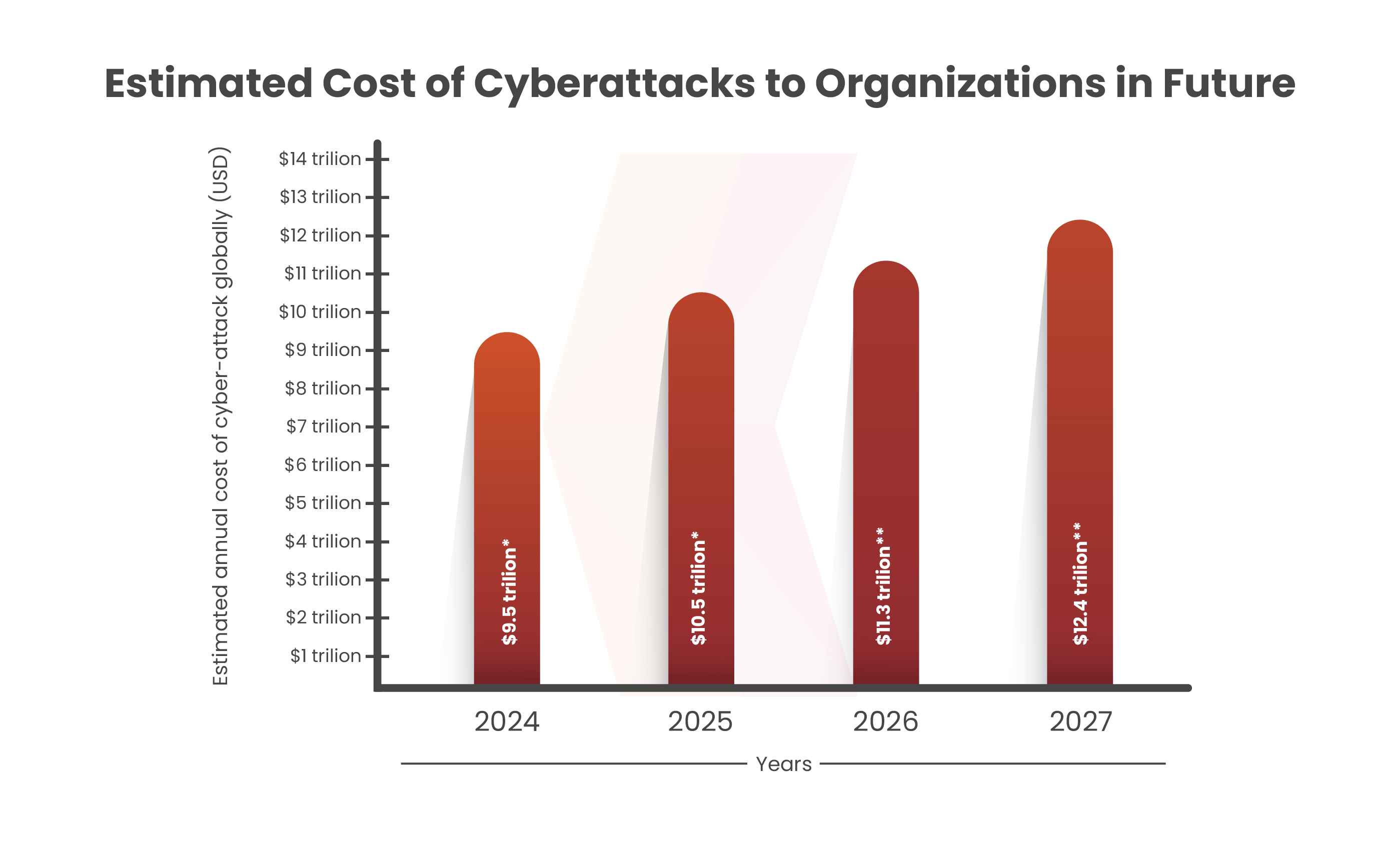
As per the 2022 Cost of a Data Breach Report by IBM and the Ponemon Institute, organizations promptly address data breaches within 200 days and incur an average of $1.1 million in data breaches. In 2024, data breaches are projected to increase by $9.5 trillion from the previous year. As data breaches pose significant security risks, sensitive information is regularly transmitted online. This ongoing exchange of data exposes individuals and businesses to potential breaches, where attackers are able to target virtually anyone from anywhere. Businesses worldwide store data digitally, leaving servers vulnerable to various cyberattacks.
