
Cleartrip, Flipkart’s popular travel booking website, has confirmed a major data breach on July 18, 2022, after the hackers claimed to have posted the stolen data on a dark web forum.
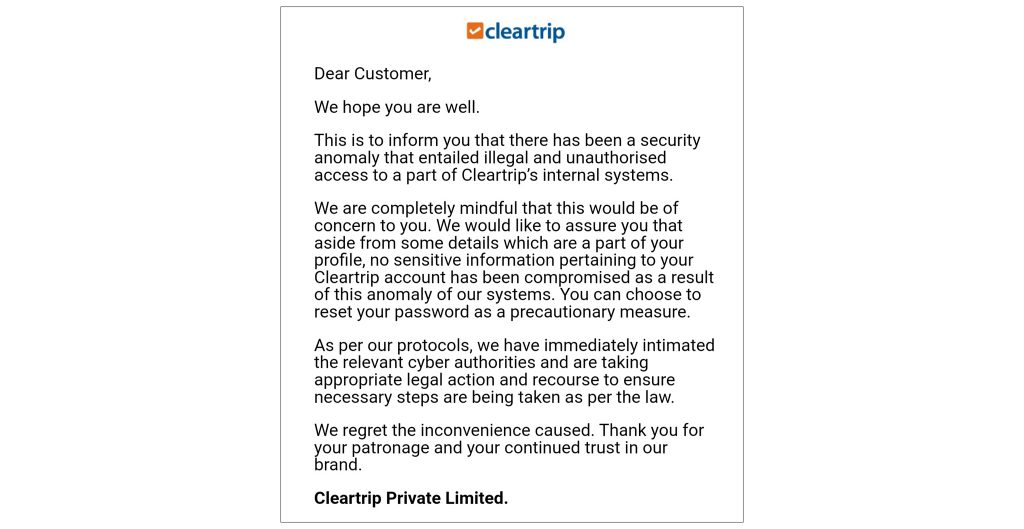
In an email, shared with its customers, Cleartrip acknowledged the “security anomaly that entailed illegal and unauthorized access” to a part of its internal systems, adding that aside from a few customer profile details, “no sensitive information pertaining to the Cleartrip account has been compromised”.
Cleartrip also urged the relevant cyber authorities to take legal action and recourse to ensure that necessary steps are being taken as per the law, meanwhile, recommending the customers to reset their passwords as a precaution.
Gravity Of The Incident
Cleartrip’s announcement may have been presented in a sincere manner, but it surely downplayed the solemnity of the issue at hand.
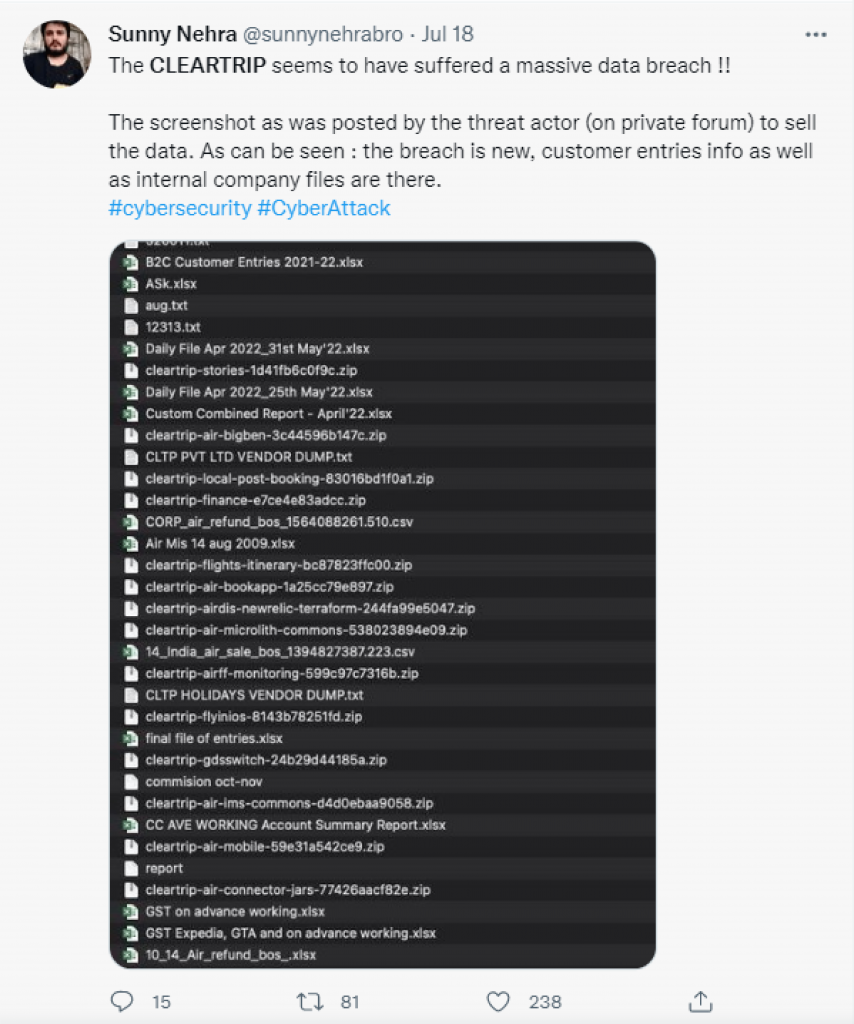
Sunny Nehra, an independent security researcher, tweeted screenshots shared by the hackers carrying details of Cleartrip’s stolen data which was put on sale on a dark web forum. The data dump includes –
- B2C Customer Entries (2021-22)
- Internal Financial Data
- Vendor-related Data
- Refund Information
- Commissions
- GST Filings
Nehra declared that the attacker appeared to be adept at network breaches as his previous hacks were also executed through unauthorized network access. He also added that the attack on Cleartrip may have exploited a Zero-day vulnerability since no Security Operations Center (SOC) or any network traffic monitoring or blocking systems of an organization, unless it was based on common payloads, can prevent most zero-days.
Adding to his declaration, Nehra notified that the attacker confessed to having compromised sensitive information from a power grid, a major medical institute, and various networks of other entities in India.
Table of Content
Cleartrip’s Past Breaches
Cleartrip’s data breach may have been the first remarkable breach since the Indian Computer Emergency Response Team’s (CERT-In) security guidelines in June, but it is not the first time the travel portal’s security has been endangered.
