Ensuring robust cloud application security within a cloud environment is a vital component of any cloud ecosystem. It empowers businesses to enhance their agility while mitigating potential security risks. Essential cloud application security testing safeguards hosted techniques, controls, and policies using specified patterns and techniques. According to Gartner, the global market for public cloud services is anticipated to increase by 20.2% in current dollars (20.1% in constant currency) in 2023.
The blog is to guide through comprehensive cloud security testing best practices, ensuring that the organization takes the necessary measures towards establishing a secure cloud environment. Let’s explore the value of cloud application security, emphasizing prevalent risks and providing effective solutions.
Table of Contents
What is Cloud Application Security Testing?
It is a critical process that focuses on evaluating and ensuring the security of applications and systems operating within cloud environments. It requires a thorough examination to detect vulnerabilities, risks, and threats impacting cloud applications, data, and overall infrastructure security and integrity. Testing detects, mitigates security risks, secures data, ensures compliance, and boosts cloud app resilience to cyber threats. Thorough assessments and security measures ensure confident cloud utilization, upholding robust standards and safeguarding valuable digital assets for organizations.
Book Your Free Cybersecurity Consultation Today!
Cloud Application Security Testing Challenges
Understanding the inherent challenges in cloud application security testing is vital for effective risk mitigation and secure deployment. Here are the key challenges to consider:
Cloud Misconfigurations:
Improper system configuration can be a security risk, allowing network access and unauthorized entry to valuable resources. These misconfigurations often stem from inadequate security awareness during cloud application security testing system setup.
Privacy and Confidentiality of Data
Organizations often handle unprotected sensitive data, risking reputational harm if disclosed due to a lack of compliance safeguards. While migrating data to the cloud offers numerous advantages, it also introduces notable security apprehensions. Inadequate security in cloud storage accessible via public networks can expose data, making it easily accessible to malicious actors.
Fraudulent use of Credentials
Malicious actors frequently exploit cloud apps and platforms in cyber attacks. Hackers have numerous methods to compromise employee credentials for cloud services. Protecting identities in the cloud poses a significant challenge for organizations, as compromised identities can jeopardize the privacy and security of cloud-based data.
Compliance Requirements
The majority of data protection regulations necessitate organizations to showcase effective limitations on access to sensitive data (e.g., credit card information or medical records). Isolation in the organization’s network ensures only authorized personnel access protected data, achieved through physical or logical measures.
Cloud setups offer a restricted view and control of the infrastructure, differing significantly from conventional data centers. This variance can heighten the challenge of fulfilling and showcasing these compliance requisites in a cloud environment.
Get in!
Join our weekly newsletter and stay updated
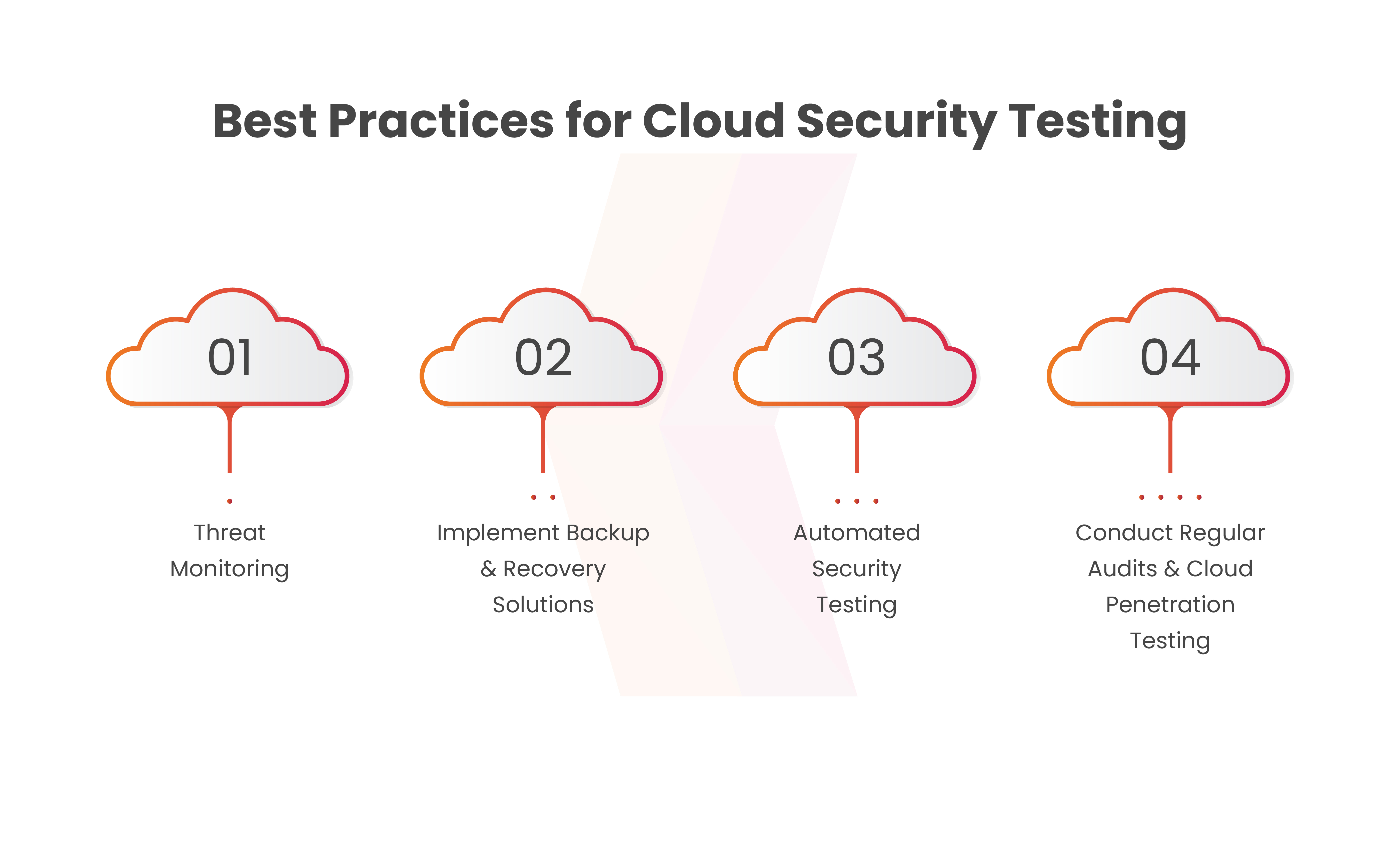
Cloud Application Security Testing Best Practices
Prioritizing robust security measures during the development and deployment of cloud applications is essential. Here are the key best practices to ensure effective cloud security testing:
Threat Monitoring
