In an era dominated by rapid technological advancements, the realm of cybersecurity and network penetration has taken on an increasingly paramount role. Central to this multifaceted defense strategy is Network Security Testing, which stands as a reliable bulwark against the surging tide of digital threats. This proactive approach involves meticulous and exhaustive analysis of an organization’s network infrastructure. This reveals potential vulnerabilities and points of entry that malicious actors might exploit. The imperative significance of network security testing reverberates across the cybersecurity landscape. This underlines its multifaceted and dynamic efficacy in safeguarding sensitive digital assets.
As the digital landscape continues to evolve, the need for preemptive measures to anticipate and thwart emerging network security threats becomes paramount. The accelerated sophistication of hackers’ tactics necessitates proactive strategies to ensure the continued safety of critical data repositories. The strategic deployment of network security testing assumes an increasingly vital role in addressing this need. This stands as a sentinel against evolving penetration threats.
Table of Contents
Deconstruct Network Penetration Testing: Ethical Hacking’s Power
Network Penetration, in its essence, encapsulates the proactive establishment and vigilant maintenance of an array of defenses designed to fortify an organization’s IT infrastructure against a spectrum of cyber incursions. This multifaceted approach encompasses various techniques, such as network segmentation, Data Loss Prevention (DLP) mechanisms, firewalls, Intrusion Prevention Systems (IPS), and more. However, as hackers harness progressively sophisticated methodologies, organizations must extend their countermeasures to match these advancements. Among the arsenal of defensive techniques, Network Penetration Testing emerges as a tactical centerpiece.
Network penetration testing, often synonymous with ethical hacking, unfolds as a meticulously orchestrated simulation of authentic cyberattacks. Accomplished experts are adept at the intricacies of hacking endeavors and undertake controlled attempts to breach the network’s security infrastructure. This wields the same tools, techniques, and methodologies deployed by malevolent agents. This simulated incursion serves a dual purpose: to unveil latent vulnerabilities and devise strategies. This will reinforce the network’s robustness against potential breaches. Organizations can find and fix weaknesses early, reducing the chance of being exploited by bad actors.
Get in!
Join our weekly newsletter and stay updated
Mitigate the Complex Landscape of Emerging Threats
The contemporary cybersecurity landscape is interrupted by numerous new cyber threats, each demanding meticulous attention and deft countermeasures. Delving into this intricate milieu, we explore the key security strategies that encapsulate the core of cyber resilience:
1. Phishing Attacks
Evolving beyond conventional email-based vectors, modern phishing attacks have metamorphosed into sophisticated endeavors encompassing “smishing” (text message-based) attacks and social media-based stratagems. To counter these threats, organizations must deploy robust email filters while consistently educating their workforce about discerning scams across diverse digital platforms.
2. DDoS Attacks
Distributed Denial of Service (DDoS) attacks have the potential to incapacitate websites, precipitating crashes or significant disruptions. The underlying mechanism involves hackers commandeering a network of compromised devices, subsequently orchestrating a deluge of requests that overwhelm the target’s infrastructure. The complex task of segregating legitimate traffic from compromised data amplifies the challenge.
