Ransomware attacks have become increasingly sophisticated and costly, with LockBit 3.0 emerging as a formidable adversary. This latest iteration of ransomware is not just a technical challenge but a financial nightmare, costing businesses millions in ransom payments, recovery expenses, and downtime. As organizations struggle with relentless cyber threats, understanding the mechanics, impacts, and preventive measures against LockBit 3.0 is crucial.
In February 2024, several ransomware groups were active. Here, we highlight trends related to the top five ransomware groups.
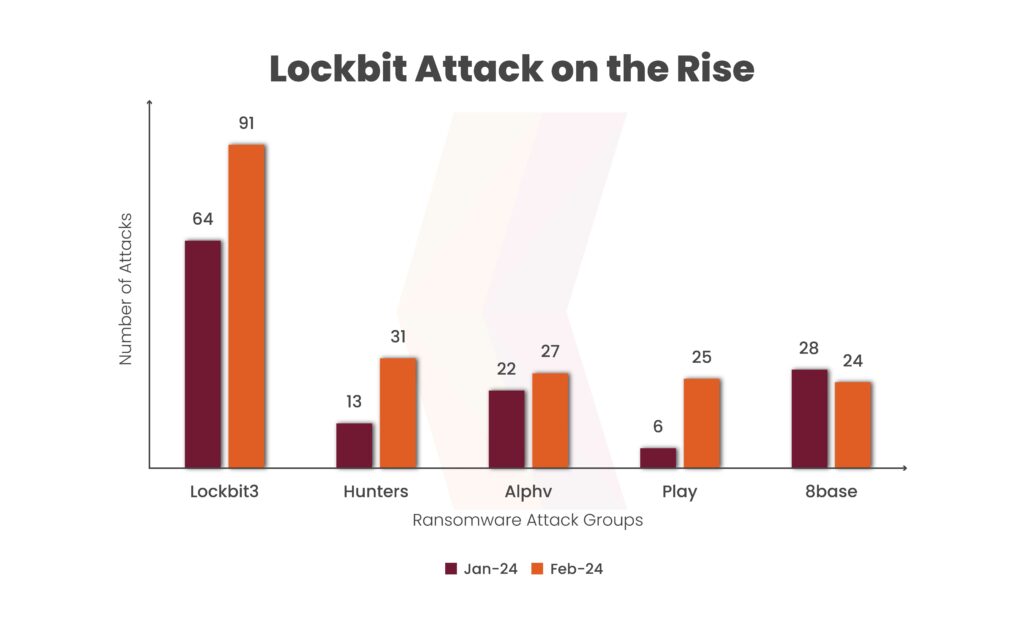
From January to February 2024, LockBit3 experienced a 42.2% rise in victims, while Hunters saw a dramatic increase of 138.5%. Alphv and Play showed moderate increases of 22.7% and 316.7%, respectively, likely due to failed ransom negotiations. Conversely, 8Base saw a 14.3% decrease in victims, possibly due to successful negotiations or reduced activity.
Table of Contents
What is Ransomware LockBit 3.0?
LockBit 3.0 is ransomware that encrypts files on a victim’s computer or network and makes them unavailable unless a ransom is paid for the decryption key. This advanced version of LockBit uses complex encryption algorithms to target certain file types such as documents, photos, videos, and databases. Notably, LockBit 3.0 has improved its capabilities, allowing it to avoid detection and spread quickly over a network. It can be transmitted via a variety of attack routes, including malicious email attachments, hijacked websites, and often demands cryptocurrency ransom payments to disguise the transaction trace.
The consequences of a LockBit 3.0 attack are severe, posing significant threats to individuals, businesses, and organizations by causing substantial financial losses, data breaches, and operational disruptions. Recovery options are limited to paying the ransom (which is not recommended) or restoring files from secure backups. To protect against ransomware, ensure regular software updates, use reputable security software, maintain secure backups, be cautious with email attachments and links, and educate users on safe online practices.
Book Your Free Cybersecurity Consultation Today!
Recent LockBit Ransomware Attack
A ransomware attack using the LockBit 3.0 malware has severely disrupted numerous critical government digital services in Indonesia. The attack targeted the country’s Temporary National Data Centre (PDN), paralyzing systems and data across hundreds of central and local government agencies. Services impacted include immigration, licensing, and procurement, forcing some agencies like the Directorate General of Immigration to revert to manual, paper-based processes and causing long queues at airports.
