How well is the field of software supply chain security evolving in the year 2024? A BlackBerry research presented recently shows that more than three-quarters of software supply chains have been attacked over the past months. Supply chain attack exploits the trust relationships between organizations by taking advantage of them. There is always a certain degree of implicit trust in others; organizations’ software operates in each other’s networks or works as vendors for other organizations. That is why hackers focus on this link of the chain of trust, as it enables them to enter several organizations and commit cyber attacks. In this blog, we will explore the supply chain attack on Polyfill.io service and how organizations can prevent themselves from supply chain attacks.
Table of Contents
What Happened in Polyfill?
Google has blocked ads for over 110,000 websites embedding the Polyfill.io JavaScript library after a Chinese company acquired the domain and the code was modified to redirect users to malicious sites. Polyfill.io, widely used by many websites, supports modern web functions for older browsers, making it a critical component. However, the project’s purchase by the Chinese CDN company Funnull in February 2024 has raised serious concerns about supply chain security. The original Polyfill.io creator urged website owners to remove the library, stating it is no longer necessary for most sites.
The screenshot indicates that over 100,000 websites may be impacted by this Polyfill supply chain vulnerability. Adding affected polyfill to the website can impact user and organization security.
Kratikal recommends removing immediately the vulnerable polyfill code and using an alternate polyfill fork such as Cloudflare polyfill as the hijacked code has protections against reverse engineering and can activate malware on certain mobile devices.
This attack highlights the risks of relying on third-party services that could be vulnerable to takeover and manipulation.
Get in!
Join our weekly newsletter and stay updated
Impact of the Attack
The Pollyfill.io supply chain attack has had significant negative consequences across multiple fronts.
Impact on Websites
- Over 110,000 websites embedding the Polyfill.io library have been affected by the attack.
- The hijacked code redirects users from these sites to malicious domains serving malware, sports betting
- Website owners must urgently remove Polyfill.io and migrate to alternative endpoints to prevent further compromise.
Impact on Users
- Visitors were affected websites face risks of exposure to malware, scams, and inappropriate content.
- The malicious redirects could lead to identity theft, financial fraud, and other cyber attacks.
Impact on Pollyfill.io
- The project’s acquisition by a Chinese company damaged trust in the library.
- The original creator has disavowed the project, stating it is no longer necessary for most sites.
- Polyfill.io’s reputation and adoption will likely suffer long-term consequences.
Impact on Web Security
- The attack highlights the risks of relying on third-party services that could be vulnerable to supply chain compromise.
- It underscores the need for website owners to carefully vet and monitor the security of all components in their tech stack.
- The incident may prompt changes in how browsers handle third-party scripts to prevent similar attacks.
How to Prevent Supply Chain Attacks?
The Polyfill supply chain attack highlighted the severe impact of such threats and revealed significant weaknesses in traditional defense mechanisms. Despite the sophistication of the SolarWinds breach, organizations can still adopt effective defense strategies to strengthen their digital supply chain security. Below is the list of strategies to prevent supply chain attacks.
Implementation of Zero Trust Architecture
A Zero Trust Architecture (ZTA) operates under the assumption that all network activity is malicious by default. Each connection request grants access to intellectual property only after meeting a stringent set of policies. At its core, a ZTA comprises a Policy Engine (PE), a Policy Administrator (PA), and a Policy Enforcement Point (PEP).
The Trust Algorithm establishes rules, and the Policy Engine determines whether to allow network traffic based on them. Also, the Policy Administrator relays the Policy Engine’s decision (allow or deny) to the Policy Enforcement Point. Policy Enforcement Point serves as the final gatekeeper, blocking or permitting network requests according to the Policy Engine’s decision.
