Table of Contents
Introduction
Open-source tools and packages are an essential part of the modern software development ecosystem. They are widely used by developers to speed up the development process and reduce the amount of work required to build complex systems. However, this convenience comes at a cost. Open-source packages can be compromised by attackers to deliver malicious software and infect websites and organization networks. In this blog, we will explore the potential risks of using open-source packages and the ways to prevent them.
What is an open-source package?
An open-source package is a piece of software that is freely available to anyone to use, modify, and distribute. These packages can be found in repositories like NPM, Maven, or PyPI and are an integral part of modern software development. They are built by developers worldwide and often serve as building blocks for larger projects.
Get in!
Join our weekly newsletter and stay updated
Recent Examples of Attacks Due to Malicious Open-source Packages
Let’s discuss the use cases of malicious open-source tools and their impacts:
Malicious Info Stealer PyPI Package
Three malicious packages containing info-stealing malware were recently discovered on the PyPI (Python Package Index) repository. The packages, named ‘colorslib,’ ‘httpslib,’ and ‘libhttps,’ were all uploaded by an individual identified as ‘Lolip0p’ between January 7 and 12, 2023. Fortinet, the cybersecurity firm, identified and reported these malicious packages, resulting in their removal from PyPI.
PyPI serves as the primary repository for Python packages, widely used by software developers to access essential components for their projects. However, its extensive usage also attracts the attention of threat actors who target developers and their projects. These malicious packages often camouflage themselves as useful tools or mimic well-known projects by altering their names.
Due to the sheer volume of package uploads, PyPI lacks the capacity to thoroughly examine each one. Therefore, it relies on user reports to identify and eliminate malicious files. Unfortunately, by the time these packages are removed, they have often already been downloaded hundreds of times.
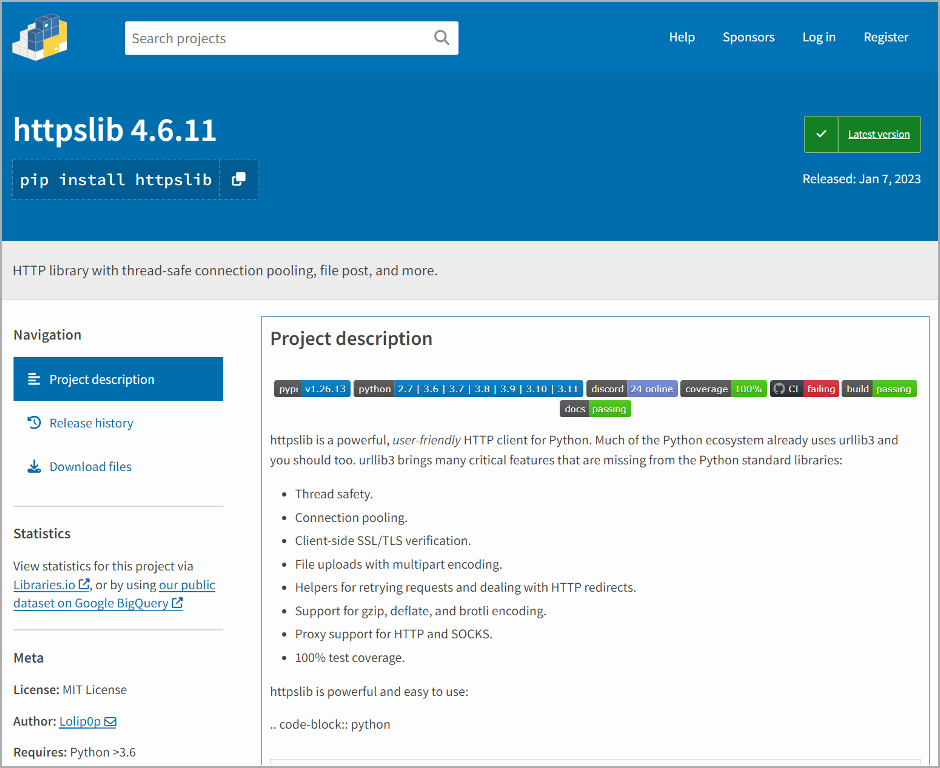
The above screenshot represents the malicious pypi package as discovered by Fortinet
Supply Chain Attack on SolarWinds, 3CX, Log4j
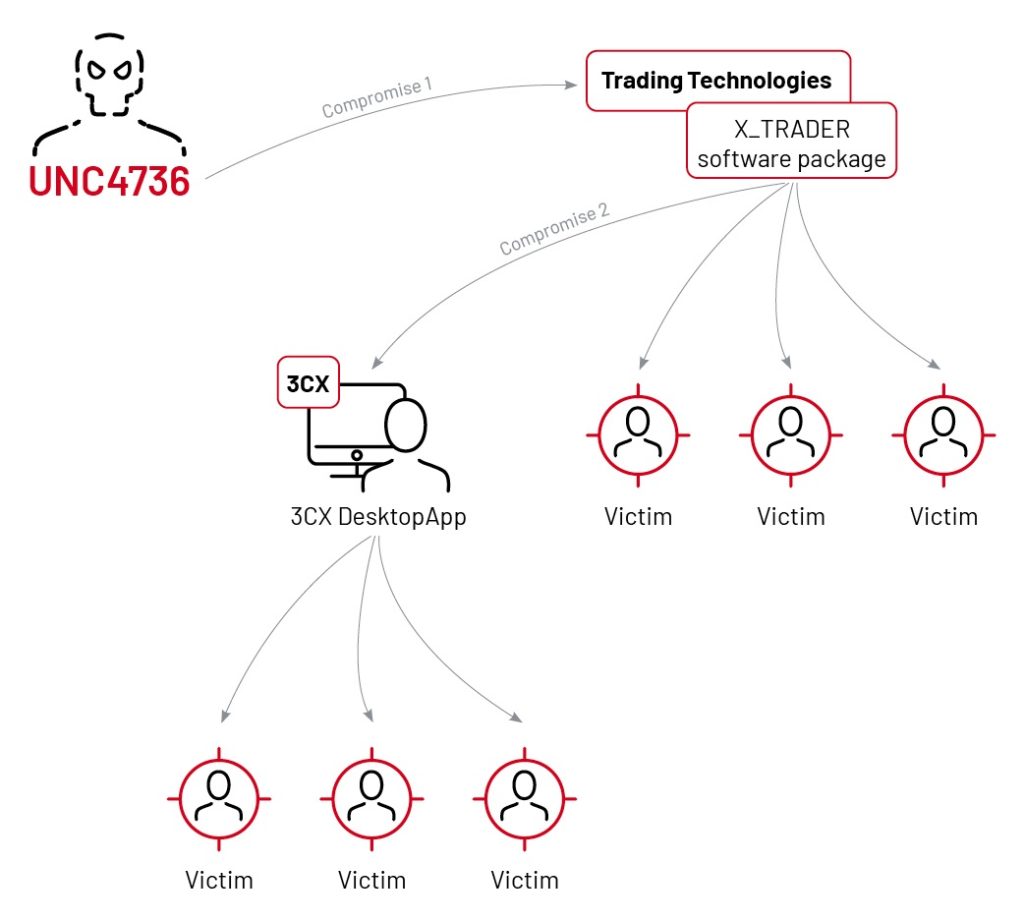
Recent attacks on 3CX, Solarwind shows a concern for supply chain risk. If we talk about the 3CX hack that was caused by another supply chain hack has infected thousands of systems around the world. Threat actors infected X_Trader software which was used by one of the 3CX employees and that led to another supply chain attack.
Even security vendors can be targets. In the case of SolarWinds, for example, one of the higher-profile companies breached was FireEye, a cybersecurity vendor. FireEye says that the attackers didn’t get into customer-facing systems, just the penetration tools used for security testing. The fact that it got hit at all is worrisome.
3CX and SolarWinds have highlighted the significant risks associated with the supply chain. In the case of the 3CX hack, it was triggered by a previous supply chain attack, resulting in the infection of numerous systems worldwide. The threat actors targeted the X_Trader software, which was utilized by an employee of 3CX, thereby initiating a subsequent supply chain attack.
Any company involved in the production of software or hardware for other organizations becomes a potential target for attackers. Even highly security-conscious firms are vulnerable to infiltration by nation-state actors, who possess substantial resources and expertise.