Back in 2017, Cleartrip was briefly exploited by a hacking group named ‘Turtle Squad’, who defaced their website. The hack came to light with an eagle-eyed Twitter user’s screenshot of the defaced website which featured a message from the hacking group – “Roses are read, violets are blue, all your security is up to you. We Are Turtle Squad. Got It?”
The message further made a mockery of the website’s security by adding, “Hey! Are you one of those 1.4 crores users? They say you’re secure”.
If the hackers’ claims were to be believed, the data of millions of users had been compromised, but many suspect the hack may have been only pulled to highlight Cleartrip’s vulnerable IT infrastructure.
Cybersecurity: A Persisting Matter For The Travel Industry
COVID-19 brought the travel and tourism industry to a standstill in 2020, adversely affecting the sector’s business and growth worldwide, but with the world getting firmly back on its feet, the travel and tourism industry, too, has gained momentum.
A new research by World Travel and Tourism Council (WTTC) predicted the sector’s global economy to reach $8.6 trillion, while creating 58 million jobs, in 2022, which would promote economic growth and recovery around the globe.
The fast-paced rehabilitation of the travel and tourism industry not only deems it praiseworthy, but also makes it a magnet for cybercriminal activities.
Principal Security Challenges
The tourism industry predominantly depends on online transactions for their bookings, payments, listings and other crucial exchanges, with the pandemic promoting an even larger interaction over the internet, leaving it exposed to numerous attack vectors.
- DDoS Attacks – Distributed-Denial-of-Service (DDoS) attacks employ the network of thousands of botnets to infect a website with malware, and send limitless requests/enquiries to overwhelm the network or server with a massive amount of traffic until it crashes and the users unable to access it.
- POS (Endpoint) Attacks – Point-of-Sale attacks utilize the lack of security during slow periods to infect the network with malware, which spreads by itself throughout an organization’s network, ultimately corrupting its POS terminals. POS terminals’ RAM stores the information of a card briefly after it is swiped, which the malware copies and transports back to the attacker via an internal staging server.
