
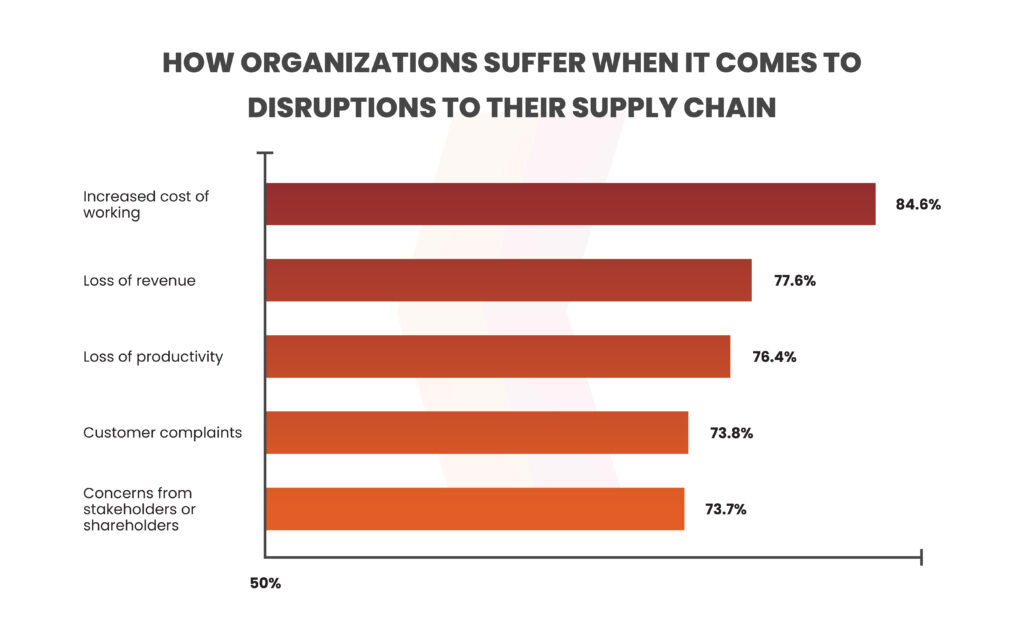
According to the State of Software Supply Chain Security Report, there has been a 1,300% increase in the discovery of malicious packages on open source over the last 3 years. Below are some statistics that include the disruptions organizations suffer when it comes to supply chain attacks.
Cyber attackers constantly refine their tactics to achieve significant outcomes. The emergence of models like Ransomware-as-a-Service exemplifies this trend. However, the cyberattack efficiency may be epitomized by the development of supply chain attacks. Recently Cloudflare faced a supply chain attack that impacted Atlassian’s bitbucket, confluence, and Jira platform. To know more about supply chain attacks and what happened at Cloudflare continue to read the blog.
Table of Content
How Was the Cloudflare System Affected?
Cloudflare, an industry leader in internet security and performance solutions, recently encountered a cyberattack stemming from a well-publicized Okta supply chain breach. The scope of the incident showcased Cloudflare’s Atlassian suite, comprising Bitbucket, Confluence, and Jira applications. The attack was traced back to a suspected nation-state actor aiming for long-term persistence within Cloudflare’s infrastructure. While the adversaries failed to achieve their objectives, Cloudflare promptly responded by engaging with CrowdStrike, replacing more than 5,000 production credentials, and performing comprehensive forensic investigations across almost 5,000 systems.
Broadly speaking, Okta experienced previous security breaches involving its customer support case management system, which resulted in the privacy of numerous consumers being compromised. Consequently, the Cloudflare instance is only one facet of a complex issue that underscores the vulnerabilities existing in today’s digital ecosystems.
Book a Free Consultation with our Cyber Security Experts

Preventive Measures for Supply Chain Attacks
Here are some general steps that companies can take to enhance their cybersecurity posture:
Implementation of Honeytokens
Honeytokens serve as virtual alarms within organizational networks, signaling potential threats. By posing as sensitive data, these stolen resources make it difficult for attackers to enter the organization’s network, and they believe that valuable assets have been found. Once these dummy resources are accessed, it triggers alerts, promptly notifying the organization of a potential breach. This proactive approach not only detects breach attempts but also provides insights into the attackers’ methods. Filled with this intelligence, organizations can identify the targeted resources and deploy tailored incident response strategies for each cyberattack method. In cases where attackers operate beyond traditional defenses like firewalls, honeytokens may even reveal their location and identity. To bolster defenses against supply chain attacks, it is recommended that vendors integrate honeytoken systems.
