
A new research has uncovered a unique attack tactic exploiting speculation execution to bypass the current defenses in the AMD and Intel CPUs. Harvesting Spectre-BTI attacks, the exploit initiates potential leakage of sensitive information from a system’s kernel memory.
Entitled ‘Retbleed’ by ETH Zurich researchers Johannes Wikner and Kaveh Razavi, the vulnerability counteracts numerous AMD and Intel microprocessors. On AMD, it is tracked as CVE-2022-29900, and impacts AMD Zen 1, Zen 1+ and Zen 2 CPUs, while Intel’s CVE-2022-29901 affects CPU generations 6, 7, and 8.
SPECTRE, The Microarchitectural Side-Channel Attacks
Microarchitectural side-channel attacks calculate the time taken between memory reads from the shared (with the victim) cache to accelerate or decelerate the reads. During the process, some of the shared memory is flushed for the attacker to manipulate.
Spectre-BTI (CVE-2017-5715 or Spectre V2), a subset of such side-channel attacks, exploits the flaws in the design of speculative optimization through a timing side-channel to fool a program into leaking sensitive information by entering the environment of its memory space.
- Speculative Execution – An optimization technique in which a processor (CPU) prepares information beforehand using concurrent processing and Out-of-Order Execution (OoOE). It fetches the data that can be required later on to eliminate the delay caused by waiting for the upcoming instructions to gain a performance boost.
Spectre takes advantage of the traces left behind by the execution in the cache, leading to the processor being tricked into executing inaccurate paths to reveal encryption keys or passwords from inside the victim’s memory address-space.
Table of Content
What is Retbleed?
The new member of the speculative execution attack family called Spectre-BTI (Branch Target Injection), Retbleed exploits return instructions, unlike its kin, that exploit indirect jumps or calls to trigger damaging branch target speculation. This feature is distinctive as it sabotages Retpoline (Return Trampoline), the popularly engaged relief against the Spectre side-channel attacks influencing the modern microprocessors.
Retpoline (Return Trampoline) originated in 2018 to forbid information theft by unauthorized attackers utilizing Spectre-BTI attacks. It reinstates indirect jumps with returns, which were deemed unrealistic to exploit due to their unpredictable nature.
However, the Computer Security Group’s (COMSEC) research proved Retbleed’s exploitation to be feasible due to the following reasons:
- The microarchitectural conditions in both Intel and AMD can be triggered to enforce returns to be predicted like indirect branches. Necessary tools were also developed to locate regions in the kernel memory where the required conditions could be fulfilled.
- The research established that an unprivileged user could also inject branch targets residing inside the kernel address-space.
The research also shed light on AMD CPUs’ ‘phantom jumps’ (CVE-2022-23825), the branch predictions occurring in the absence of any corresponding branch instruction. Using the same techniques used to exploit Retbleed, the group eliminated the return instructions and observed branch target predictions on the given instructions, implying significant mitigation from the exposed attack surface.
The researchers issued a POC (Proof Of Concept) regarding the issue. Check it out here.
(This POC has been taken from GitHub)
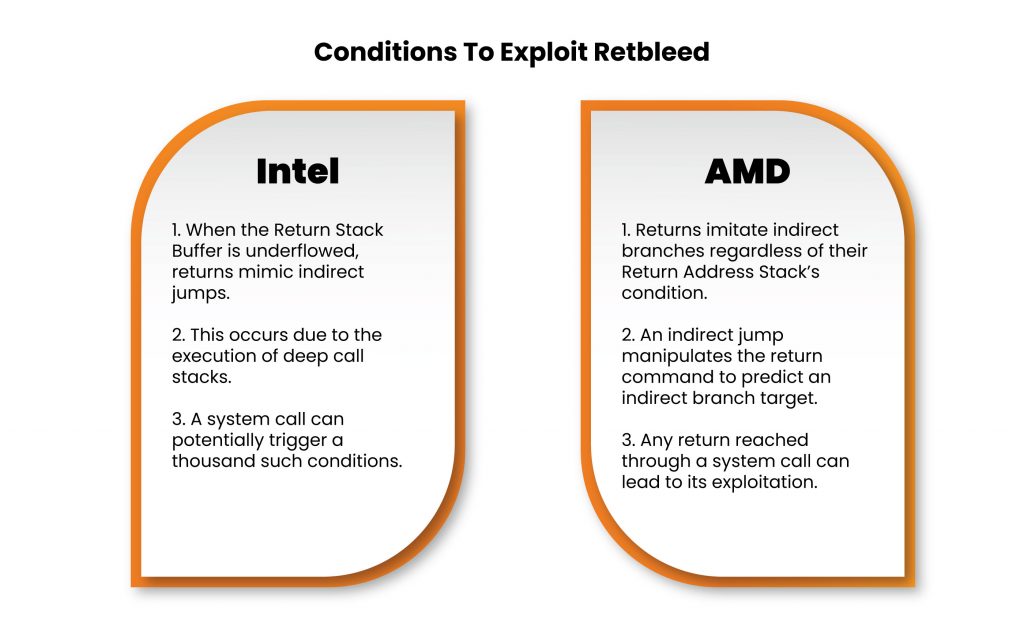
Conditions To Exploit Retbleed
- Intel
- When the Return Stack Buffer is underflowed, returns mimic indirect jumps.
- This occurs due to the execution of deep call stacks.
- A system call can potentially trigger a thousand such conditions.
- AMD
- Returns imitate indirect branches regardless of their Return Address Stack’s condition.
- An indirect jump manipulates the return command to predict an indirect branch target.
- Any return reached through a system call can lead to its exploitation.
What Can Be Done To Mitigate This Issue?
Intel and AMD have swiftly released a security advisory following the discovery of the vulnerability in their processors, while it remains unexploited in the wild by cybercriminals. AMD recommends using Jmp2Ret as a new line of defense, while Intel, tagging Retbleed as Return Stack Buffer Underflow (RSBU), has also advocated Indirect Branch Restricted Speculation (eIBRS) to combat the flaw despite Retpoline mitigations being in place. Additionally, Intel’s advisory suggested no update for Windows operating systems since they use IBRS by default.
Unfortunately, the mitigations are expected to hinder the performance of the concerned processors with the implementation of IBRS.
Strike Out Vulnerabilities With Kratikal
For security threats that are difficult to discard once they are exploited, security testing is the ultimate mitigation.
Vulnerability Assessment and Penetration Testing (VAPT) analyzes the security structure of an organization to discover the hidden loopholes and flaws, and recommends fixes for their further dealing, assisting enterprises in improving and protecting their security structure.
Vulnerability assessment identifies, classifies, and addresses the security flaws while providing support and mitigation to counter these identified weaknesses. Penetration testing, on the other hand, exploits the detected vulnerabilities to provide a deeper understanding of the discovered flaws.
Kratikal, a CERT-In empanelled security solutions consultancy firm, offers a manual and automated suite of VAPT services. These services include Mobile/Web Application Penetration Testing, Network Penetration Testing, Cloud Penetration Testing, and significantly more, along with security audits for both standard and regulatory compliance, namely ISO/IEC 27001, PCI DSS, HIPAA, GDPR to name a few.
Vulnerability exploitation is an everyday subject, but numerous organizations still prefer to stay ignorant of it. Do you think if precautions are taken beforehand, these incidents could be avoided? Share your thoughts in the comments below!