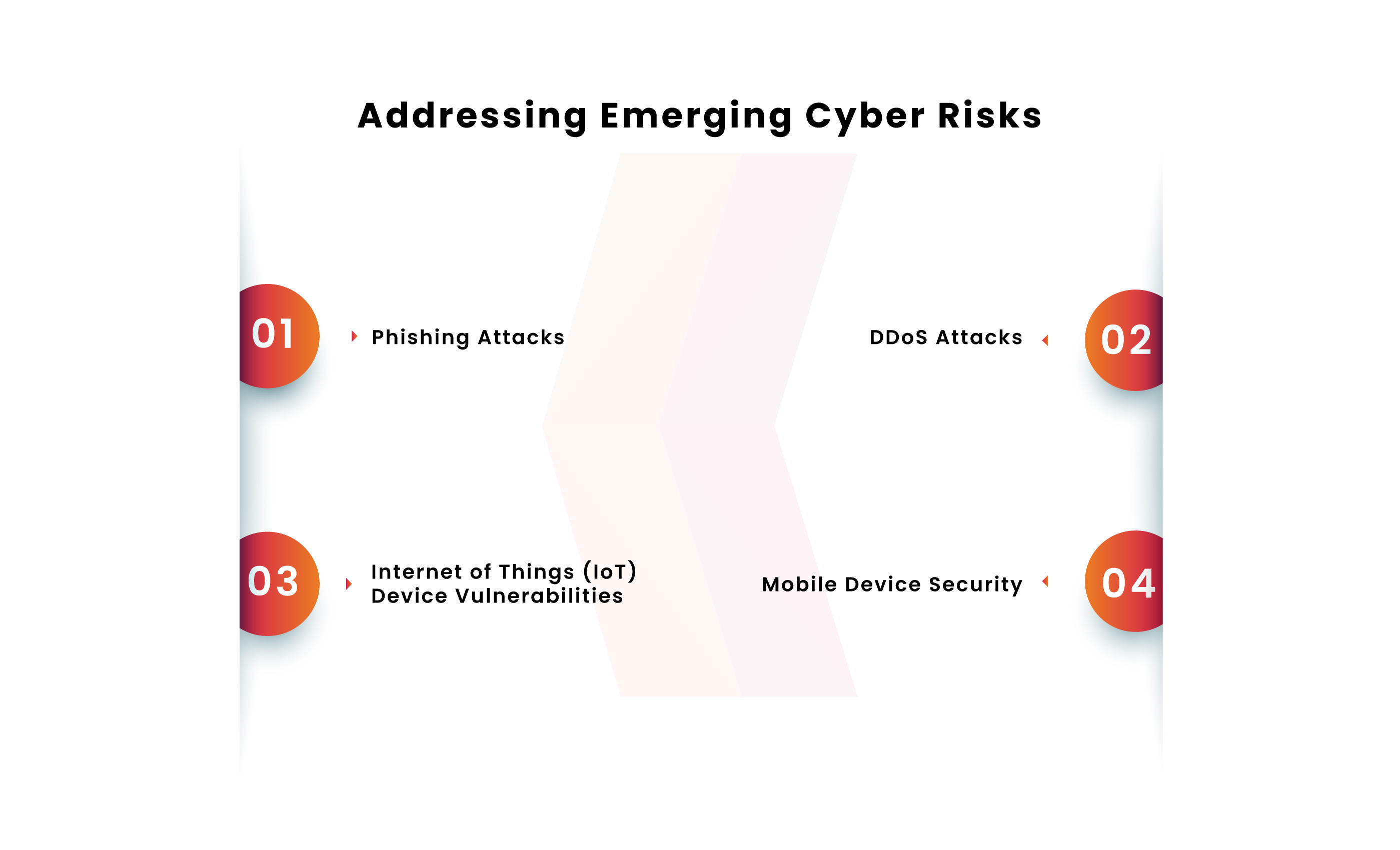
3. Internet of Things (IoT) Device Vulnerabilities
The rapid proliferation of IoT devices introduces a host of cybersecurity vulnerabilities. Consistent assessment of the security of these devices is crucial in preempting potential breaches. Ensuring up-to-date firmware and integrating devices into secure network environments are pivotal measures.
4. Mobile Device Security
With mobile devices becoming increasingly integral to organizational workflows, they emerge as lucrative targets for cyber attackers. Imposing stringent security protocols for mobile devices – encompassing regular updates, secure app installations, and robust encryption – constitutes an effective countermeasure.
Book Your Free Cybersecurity Consultation Today!
Elevating Network Penetration Testing: Blueprint for Resilience
To truly fortify defenses against the complex and evolving threat landscape, organizations must augment their investment in network security testing. Regularly scheduled network penetration tests emerge as the cornerstone of proactive cybersecurity, aiding in the identification and rectification of vulnerabilities before they can be exploited. Empowering employees with the capacity to recognize and responds to potential threats through dynamic threat landscape training is pivotal. The constant integration of the latest threat intelligence enables organizations to calibrate their defenses against novel attack vectors, fostering an environment of adaptability.
In the quest to minimize the likelihood of unauthorized manipulation or data breaches, organizations should enforce stringent access controls on authorized personnel overseeing network security controls. Comprehensive system upgrades, coupled with the implementation of multi-factor authentication and the meticulous generation of strong, individualized passwords for each account, collectively fortify network security. Adhering to these practices under the guidance of cybersecurity experts, organizations actively diminish risks while enhancing network security amidst the mounting tide of emerging threats.
Conclusion
The foundation of this comprehensive method is network penetration testing, a crucial component of network security. Organizations may strengthen their defenses through constant vulnerability assessments and penetration testing. Safeguarding sensitive data, and cultivating unwavering trust among stakeholders and clients alike holds major importance. The potency of this approach lies in its potential to unmask vulnerabilities before malicious entities exploit them, underscoring its efficacy.
Kratikal emerges as a vanguard of innovative solutions and a holistic approach to combating online threats. As a CERT-In empanelled auditor, Kratikal occupies a position of eminence within the Indian cybersecurity landscape. Its recognition, much like an essential sign of awareness, emphasizes how crucial it is for people and organizations to fully understand new network threats.
The contemporary milieu mandates an unwavering vigilance against cyber risks, elevating the imperative of cultivating resilience. Assurance in the face of new network security challenges finds fruition through meticulous network testing, the implementation of comprehensive security measures, and a steadfast commitment to continuous improvement. Through these multifaceted endeavors, organizations can forge an unbreakable digital barrier that resists the constantly changing environment of cyber attacks.









Leave a comment
Your email address will not be published. Required fields are marked *