Enhance Privileged Access Management
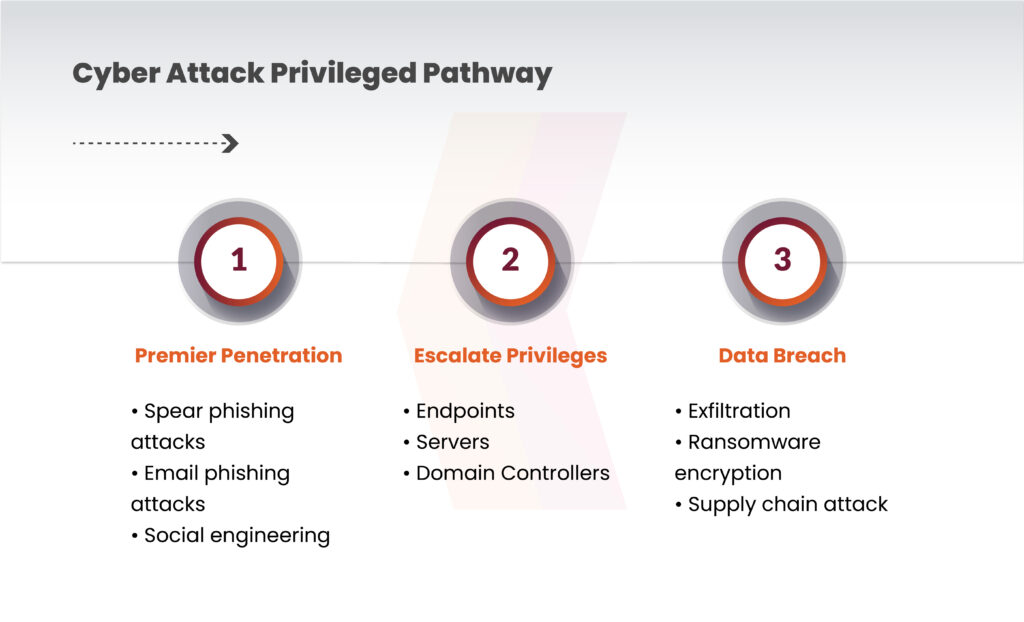
Upon breaching a defense, cyber attackers typically pivot laterally within the ecosystem to locate privileged accounts. Privileged accounts are targeted as they possess exclusive access to sensitive resources. Once identified, attackers attempt to access sensitive data through these accounts.
To prevent the breach attempts, including supply chain attacks, can be achieved by obstructing an attacker’s advancement along this pathway. An efficient Privileged Access Management (PAM) framework disrupts this typical attack route. However, to enhance defense against supply chain attacks, it’s imperative to safeguard the PAM itself. Both external and internal defenses should shield the PAM.
Identification of Potential Insider Threats
Hostile insider threats present a unique challenge in detection and are especially perilous as they can grant threat actors the precise access required to orchestrate a software supply chain attack. Implementing regular feedback via surveys and fostering an environment of openness and support are effective measures for addressing concerns before they escalate into hostile insider threats.
Continuous Monitoring of Supply Chain Risks
Monitoring of security risks such as data breaches, security incidents, and harmful software injections is essential in an organization’s supply chain. Creation of an incident response plan in case of a security breach plays a vital role in monitoring the supply chain risks. Kratikal has always recommended continuous monitoring to minimize any risk associated with the supply chain.
These prevention measures are not permanent solutions to prevent supply chain attacks it is recommended to implement proper compliance, controls, and firewall management and an external security audit to make sure that the risk associated with supply chain attacks is almost non-existent. However, the above-suggested preventive measures can be used to minimize the risk.
Conclusion
The growing number of attacks in the supply chain presents enormous obstacles to businesses’ cybersecurity posture. A recent Cloudflare-related event serves as a reminder of the intricacy of these threats and how they might affect connected digital ecosystems. In order to address these challenges organizations take a proactive approach to cybersecurity and implement strong preventive measures.
Critical steps in reducing the risks connected with supply chain attacks include the use of honeytokens, improving privileged access management (PAM), and spotting possible insider threats. These strategies not only bolster defenses against external threats but also address vulnerabilities within organizations’ internal environments.
FAQs
Q1. How are supply chain attacks executed?
Ans: Hackers insert malicious code into the software or find different ways to compromise network protocols. Once malicious actors identify a hacking opportunity, they exploit it to gain access to vital digital assets.
Q2. What are the types of supply chain attacks?
Ans: The types of attacks include:
- Pre-installed malware
- Ransomware
- Stolen certificates
- Firmware attacks