A recent incident took place at a famous remote desktop software, AnyDesk. In this blog, we will talk about the incident and how these cyberattacks can be prevented.
Table of Contents
What Happened with Anydesk?
AnyDesk, a remote access software provider, faced a cyberattack in mid-January 2024, with the original breach occurring in late December 2023. In Europe, attackers compromised two relay servers, which transmitted credentials to AnyDesk clients. The increasing theoretical possibility of rewriting the AnyDesk code allowed customers to use malicious software and provide their passwords. AnyDesk reviewed its code and found no evidence of malicious damage of bad code to customers through its system. The company revoked security-related signing rules and certificates, pushed out software updates, and forced password resets for all customers as a precaution. AnyDesk clarified the incident did not involve any ransomware and was not an extortion attempt, the result of a security breach. There was no evidence of user session hijacking.
The company confirmed that there was no evidence that end-user systems were affected to control the situation and urged users to ensure that they were using the latest version. Security researchers found that hackers were selling access to AnyDesk accounts affected by alleged breaches in known cyber threat systems. AnyDesk said it did not sell additional notifications to users on the dark website and the issue is not interconnected because the certificates were issued directly to customers.
Image Source: Beeping Computers
Book Your Free Cybersecurity Consultation Today!
How these types of Cyberattacks can be Prevented?
Adding barriers to prevent cyberattacks is a simple yet effective approach to stop data breaches. This will make it harder for hackers to go toward their goal of stealing data.
We can divide the strategy into 2 parts:
Stage 1: Protecting Network Compromise
At this stage, a comprehensive strategy is discussed for preventing data breaches by focusing on 4 key cybersecurity principles such as Internal Security Vulnerability Management, Data Leak Management, and Vendor Risk Management. Each term addresses different aspects of network security, including employee education, internal vulnerability detection, data leak detection, and managing third-party vendor risks. By working on these key areas, organizations can strengthen their defense against data breaches.
3 Stages of Attack Surface include
Vulnerability Management
This includes internal security vulnerabilities, unstructured resources, open ports, and lack of Multifactor Authentication (MFA), which can pose significant risks to organizations. A key strategy to mitigate network risk includes maintaining high-security standards. It emphasizes the importance of implementing holistic security measures such as firewalls, endpoint detection and response solutions, and antivirus software.
Data Leak Management
Data breaches can be prevented by implementing firewalls in the organization’s systems. It is important to prevent data leaks by following compliance standards which will help in regular security audits.
Vendor Risk Management
Vendor Risk Management (VRM) aims to mitigate security risks associated with third-party vendors and service providers. The VRM process includes onboarding, compliance, continuous monitoring, and termination, each addressing a specific security aspect of the vendor relationship lifecycle. Some of the key features of VRM include analyzing vendor security levels, ensuring compliance, and third-party identification of emerging threats. Continuous monitoring and effective oversight of third-party security threats via VRM prevent network breaches.
Get in!
Join our weekly newsletter and stay updated
Implementing strong enforcement measures is critical in preventing unauthorized access to sensitive data, thereby reducing the risk of data breaches. Restricting authorized access can significantly reduce the potential for a data breach and protect sensitive information from unwanted access attempts.
The attack surface includes 3 steps:
Multi-Factor Authentication (MFA)
MFA adds additional user-identity verification at login, improving security. More secure MFAs have advanced biometrics that ensure fingerprints or facial recognition, making it harder for cyber hackers to override. Passwordless authentication, which is often in conjunction with MFA, requires users that is, password-less automation, through means such as fingerprints or hardware tokens.
Network Segmentation
Once a network breach occurs, hackers move sideways in search of sensitive resources. By cutting off vulnerable network sites from regular routes, this lateral movement can be stopped. To enhance security, all user accounts accessing the restricted areas should be secured by multiple controls.