The incident involving SolarWinds further emphasizes this risk, as it impacted prominent entities such as FireEye, a cybersecurity vendor. Although the attackers did not breach customer-facing systems, they managed to compromise the penetration tools employed for security testing. The fact that even a security vendor like FireEye was targeted raises concerns about the overall security landscape.
Dependency confusion attack on NPM:
A researcher demonstrated a “dependency confusion” attack on NPM, the official repository for Node.js packages. The attack involved uploading a malicious package with the same name as an internal package used by a company, which could then be downloaded by developers and executed on their systems. This attack had the ability to compromise the security of any Node.js project that used the affected packages, potentially exposing sensitive data or allowing attackers to take full control of systems.
How Can Open-source Packages Be Infected?
Open-source packages can be infected by attackers in a number of ways. One of the most common methods is by inserting malicious code into the package. This code can be designed to deliver malware, spyware, or ransomware, and can compromise the security of any system that uses the package. Attackers can also create fake versions of popular packages and publish them on public repositories, making them appear legitimate to unsuspecting developers.
Another way attackers can infect open-source packages is by exploiting vulnerabilities in the package’s dependencies. This is especially common when packages have many dependencies, and developers do not regularly update them. Threat actorsAttackers can use these vulnerabilities to gain access to the system or network and deliver malicious software.
Risks Associated with the Usage of Infected Open-source Packages
Using infected open-source packages can have severe consequences for organizations. The malware delivered through these packages can compromise sensitive data, steal financial information, and damage the reputation of the organization. In some cases, the malware can also spread to other systems in the organization’s network, causing widespread damage and disrupting business operations.
Ways to Protect Against Malicious Open-source Packages
Protecting data against malicious open-source packages is a critical part of any organization’s security strategy. Here are some best practices to keep in mind:
- Regularly update packages and dependencies: Updating packages and dependencies regularly can help protect against vulnerabilities and reduce the risk of infection.
- Only use trusted sources: Use packages from trusted sources and repositories only. It is also essential to verify the integrity of the packages before use.
- Use vulnerability scanners: Using vulnerability scanners can help identify vulnerabilities in packages and dependencies.
- Monitor for suspicious activity: Regularly monitor the organization’s network and systems for suspicious activity. This can help identify and respond to attacks early.
- Educate employees: Educating employees on the risks of using open-source packages and how to protect against them is essential.
Conclusion
Open-source packages are an integral part of modern software development, but they come with potential risks. Malicious open-source packages can infect systems and networks and compromise sensitive data. By following best practices like updating packages regularly, using trusted sources, and monitoring for suspicious activity, organizations can protect themselves against these risks and continue to benefit from the advantages of open-source development.
Kratikal a Cert-In Empanelled organization can protect organizations by providing a complete secure code auditing to prevent any serious cyber attack before it’s very late.
Get in touch to make your organization cyber-proof.









Leave a comment
Your email address will not be published. Required fields are marked *