- Malware Attacks – Malware (Malicious Software) attacks focus on a command-and-control server, which permits the attackers to commune with the affected systems, collect sensitive data and, under certain circumstances, allow the compromised device or server to be remotely controlled.
- Ransomware Attacks – Ransomware is designed to locate an organization’s sensitive data, manipulate backups to make them futile, create backdoors in the system, encrypt the valuable information and demand a ransom, which is normally paid in cryptocurrency.
Security Priorities: What should be done?
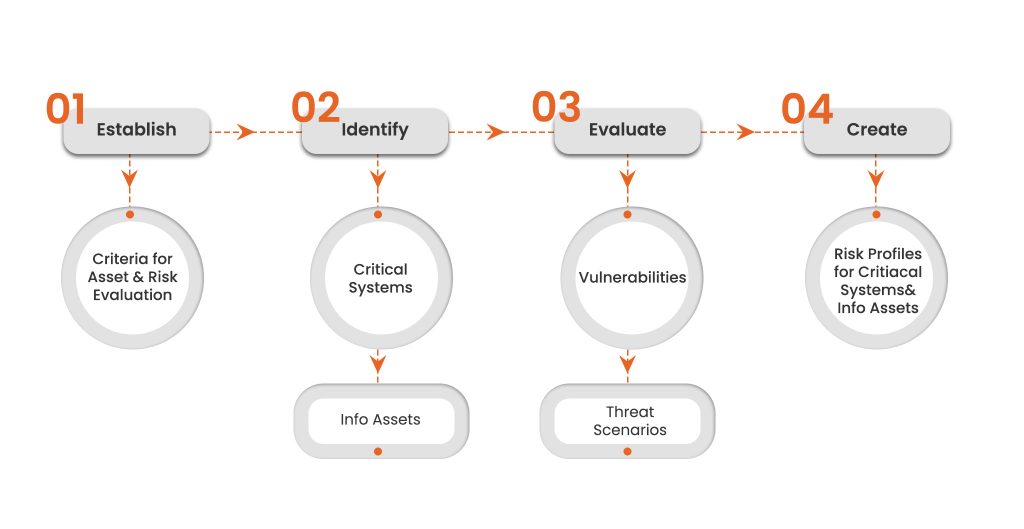
To design a fool-proof cybersecurity strategy providing the finest protection to important business assets and operations, organizations should first understand their IT infrastructure, the systems which are critical as well as valuable information assets for cybercriminals. This means that they should not only be aware of these systems and assets, but should also know the asset’s location, and the people who have access to them.
Getting an understanding of how these assets are related to one another, the possible threats to them and the vulnerabilities that can compromise them can allow businesses to safeguard their IT frameworks.
- Vulnerability Assessment and Penetration Testing (VAPT)
A periodic VAPT is the most definite method to eliminate the vulnerabilities present in an organization’s networks and systems. Not only does VAPT run an in-depth analysis to expose all the exploitation weaknesses of an IT infrastructure, it also detects, identifies, and classifies all these flaws and provides guidance for their mitigation.
- Network Penetration Testing
Network security testing specifically targets the networks or servers of an organization to evaluate their state of security by detecting all the exploitable vulnerabilities in them so they can find a fix before an attacker can discover and exploit them.
How can Kratikal Help?
As a CERT-In empanelled security consultancy firm, Kratikal provides a complete suite of both manual and automated VAPT services, including Network Penetration Testing, Web/Mobile Application Penetration Testing, Cloud Penetration Testing, and many others to keep your IT infrastructure intact.
We also provide security auditing for Compliance, the important security standards an enterprise must adhere to for the smooth running of their operations, such as PCI DSS, ISO/IEC 27001, GDPR, HIPAA, and others.
Cleartrip’s data breach is a huge concern, but it is also a lesson for us. The incident is crucial for us to bookmark to remind ourselves why cybersecurity is critical in the modern world, and why we should take necessary steps to secure our networks, devices and systems.
If a data breach were to hit a digital platform that you frequently use, what will you do? Share your thoughts in the comments below!


