Cloud misconfigurations have emerged as a major security threat. This led to over 400,000 buckets and 10.4 billion data exposed to the public. Are your sensitive data and personal files truly secure in the cloud? The development of cloud storage has undeniably transformed the way firms protect their digital assets. However, great convenience comes with enormous risk.
In this blog, we will look at the consequences of cloud misconfigurations. Further, we will understand the role of cloud security testing in preventing ransomware attacks.
Table of Contents
The Cloud Misconfiguration Challenge
Organizations seek high availability and performance by transferring their digital assets to cloud storage in today’s web-centric environment. One critical issue that is at times missed is the right design of cloud buckets. These buckets store essential corporate assets like private data, sensitive databases, and source codes. While cloud providers ensure the overall safety of these files within their network, users are responsible for configuring access privileges.
Get in!
Join our weekly newsletter and stay updated
Unfortunately, as a result of human error, cloud buckets can become publicly accessible. This potentially leads to the exposing of private data. Cloud storage misconfigurations contributed significantly to 13% of data breaches, according to Verizon’s 2022 Data Breach Investigations Report. These misconfigurations are used by hackers to gain unauthorized access to buckets containing important information. Such data breach violations have severe consequences and can end in harmful ransomware attacks.
The Risk of Open Search for Public Buckets
Open-source programs and platforms have further exacerbated the issue of cloud misconfigurations. These platforms allow anyone to scan millions of public buckets simultaneously using certain keywords. The buckets generally follow a common naming convention, making them easily detectable. Hacker utilizes these platforms, such as GrayhatWarfare, to gather information on publicly available buckets for their malicious activities.
The availability of a comprehensive collection of public bucket data in one place serves as an attractive opportunity for threat actors. It becomes a potential focal point for cyberattacks, including ransomware attacks, as threat actors search for vulnerable buckets and exploit them for financial gain.
Implications of Cloud Misconfigurations
The consequences of public bucket exposures are broad. The situation becomes worse with the availability of platforms that centralize public bucket searches. While these platforms are meant to raise awareness about the issue, they unintentionally generate resources for threat actors. A recent event involving Microsoft’s AI research team is an excellent example in point. While sharing an open-source training data bucket on GitHub, they inadvertently exposed 38 terabytes of sensitive data. This vulnerability was caused by an incorrectly set Azure Shared Access Signature (SAS) token during the URL construction procedure.
These bucket discloses have revealed important configuration information and backup disc images. This further poses a substantial risk. When combined with current vulnerabilities, they have the potential to enable additional cyberattacks, including ransomware operations.
Cloud Safety: Key Tips and Strategies for Secure Data
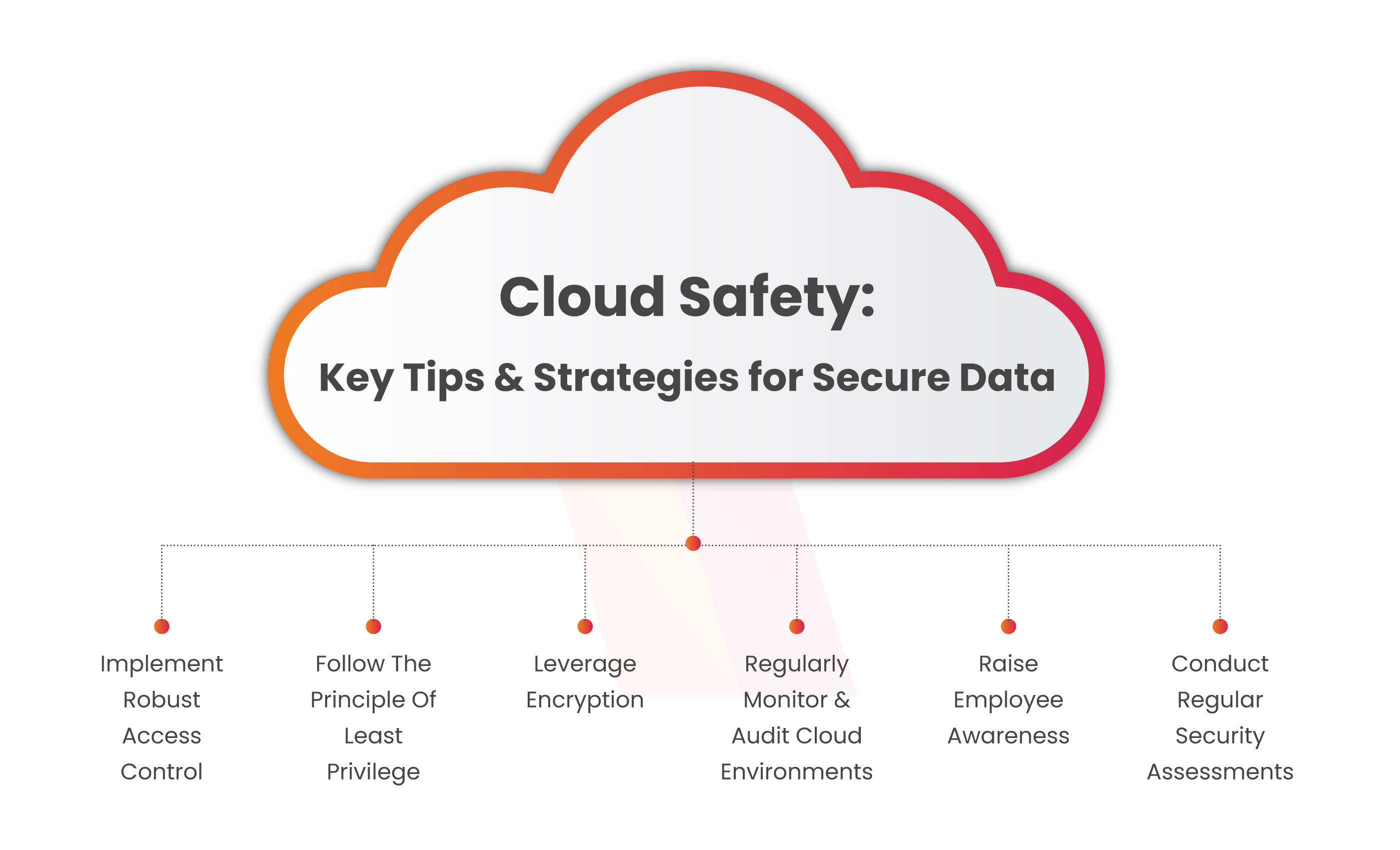
