In 2024, approximately 183,000 customers worldwide were affected by supply chain attacks. In terms of frequency, the software supply chain experienced one attack every 48 hours. Surprisingly, India is among the most targeted countries, along with the USA, UK, Australia, Japan, and Germany. Manufacturing, healthcare, defense, and aerospace are among the most targeted sectors. Among the most targeted entities are the IT providers comprising 1/3rd of the the total attacks. Cybersecurity threats circulating via open-source package repositories surged by 1300% between 2020 and 2023.
A supply chain attack is a form of cyberattack where hackers target loopholes found in an organization’s supply chain rather than directly attacking the organization. It generally involves third-party vendors, software providers, hardware manufacturers, or any external partner that the organization relies on. In this type of attack, hackers exploit the trust and access provided to these suppliers to penetrate the organization, frequently evading conventional security measures.
Table of Contents
Why Are Supply Chain Attacks Growing?
We are digitally interconnected. This has become a necessity for smooth functioning in the corporate world. Such inter-dependency has made supply chains more complex as they span across multiple organizations, regions, and technologies. Along with it comes vulnerabilities that hackers can exploit. Some of the key factors contributing to the growth of supply chain attacks are:
- Increased Digital Transformation: As organizations adopt cloud services, third-party APIs, and outsourced development, their attack surface expands.
- Trust in Third Parties: Many businesses implicitly trust their suppliers and partners, often without rigorous security assessments.
- High Reward for Attackers: Compromising a single supplier can potentially grant access to multiple downstream targets, amplifying the impact of an attack.
- Sophistication of Threat Actors: Nation-state attackers and organized cybercriminal groups are investing more resources into exploiting supply chain vulnerabilities.
Need To Prioritize Detection and Mitigation of Supply Chain Attacks
Before moving on to how to detect and mitigate supply chain attacks it is important to understand the need. Here are a few such key factors:
Impact on Operations
The effect of a supply chain attack can spread from one supplier to an entire network. It impacts all organizations that rely on the vendor whose security has been compromised. From downtime to revenue loss, the effects are cascading.
Reputational Loss
In case of a supply chain attack, an organization may not be directly at fault. However, it impacts its reputation among its customers, partners, and stakeholders. The organization may be seen as inefficient in protecting its supply chain or its customers’ data.
Financial Loss
Supply chain attacks are costly. From immediate recovery expenses to long-term losses caused by customer attrition or lawsuits, the financial burden of a breach can cripple organizations. The average cost of a data breach continues to rise, and supply chain breaches often worsen these costs.
National and Industry-Wide Security Risks
In some cases, supply chain attacks are targeted against entire industries or even nations rather than individual organizations. Critical infrastructure, like energy grids, healthcare systems, and financial networks depends on complex supply chains. Thus, it makes them attractive targets for attackers.
Regulatory and Legal Consequences
There are certain guidelines and industry-specific standards that require organizations to ensure their third-party suppliers follow the stated security guidelines. This is important because failing to do so can result in non-compliance, leading to hefty fines and legal challenges.
Book Your Free Cybersecurity Consultation Today!
Real-World Examples and Lessons Learned
Example 1: On February 21, a ransomware attack targeted one of the largest health payment processing companies globally. The attackers:
- Disrupted the company’s operations.
- Stole up to 6TB of sensitive data, including millions of patients’ protected health information (PHI).
- Demanded and received a $22 million ransom to retrieve the stolen data.
Operational disruption led to a $1.1 billion loss in earnings for the second quarter and an estimated $2.3 billion loss for the year.
Lessons Learned:
The attackers exploited a remote server without adequate protection. Implementing multifactor authentication (MFA) could have prevented unauthorized access, blocking the attackers from entering the system.
Example 2: On May 8, 2024, a ransomware group attacked a major nonprofit healthcare system operating 142 hospitals and 40 senior facilities. The attack:
- Shut providers out of the electronic health records (EHR) system.
- Caused disruptions across hospitals in three states, leading to delayed or lost lab results, medication errors, missed safety checks, and increasing risks of critical mistakes.
- The attack exposed some patients’ PHI and contributed to a $1.8 billion operating margin loss for the system.
Lessons Learned:
The attack succeeded because of insufficient controls. Many simple and commonly available controls such as restricting permissions, regular system audits, and robust staff training could have prevented the attack.
