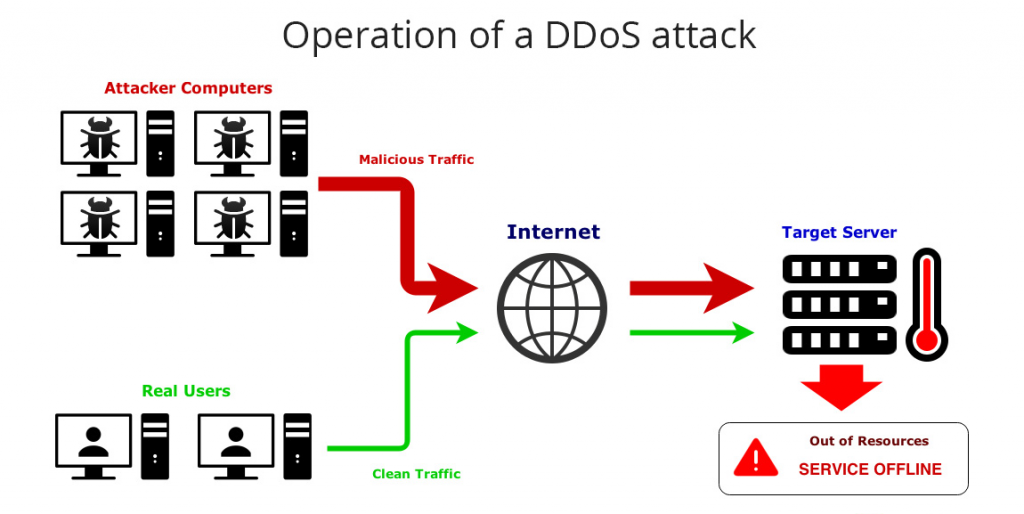
A distributed denial-of-service (DDoS) attack is a malicious attempt for disrupting normal traffic on a targeted network, server or service by overwhelming the target web service with too much traffic from two or more compromised computer systems.
In a DDoS attack, attacker gains control of a network of online machines for carrying out successful attacks. Attackers infect computers and other machines (like IoT devices) with malware, turning these machines into bot or zombie that are under the control of attackers.
Table of Contents
Some of the commonly deployed DDoS attacks are:
- Zero-day DDoS Attacks: In this DDoS attack method, the attacker exploits vulnerabilities that have not been patched yet.
- Advanced Persistent DoS (APDoS): In this type of DDoS attack, attacker employs a number of other
- UDP Flood: User Datagram Protocol (UDP) is an alternative communication protocol to Transmission Control Protocol.
- Fraggle Attack: It is one of DDoS attack types where large amount of UDP traffic is used to a router’s broadcast network.
- Smurf Attack: This attack type exploits Internet Protocol (IP) and Internet Control Message Protocol (ICMP) because of a malware called Smurf.
- NTP Amplification: This type of attack exploits Network Time Protocol in order to overwhelm UDP traffic.
- Other DDoS attacks include Application Level Attacks, Slowloris, HTTP Flood, Ping of Death, SYN Flood etc.
History of DDoS attacks
- One of the first DDoS attacks took place in the year 1999 when hackers disabled the computer network of University of Minnesota for two days with the help of a tool known as ‘Trinoo’
- In the year 2000, Mafiaboy, a 15year old hacker, brought down major internet portals including Yahoo, Amazon, eBay, Dell, CNN as well as others. The financial loss caused by this DDoS attack was around $1.2 billion dollars.
- South Korea was hit with a major DDoS attack called ‘SQL Hammer’ that left the country without Internet or mobile telecom for many hours. The attack infected thousands of servers within a timeframe of 15 minutes and this increased the global traffic by 25%.
- For the first time in the year 2006, cyber criminals threatened national security with a DDoS attack that was launched on various internet portals of Estonia. The websites of many banks, government bodies, newspapers as well as internet providers crashed. It is rumoured that the Russia was behind these attacks.
- During the period of 2011-12 amidst the political tension, ruling as well as opposing parties both underwent a DDoS attack.
- The largest DDoS attack till date was attempted in the year 2015 at the web-based hosting service called Github for less than 10 minutes. The traffic for the attack originated in China and it is believed that Chinese government overlooked this traffic that was scaled at an incredible 1.35 Tbps at peak.. This attack targeted URLs of two Github projects aimed at evading the Chinese state censorship.
Why are DDoS attacks concerning?
- Gone are the days when DDoS attacks were meant for denying services. Now, DDoS attacks veil other forms of cyber-attacks including financial frauds, data breaches etc. This new advanced form of DDoS is known as Smokescreen DDoS attack. This attack poses a risk to the network security of an organization since attackers can easily infiltrate the network with such attack.
- Short sub-saturating DDoS attacks can allow enough bandwidth so that other cyber-attacks can easily occur.
- In many cases, DDoS attacks take place prior to a ransomware attack. Cyber-attackers exploit the vulnerabilities present in the network and install a malicious software in order to launch a ransomware attack on the organization.
- Service degradation and network congestion are some of the results of DDoS attacks.
- DDoS attacks are also responsible for theft, reputation and productivity loss as well as theft of sensitive and confidential data.
How can organizations safeguard themselves against DDoS attacks?
- IDS and IPS: Intrusion Detection System as well as Intrusion Protection System work together to prevent DDoS attacks. IDS is a software application that monitors systems or networks for any malicious activity. Intrusion Prevention System is a threat prevention or network security that examines network traffic flows that help in detecting and preventing vulnerability exploits.
- Traffic Scrubbing: Traffic scrubbing is a common DDoS mitigation technique where the traffic routed to a particular IP address is redirected to data centres. At these data centres, the attack traffic is cleaned or ‘scrubbed’ and is then sent to the targeted IP address.
- Securing the network infrastructure: Mitigating the network security threat combining the firewall, VPN, load balancing, content filtering and other techniques help in securing the network infrastructure of the organization.








Leave a comment
Your email address will not be published. Required fields are marked *