Forbes predicts that cyber threats will cost the world an astonishing $10.5 trillion annually by 2025. With a growing range of increasingly alarming cybersecurity threats on the horizon, businesses must prioritize safeguarding themselves against the ever-evolving tactics of hackers.
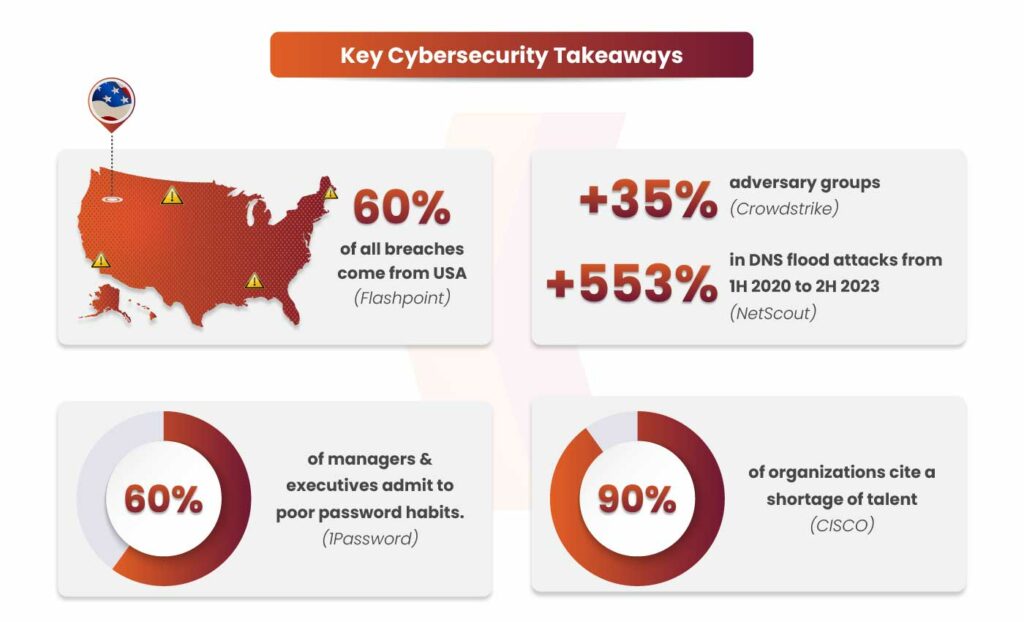
This insight is derived from analyzing specific statistics and interpreting reports from 1Password, Cisco, CrowdStrike, Flashpoint, Google Threat Analysis Group/Mandiant, NetScout, Pentera, and Sophos. If you’re still uncertain or believe that data breaches and hacks won’t affect you, this blog will explain why that assumption couldn’t be further from the truth.
Table of Contents
Why is it Essential to Invest in Cybersecurity?
With increasing cyber threats, protecting sensitive data, maintaining trust, and ensuring business continuity are more important than ever. As companies rely on cloud technology and interconnected systems, the risk of cyberattacks grows, making cybersecurity essential. Here’s why it matters:
Rising Dependency on Cloud Infrastructure
Initially, cloud technology was viewed as a minor component of IT infrastructure, handling only specific tasks. However, today’s reality is vastly different, with businesses heavily reliant on cloud technologies. The shift became particularly evident during the pandemic, as remote work surged, forcing companies to rapidly adopt cloud infrastructure to manage and store data over the past year.
As organizations increasingly depend on cloud providers like AWS, they can maintain agility and focus on their core operations. However, it’s crucial to recognize that cloud security is not the same as traditional cybersecurity within an organization. While cloud service providers (CSPs) offer infrastructure and system security measures, additional investments in tailored cybersecurity solutions are necessary to safeguard against external threats. These investments should go beyond the basic protections offered by CSPs and must be customized to suit the organization’s specific needs, industry, and risk profile. In short, relying solely on a CSP for security isn’t enough. Organizations seeking robust security must invest in additional, specialized cybersecurity measures.
Protection From Data Breaches
The impact of data breaches is significant, with the Ponemon Institute revealing that affected organizations face plummeting share prices, customer loss, and severe reputational damage. Data protection has become a critical issue requiring collective action from all levels of a company.
The WannaCry ransomware attack highlighted the dangers of unpatched vulnerabilities, spreading rapidly through un-updated assets and causing global disruption. This attack underscored the need for timely patches and robust incident response plans.
While a one-time cybersecurity risk assessment can identify security risks, continuous monitoring is essential to maintain security. A comprehensive Cybersecurity risk assessment should address key questions about data collection, storage, protection, and access.
To prevent such issues, it is crucial to:
- Conduct regular cybersecurity risk assessments.
- Implement continuous monitoring and timely updates.
- Ensure robust data protection and incident response strategies.
Get in!
