Active Directory (AD) serves as a Microsoft Windows Directory service enabling IT admins to oversee network elements such as users, apps, and data. Safeguarding Active Directory Attacks is crucial to prevent unauthorized access to user credentials, company systems, sensitive data, and applications. A breach could jeopardize identity management, resulting in severe data leaks or system damage.
Given Active Directory’s role in authorizing user access across an organization, it becomes the primary focus for the attackers. Breaching the Active Directory System could grant cyber attackers access to user accounts, databases, applications, and sensitive information. Thus, a compromise in Active Security, especially if undetected, can result in extensive consequences that might be challenging to mitigate.
In this, blog we’ll talk about Active Directory Attacks, how they operate, and how to counter them.
What are Active Directory Attacks and How it Works?
Active Directory constitutes both a database and a suite of services that facilitate the connection between users and the network resources essential for the tasks.
Contained within this database (or directory) is crucial information about the system, encompassing user and computer details, as well as their respective permissions. For instance, it might contain a roster of 100 user accounts complete with job titles, contact information, and passwords.
The services play a pivotal role in overseeing activities within the IT environment. Their primary functions include verifying the identity of users (authentication) by assessing the user ID and password they provide and subsequently granting them access to data that aligns with their authorized permissions (authorization). Now let’s see how an active directory works:
How does Active Directory Work?
Active Directory Domain Services (AD DS) serves as the central component of Active Directory, integrated into the Windows Server operating system. Within this framework, domain controllers (DCs) operate as the servers driving AD DS functionalities. Typically, organizations maintain several DCs, with each housing a comprehensive domain directory copy. Changes performed on one domain controller, such as altering passwords or deleting user accounts, undergo replication across all DCs to ensure synchronization. The Global Catalogue server stores full-domain and partial cross-domain directory replicas in a specific case. This design facilitates easy object retrieval for users and applications across domains. While Windows-based desktops, laptops, and devices can be incorporated into an Active Directory environment, they do not execute AD DS functions.
Book a Free Consultation with our Cyber Security Experts

Active Directory Attacks
Local Admin Mapping using BloodHound
BloodHound, a web application, plays a vital role in detecting and illustrating active directory attack routes within AD environments. This tool highlights the most efficient sequence of actions from any AD account or machine towards a specific goal, like gaining access to the Domain Admins group. Employing BloodHound for routine Active Directory assessments can serve as a potent defensive strategy. It aids in preventing attackers from using a compromised machine or account as a gateway to compromise the entire domain.
By employing PowerSploit and Invoke-UserHunter, BloodHound initiates its process. It begins by crafting a comprehensive map indicating user accessibility to various computers, with a specific emphasis on the Local Administrators Group (referred to as Local Admin Mapping).
Precautionary Measures
Implementing managed server access safeguards can help mitigate such assaults. Following Microsoft’s recommended best practices, the adoption of a tiered administrative model for Active Directory offers a stringent approach to access control, effectively reducing potential attack paths. Watchful tracking of unusual logins aids in detecting attempts to exploit these attack paths through authentication and login anomalies.
Pass the Hash
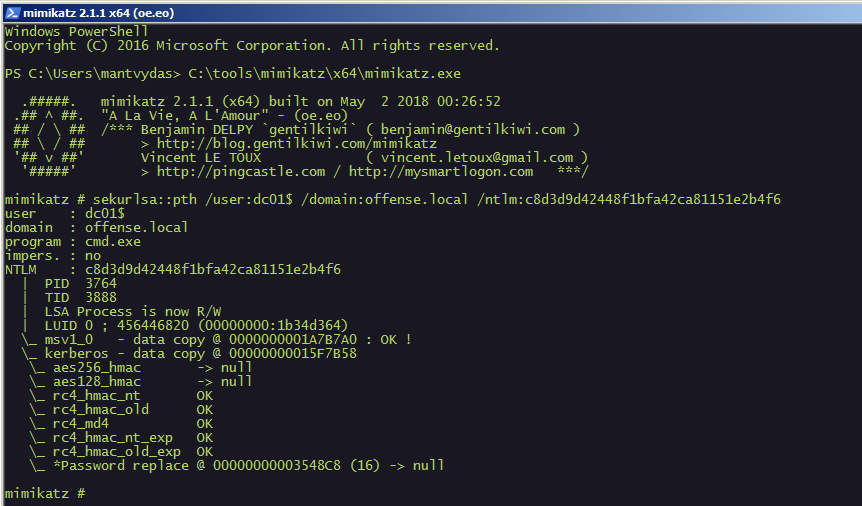
Active Directory hashes the passwords it stores, just as other password databases. A hash simply put, is a mathematical representation that hides the clean-text password from view. Pass-the-hash attacks don’t require the attacker to know the password or crack it to get access to the system, unlike other attempts to steal credentials. Instead, it starts a new session using a saved copy of the password.
Precautionary Measures
Preventing “Pass the Hash” Attacks is challenging, yet Windows has introduced various features to enhance prevention measures. Among these, implementing login restrictions emerges as a potent strategy, effectively avoiding the storage of privileged account hashes in extractable locations. Microsoft’s suggested course of action comprises a layered administrative paradigm for Active Directory, strengthening the security of privileged accounts, and significantly reducing the likelihood of breach via such methods. Additional security measures include using Remote Desktop’s Restricted Admin mode, Protected Users security group, and enabling LSA Protection.
NTDS.dit Extraction
All Active Directory information is kept on domain controllers in a file named ntds. dit, also known as “the dit”. This file can be found by default at the following path: C:\Windows\NTDS\. An attacker who gains access to Active Directory or who compromises the backup system the business uses and extracts the ntds.dit file from the backup can both access the ntds.dit file. This vulnerability underscores the importance of thorough network penetration testing to identify and rectify potential security risks.
To strengthen the overall security posture of the Active Directory system, it is essential to undertake comprehensive network hardening measures. This entails utilizing intrusion detection systems, enforcing strict password policies, enabling safety auditing, and often patching and updating systems.
Precautionary Measures
Use the following recommended practices to lessen the chance that attackers will extract the ntds.dit file:
- The number of accounts that can access domain controllers should be kept minimum
- For domain controllers, adhere to the clean source principle: The security level of all supporting hardware (like ESX and linked storage) and software (like backup programs) for domain controllers must match that of the domain controllers themselves
- Keep domain controller computers physically secure. Run read-only domain controllers if they cannot be secured
- Preventing individuals from having administrative privileges outside of their security parameter
Password Spray
A password attack known as “Password Spraying” targets Active Directory Domain Services accounts with weak passwords. Password Spraying is an attacker using a single weak or common password to attempt it on several Active Directory accounts.
As the attacker only tries the password once per account, it has advantages over the traditional attack in that it prevents account lockouts. Attackers can discover weak passwords in the environment across numerous users in this method.
Precautionary Measures
- Utilise sound password policies to impose strong passwords.
- Prevent the usage of additional passwords or password breaches.
- Avoid reusing account passwords.
- Encourage people to not use paraphrases as their passwords.
Conclusion
The strength of cybersecurity posture depends on how well can defend Active Directory infrastructure. Cyber attackers frequently use a variety of attack vectors, including the ones we’ve outlined, to target Active Directory accounts.
By strengthening the environment’s overall password security, enforcing good password hygiene, and deleting compromised, incremental, and otherwise weak passwords, the security of the Active Directory environment and privileged accounts can be improved.