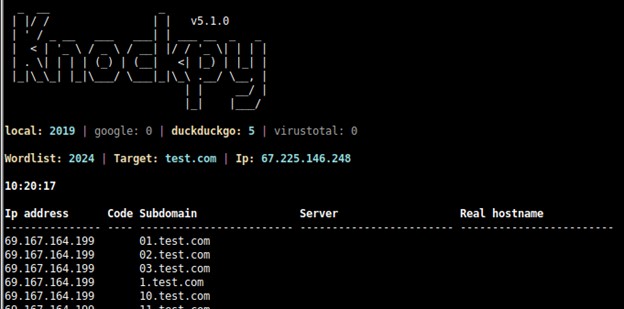
The screenshot above illustrates a WAF bypass exploit where test.com is used to check for subdomains but not real sites. An attacker must check to see if any subdomains have a server name other than Cloudflare and a code 200 status.
In addition, a threat actor may employ this attack technique using an online subdomain enumeration tool.
Even yet, threat actors use a variety of various methods to carry out these types of attacks. Defenders can also stop it using a variety of techniques.
For example
- Regularly Audit your web application: This assists to gain a better understanding of the attack surface of your websites.
- Use Cloud flare’s “I’m Under Attack” mode: This mode requires visitors to solve a challenge, such as a CAPTCHA before they can access the website. This can help to block automated attacks that might be used to uncover the real IP address of the website.
- Hide DNS Information: To disguise your DNS information, use a different service. This can be achieved by employing WHOIS privacy protection, which will stop attackers from discovering your website’s IP address by performing a DNS lookup to discover the genuine IP address.
- Reverse Proxy: Setting up a reverse proxy will make the traffic route from an additional server before it reaches your website. This will create an additional layer of security from attacks that try to get the real IP of a website.
Get in!
Join our weekly newsletter and stay updated
How Kratikal can help to prevent such web application attacks?
We learned that merely installing a firewall won’t shield you from cyberattacks and data leaks. Certainly, they can decrease the attack surface, but they won’t help you stop these attacks as much as regular network and web app security audits, threat modeling, and web app penetration tests.
Kratikal’s cybersecurity solutions can be effective in protecting organizations from various types of cyber attacks, including those aimed at bypassing Web Application Firewalls like Cloudflare. By using tools and techniques such as vulnerability assessments, penetration testing, and security audits,
Kratikal, a CERT-In Empanlled organization can help organizations identify and address weaknesses in their security posture before they are exploited by attackers. Additionally, Kratikal’s expertise in implementing advanced security measures such as reverse proxies, DNS protection, and two-factor authentication can help organizations stay ahead of the evolving threat landscape and ensure that their data and infrastructure remain secure.
With Kratikal’s comprehensive cybersecurity solutions, organizations can minimize the risk of cyber-attacks and ensure that their business operations are protected against any potential threats.









Leave a comment
Your email address will not be published. Required fields are marked *