Continuous real-time monitoring is paramount for swiftly identifying and responding to any unusual activities. With the evolving cyber threats and data breaches, utilizing threat intelligence data becomes essential to outpace malicious attackers. Embracing this effective approach allows your cloud security team to promptly detect threats, respond instantly, and mitigate the impact of potential cyberattacks.
Implement Backup and Recovery Solutions
Implementing backup and recovery is critical for ensuring data availability in reducing risks of loss from ransomware, deletion, alterations, or hardware issues.
Organizations have the flexibility to adopt diverse approaches for backup, recovery, and archiving. Utilizing automated backups and lifecycle policies aids in preserving retrievable copies, while archives provide a secure repository for storing accessed data. Recovery procedures guide data restoration during cyber threats, designating specific roles to oversee the restoration process effectively.
Automated Security Testing
Automation allows for the rapid and repetitive execution of security tests, which is especially critical in today’s dynamic and digital landscape where manual testing alone may not be sufficient. Automated Security Testing offers several benefits, including increased testing coverage, faster identification of vulnerabilities, early detection of security flaws, and the ability to integrate security testing seamlessly.
Conduct Regular Audits and Cloud Penetration Testing
Penetration testing involves a controlled and authorized simulated attack carried out by ethical hackers to uncover and address security weaknesses. Its purpose is to evaluate the effectiveness of security controls within your cloud infrastructure and to mitigate any vulnerabilities and deficiencies detected. Routine audits are a fundamental security measure and are often mandated by regulatory bodies to ensure compliance and security. They play a crucial role in validating the adequacy of your cloud security measures, including those configured by your cloud service provider.
Why Cloud Penetration Testing is essential?
Organizations promptly acknowledge the necessity of securing cloud applications throughout their entire life cycle, encompassing development, testing, deployment, and maintenance. Cloud applications are at risk of unauthorized access, data breaches, and cyber threats. Moreover, these applications commonly integrate with a variety of services, APIs, and third-party components, expanding the potential attack surface. It’s imperative to establish robust measures such as effective identity management, encryption, access controls, monitoring sensitive data, upholding compliance, and combating evolving threats in the dynamic cloud landscape.
Conclusion
Cloud application security testing is vital, focusing on assessing and enhancing the security of cloud-based applications, data, and systems. A comprehensive examination identifies vulnerabilities and threats, enabling proactive risk detection and measures to safeguard sensitive information and ensure compliance. Adherence to best practices, including continuous threat monitoring, security testing, and audits, is crucial in overcoming cloud challenges effectively.
Adhering to best practices in cloud application security testing is crucial for organizations to mitigate cyber threats effectively. Kratikal a CERT-In empanelled auditor provides extensive cybersecurity solutions designed to safeguard businesses from a variety of cyber attacks, with a specific emphasis on securing web applications against potential risks. By partnering with Kratikal, businesses can identify and address security vulnerabilities proactively, preventing malicious hackers from exploiting these weaknesses.









Leave a comment
Your email address will not be published. Required fields are marked *