Misconfigurations in the cloud can have severe consequences for businesses. This could lead to unauthorized access to sensitive data and data breaches. To limit the risks associated with cloud misconfigurations, organizations must follow guidelines to maintain the security of their digital assets. Some of the key tips and strategies for protecting data are provided below:
Implement robust access control: Properly configure access rights and permissions for cloud storage buckets, ensuring that only authorized individuals or systems have access to sensitive data. Regularly review and update access controls to reflect changes in the organization’s structure and personnel.
Follow the principle of least privilege: Grant the minimum level of access necessary to perform the required tasks. Avoid providing unnecessary permissions, as this can increase the risk of data exposure in case of a misconfiguration.
Leverage encryption: Encrypt data stored in the cloud to add an additional layer of security. Encryption ensures that even if unauthorized access occurs, the data remains unintelligible and unusable.
Regularly monitor and audit cloud environments: Implement continuous monitoring and auditing of cloud storage buckets to detect any misconfigurations or unauthorized access promptly. Tools like cloud security modules can provide real-time alerts and insights into potential threats.
Raise employee awareness: Educate employees about the risks of misconfigurations in the cloud and train them on proper security practices. Encourage them to follow best practices and report any suspected misconfigurations or security incidents.
Conduct regular security assessments: Conduct periodic security assessments (cloud penetration testing) of cloud environments to identify potential vulnerabilities and misconfigurations. This can help address any security gaps proactively and prevent future incidents.
Mitigating the Risk: Cloud Security Testing
Organizations must prioritize cloud security testing to prevent harmful ransomware attacks triggered by cloud misconfigurations. Preventative steps should be taken to discover vulnerabilities in cloud environments and ensure that access rights and permissions are properly configured. Different approaches to security testing, such as black, grey, and white box testing, can help companies improve their security. Continuous monitoring of cloud settings for odd activity and potential security threats is part of a full cloud security testing approach.
Ensuring Cyber Security with Kratikal
In a time where cloud usage is rising in addition to an increasing number of human errors that expand the attack surface, the possibility of cloud misconfigurations and subsequent ransomware attacks remains a significant concern. As companies attempt to preserve their valuable assets and protect against cyber threats, cooperating with a reputable cybersecurity service such as Kratikal becomes ever more essential.
Book Your Free Cybersecurity Consultation Today!
Kratikal, a CERT-In empanelled auditor, provides comprehensive cloud security testing services to enterprises. Our experts tailor VAPT services and Compliance for companies of all scales to ensure overall cyber resilience. Our knowledge of identifying vulnerabilities, establishing access privileges, and conducting regular security audits can assist firms in mitigating the risks associated with misconfigurations in cloud data. Organizations can securely safeguard their data from ransomware attacks. Let’s maintain a strong security posture by adopting a proactive approach to cloud security.
Ref: socradar.io/over-400k-buckets-and-104b-files-are-public-due-to-cloud-misconfigurations








Leave a comment
Your email address will not be published. Required fields are marked *