Detecting Supply Chain Attacks
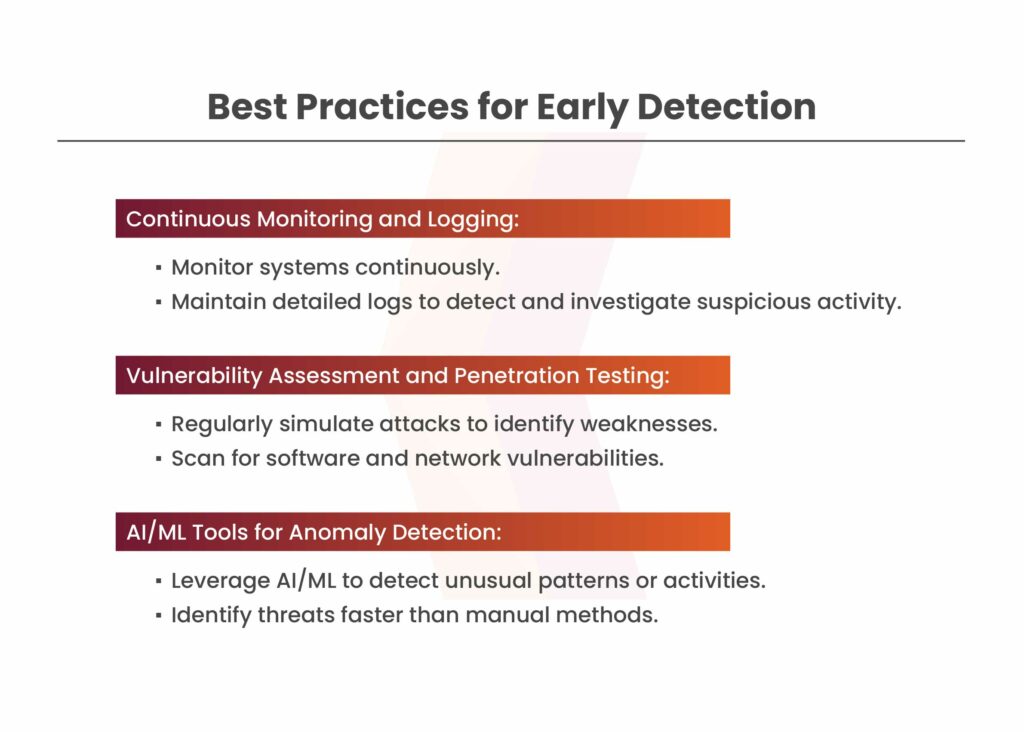
Every organization must be aware of the signs of a possible attack and must implement the best practices for early detection. Given below are some of the Key Indicators of Compromise (IoCs):
Strange Network Activity:
If an organization’s devices or systems start transferring unusually large amounts of data to unfamiliar servers or locations, it might indicate that an attacker is trying to steal sensitive information or disrupt operations.
Unusual Software Behavior:
When trusted software used in the organization begins acting abnormally such as crashing frequently, accessing sensitive files it normally wouldn’t, or connecting to unknown servers, it could signal that the software has been compromised. This might happen if an attacker has manipulated the software to spy on the organization, steal data, or disrupt business operations.
Mitigating Supply Chain Attacks
Organizations can mitigate the supply chain attack in the following ways:
Farseeing Measures
Vetting and Auditing Third-Party Vendors:
- Before working with external partners, check their security practices thoroughly to ensure they meet your standards.
- Regularly review their performance to spot and fix potential issues.
Implementing Strict Supply Chain Security Policies:
- Set clear rules and guidelines for everyone involved in your supply chain.
- These policies ensure security at every step, from sourcing to delivery.
Technical Defenses
Secure Code Signing:
- Use digital signatures to verify that software updates or applications come from a trusted source.
- Ensure that they have not been tampered with.
Zero Trust Architecture in Supply Chain Environments:
- Assume nothing and verify everything.
- Every user, device, and application must prove its identity and permissions before accessing resources, regardless of location.
Incident Response Planning
Steps to Take During and After an Attack:
- Develop a clear plan highlighting immediate actions.
- Take action accordingly to contain the damage, investigate the cause, and restore operations.
Maintaining Business Continuity and Recovery Plans:
- Ensure your organization can keep running during a crisis.
- Have backup systems and processes in place to recover quickly and minimize downtime.
Compliance Landscape
Compliance is important in supply chain security. It is about following rules, standards, and best practices to protect your organization and its partners. Achieving compliance protects your business, helps build trust, enhances reputation, improves risk management, and avoids penalties. In short, compliance is like having a security checklist, it keeps everyone accountable, reduces risks, and ensures smooth operations in the supply chain.
Some of the relevant regulations and standards related to supply chains are ISO/IEC 27001, NIST Cybersecurity Framework (CSF), SOC 2 (Service Organization Control 2), GDPR (General Data Protection Regulation), and HIPAA among others. The need for compliance may differ from industry to industry.
Get in!
Join our weekly newsletter and stay updated
How Kratikal Can Help Prevent Supply Chain Attacks?
Kratikal offers VAPT services as well as is empanelled by CERT-In as an auditor. Organizations that are at risk of supply chain attacks can perform a Secure Code Review, Root Cause Analysis, or both. Secure Code Review helps organizations examine their software code to look for and fix security issues before it is used. This is important because it ensures the code used is free from any loopholes. Thus, it will save the company from data theft, unauthorized access, or system crashes. If an organization has already been a victim of a supply chain attack, one of the most appropriate cybersecurity measures is performing Root Cause Analysis (RCA). It will help them find the main reason behind the attack and will stop it from happening again.
When it comes to being compliant, Kratikal can help achieve compliance by performing audits. It follows the NIST Cybersecurity Framework (CSF) for managing cybersecurity risks, including supply chain vulnerabilities. Organizations with supply chain security risks can perform audits for ISO/IEC 27001, SOC 2, GDPR, HIPAA compliances with Kratikal.
FAQs
- How can an organization prevent supply chain attack?
To catch supply chain attacks early, stay alert to strange network or software activity. Use monitoring tools, simulate attacks to find weaknesses, and employ advanced AI-driven tools to identify anything unusual.
- What are the two major risks in supply chain?
The supply chain has multiple internal and external risks. Some of the major risks include cybersecurity, operational, geopolitical, financial, environmental, and supply-and-demand.
- How can an organization detect a supply chain?
Continuous monitoring, detailed logging, vulnerability scanning, vulnerability management, and using AI-driven tools for anomaly detection can help organizations detect supply chain early.








Leave a comment
Your email address will not be published. Required fields are marked *