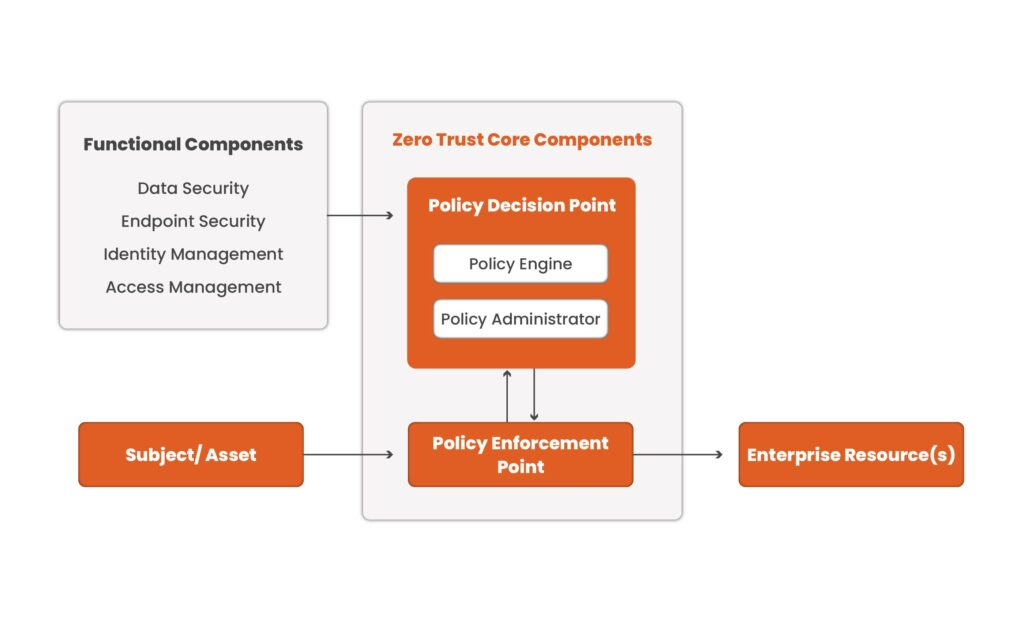
You can tailor the Zero Trust Architecture (ZTA) framework to fit the setup requirements of any ecosystem. This approach can also secure remote endpoints, which have become a common target for attacks following the widespread adoption of remote work.
Identification of Potential Threats
An insider threat isn’t always motivated by malicious intent. Insider threats are difficult to identify. They’re also significantly more risky because they can provide threat actors with the specific access they require to facilitate a software supply chain attack. Regular employee feedback surveys and an open and supportive work culture will address concerns before they cultivate hostile insider threats.
Minimize Access to Sensitive Data
First, identify all access points to sensitive data. This will allow you to track all employees and vendors currently accessing your sensitive resources. The more privileged access roles there are, the larger the attack surface, so it’s crucial to minimize these accounts. Vendor access requires particular scrutiny due to their high risk as initial targets in supply chain attacks. Document all vendors with access to your sensitive data and their respective access levels. Use questionnaires to determine how each vendor processes and protects your sensitive data. Service providers should only have access to the minimal amount of sensitive data needed to perform their services.
Kratikal has always recommended continuous monitoring to minimize any risk associated with the supply chain. Contact us for VAPT Testing services to mitigate supply chain attacks.
Book Your Free Cybersecurity Consultation Today!
Conclusion
The Polyfill.io supply chain attack underscores the urgent need for organizations to reassess and strengthen their cybersecurity measures. By exploiting trust relationships between organizations, hackers can infiltrate multiple targets through a single point of compromise. This incident highlights the critical importance of implementing a Zero Trust Architecture, rigorously vetting third-party vendors, and minimizing access to sensitive data. Continuous monitoring and proactive security measures are essential to mitigating supply chain risks. For expert guidance and comprehensive security solutions. Kratikal’s VAPT Testing services to safeguard your organization against evolving cyber threats. Stay vigilant, and prioritize security to protect your digital ecosystem from future attacks.
FAQs
- How do supply chain attacks work?
For a supply chain attack to be effective, hackers insert malicious code into software or compromise network protocols or components. Once malicious actors identify a vulnerability, they exploit it to gain access to critical digital resources.
- How to detect a supply chain attack?
A supply chain attack can be detected by a monitoring system that identifies abnormal behavior on devices, applications, and systems.









Leave a comment
Your email address will not be published. Required fields are marked *