Data Encryption
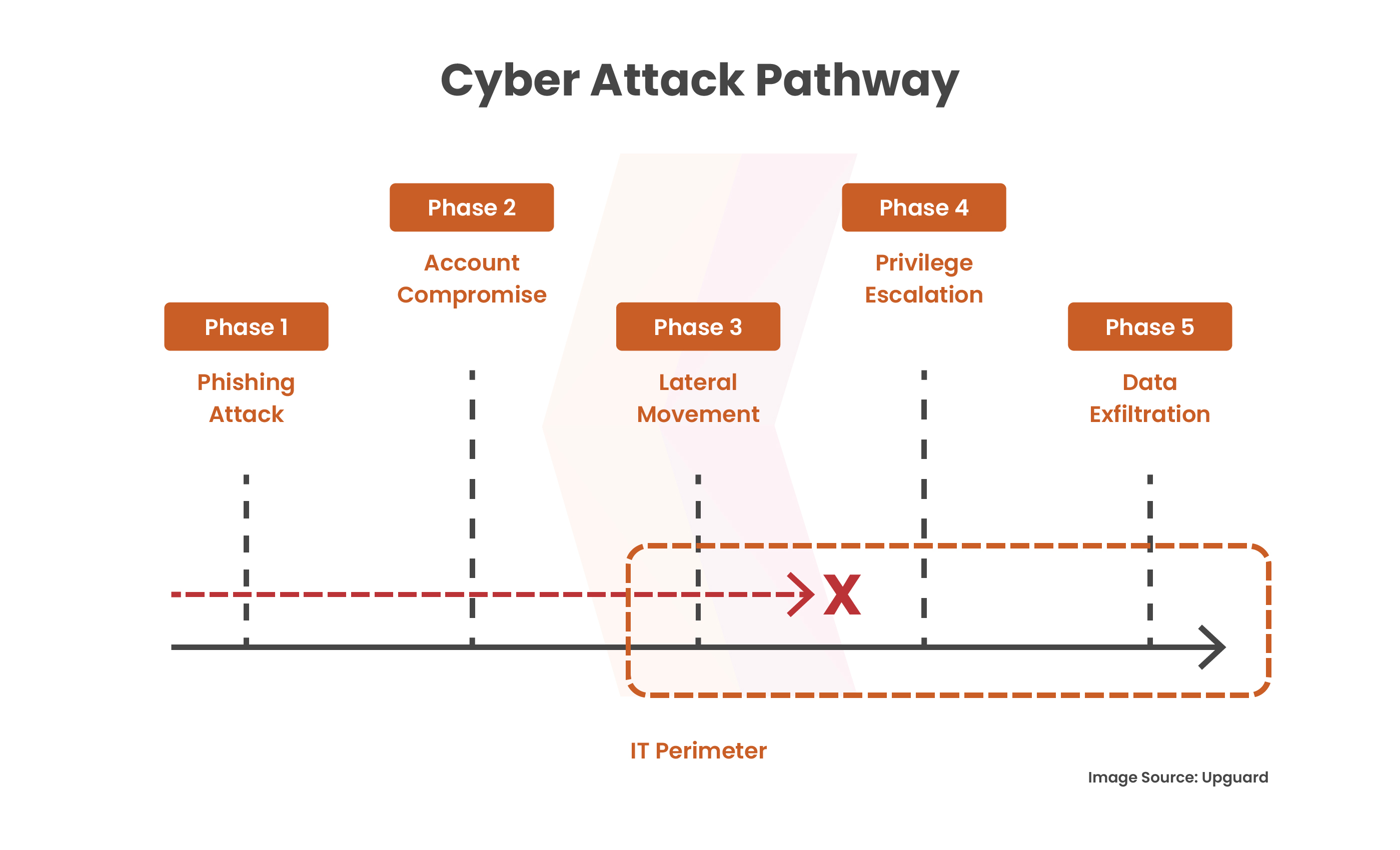
Ensure your data encryption protection policy covers all internal data, including information stored on hard drives and laptops, not just in critical locations. Organizations can thwart hackers’ attempts to increase privileges and decrease the compromise on sensitive resources by encrypting all internal data and putting strong security measures in place. This successfully closes off the attack pathway and improves overall security posture by obstructing the attack’s progression between stages three and four.
Conclusion
This recent cyber incident at AnyDesk highlights the ongoing threat of cyberattacks and the need for robust security measures to prevent unauthorized access and data breaches. This includes internal security and vulnerability measures, data leak measures, vendor risk management, multiple authentication, and communication through similar mechanisms. Organizations can strengthen their security and reduce the risk of unauthorized access and compromise of networks and sensitive data. In today’s digital environment, organizations need to be vigilant of emerging threats and stay updated.
Kratikal is a CERT-In empanelled auditor, that provides cyber security services including VAPT and Compliance. We provide strong defenses to offset the ongoing risk of cyberattacks. With Kratikal’s guidance, it is easily possible to address and fix security issues. This can easily prevent malicious hackers from taking advantage of possible vulnerabilities.
Ref: https://thehackernews.com/2024/02/anydesk-hacked-popular-remote-desktop.html








Leave a comment
Your email address will not be published. Required fields are marked *