Cybersecurity experts have highlighted this incident as a wake-up call, exposing the vulnerability of Indonesia’s digital infrastructure. They emphasize the urgent need for the government to strengthen its overall cybersecurity strategy and incident response capabilities. This should include advanced physical and network security measures, robust threat detection and monitoring, comprehensive employee training, and improved collaboration between the public and private sectors. While the government has refused to pay the $8 million ransom demanded by the attackers, experts caution that this must be complemented by a more proactive and resilient approach to protecting critical government data and services from future cyber threats.
Impact of LockBit Ransomware
The impact of LockBit 3.0 ransomware on organizations is intense causing severe operational disruptions, significant financial losses, and potential reputational damage. Once entered, this malware encrypts critical files, rendering them inaccessible and effectively paralyzing business operations. Organizations are then faced with the difficult choice of paying a hefty ransom or attempting to restore data from backups, which may not always be up-to-date or available. The downtime associated with a LockBit 3.0 attack can lead to substantial revenue losses and erode customer trust.
Additionally, the costs involved in responding to the attack, including IT recovery efforts, legal fees, and potential fines for data breaches, can further strain an organization’s resources. Overall, the impact of LockBit 3.0 ransomware underscores the urgent need for robust cybersecurity measures and proactive incident response planning.
Get in!
Join our weekly newsletter and stay updated
Preventive Measures for LockBit Ransomware
Here are some practices that can help prepare organizations for ransomware attacks:
Install Antivirus and Firewalls
Comprehensive antivirus and anti-malware software are essential for defending against ransomware, as they can scan, detect, and respond to cyber threats. However, configuring your firewall is also crucial since antivirus software only works internally and can only detect attacks once they are already in the system.
Firewalls serve as the first line of defense against incoming external attacks, protecting against both software and hardware-based threats. They are vital for any business or private network because they can filter out and block suspicious data packets from entering the system.
Ransomware can rapidly spread throughout a network, making it crucial to limit its reach during an attack. Network segmentation helps by dividing the network into smaller segments, allowing the organization to isolate the ransomware and prevent it from spreading to other systems.
Each subsystem should have its own security controls, firewalls, and unique access to protect against ransomware reaching target data. This segmented access not only prevents the ransomware from affecting the main network but also provides the security team with more time to identify, isolate, and eliminate the threat.
Application Whitelisting
Ransomware can quickly spread throughout a network, so it’s essential to limit its reach during an attack. Network segmentation can help by dividing the network into smaller segments, allowing the organization to isolate the ransomware and prevent it from spreading to other systems.
Each subsystem should have its own security controls, firewalls, and unique access to protect against ransomware reaching target data. This segmented access not only stops the ransomware from impacting the main network but also gives the security team more time to identify, isolate, and remove the threat.
Endpoint Security
Securing endpoints should be a top priority for growing businesses. As businesses expand and the number of end-users increases, the proliferation of endpoints such as laptops, smartphones, and servers introduces more security vulnerabilities. Each remote endpoint represents a potential entry point for cyber attackers to access sensitive information or compromise the main network.
Whether operating a home-based business or part of a larger company, it’s crucial to deploy Endpoint Protection Platforms (EPP) or Endpoint Detection and Response (EDR) for all network users. These technologies empower system administrators to monitor and enhance security measures across each remote device. EDR, in particular, offers advanced capabilities focused on swiftly responding to and neutralizing immediate threats that breach the network.
Kratikal’s endpoint network security services along with compliance services, offer comprehensive protection for your digital data. This includes not only, vulnerability management and, threat intelligence but also ensures that organizations can maintain a robust defense against cyber threats.
Conclusion
The threat posed by LockBit 3.0 ransomware is not just a technical challenge but a significant financial and operational risk for organizations worldwide. The recent attack on Indonesia’s government services underscores the devastating impact ransomware can have on critical infrastructure and public trust. As businesses and governments face increasingly sophisticated cyber threats, proactive cybersecurity measures are paramount. This includes comprehensive antivirus and firewall protections, network segmentation to contain and isolate ransomware incidents, application whitelisting to control system access, and robust endpoint security solutions.
Moreover, fostering a culture of cybersecurity awareness and readiness among employees is essential to mitigate risks effectively. By implementing these preventive measures and maintaining resilient incident response strategies, organizations can better safeguard against the devastating consequences of ransomware attacks and ensure continuity in the face of evolving cyber threats.
FAQs
- How does LockBit 3.0 ransomware work?
LockBit 3.0 attempts to spread across a victim network. It does this by using a preconfigured list of credentials hardcoded at compilation time or a compromised local account with elevated privileges.








Leave a comment
Your email address will not be published. Required fields are marked *