Join our weekly newsletter and stay updated
Adhere to Legal Regulations
A compliance framework is crucial in any security program, underscoring the principle: “We Trust but Verify.” This means taking additional steps to ensure that policies, standards, laws, and regulations are properly followed and verified. This thorough approach to confirming compliance is vital. Whether at the individual or organizational level, achieving compliance enhances trust and credibility—there’s no substitute for diligently gathering evidence of adherence to required standards.
Securing electronic Protected Health Information (ePHI) remains a major challenge in the industry. According to HIPAA and the HITECH Act, health organizations must implement stringent access control measures for handling ePHI. This includes managing and monitoring access to data whether it’s at rest, in use, or in transit—a task that can be complex even for well-resourced organizations. These regulations are regularly audited within healthcare organizations to protect patient privacy and ensure compliance. Similarly, the Payment Card Industry Data Security Standards (PCI DSS) are designed to instill security and trust within the card industry. They provide essential guidelines for organizations that store, process, and transmit cardholder data.
The twelve domains of PCI DSS cover the full lifecycle of cardholder data—from its creation to its disposal. Key areas such as access control, encryption, and network security are addressed to ensure that assets are protected against threats and malicious activities.
Build Brands Goodwill
Customer satisfaction is crucial for any business. In today’s digital age, customers are increasingly aware of their rights and the importance of data privacy.
As they make transactions online, they expect protection against cyber threats such as phishing, identity theft, and other privacy breaches. Gaining and maintaining customer trust is essential for business success; research indicates that up to 40% of online shoppers will abandon a purchase if they have concerns about a website’s security. Implementing a robust cybersecurity system is vital to building and sustaining customer confidence.
Consider the case of ‘UberLeak,’ a hacker who posted stolen confidential information from Uber and Uber Eats on an online forum. The breached data reportedly included employee email addresses, corporate reports, and IT asset details from third-party vendors. The hacker also released archived source codes for mobile device management platforms used by the companies. This significant data breach highlights potential shortcomings in Uber’s cybersecurity measures, affecting their employees, customers, and service providers.
Avoid Financial Penalties and Litigation
No one wants to deal with fines or lawsuits, and data breaches can lead to both. Business owners should take proactive measures to safeguard their company’s sensitive information in the event of a breach. For instance, IBM data shows that the average cost of a data breach in the US has surged from $3.5 million in 2006 to $9.4 million in 2022—a nearly 170% increase over 16 years.
Government agencies can impose substantial fines on organizations that fail to adequately protect data. Additionally, even if fines are avoided, your company could face lawsuits from individuals or groups whose sensitive information was exposed. To mitigate these risks, familiarize yourself with relevant laws, regulations, and data security best practices. Ensure that all employees are aware of privacy policies and understand the importance of safeguarding personal customer information. By taking these precautionary measures, you can help prevent potential fines and legal actions resulting from data breaches.
Book Your Free Cybersecurity Consultation Today!
Cybersecurity: A Key Priority for Businesses Today
Cybersecurity is vital for businesses due to the growing sophistication and frequency of cyber threats. Protecting sensitive data, such as customer information, financial records, and intellectual property, is crucial, as data breaches can lead to significant financial losses and damage to reputation. Additionally, robust cybersecurity measures are essential for maintaining business operations and preventing costly downtime and disruptions. Compliance with regulations that mandate specific security standards is another critical reason for investing in cybersecurity, helping businesses avoid fines and legal issues. Furthermore, a strong cybersecurity stance builds customer trust, fostering loyalty and long-term relationships. Companies that prioritize cybersecurity also gain a competitive edge by focusing on their core operations without the distraction of cyber threats.
How can Kratikal Help Business in Cyber Security Services?
Kratikal offers a comprehensive suite of cybersecurity services designed to protect businesses from increasing cyber threats. Their end-to-end Vulnerability Assessment and Penetration Testing (VAPT) services thoroughly assess web applications, mobile apps, networks, cloud infrastructure, and codebases to identify and fix vulnerabilities. Kratikal also provides phishing simulations and security awareness training to educate employees, reducing the risk of breaches caused by human error. With real-time threat intelligence and monitoring, businesses can detect and respond to threats proactively, while Kratikal’s expert incident response team helps mitigate and recover from attacks. Additionally, Kratikal ensures compliance with key regulations like GDPR, HIPAA, and PCI DSS, helping businesses avoid fines and legal issues while maintaining customer trust. By partnering with Kratikal, businesses can enhance their cybersecurity, protect valuable data, and stay ahead of evolving cyber threats.
FAQs
- Why is cyber security so important?
Cybersecurity involves safeguarding internet-connected devices and services from malicious attacks by hackers, spammers, and cybercriminals. Organizations implement cybersecurity measures to defend against threats such as ransomware, identity theft, data breaches, and financial losses.
- What is the main purpose of cyber security?
Cybersecurity helps individuals and organizations minimize the risk of cyberattacks. Its primary purpose is to protect the devices we use, such as smartphones, laptops, tablets, and computers, as well as the online and workplace services we rely on, from theft or damage.








Leave a comment
Your email address will not be published. Required fields are marked *