Table of Contents
Introduction
In recent months, a threat to open-source repositories has emerged in the form of repository hijacking, commonly known as RepoJacking. RepoJacking involves a malicious actor intentionally taking over the account of an owner or maintainer who hosts a repository. By gaining access to the account, the attacker can inject malicious code into projects that use the repository as a dependency.
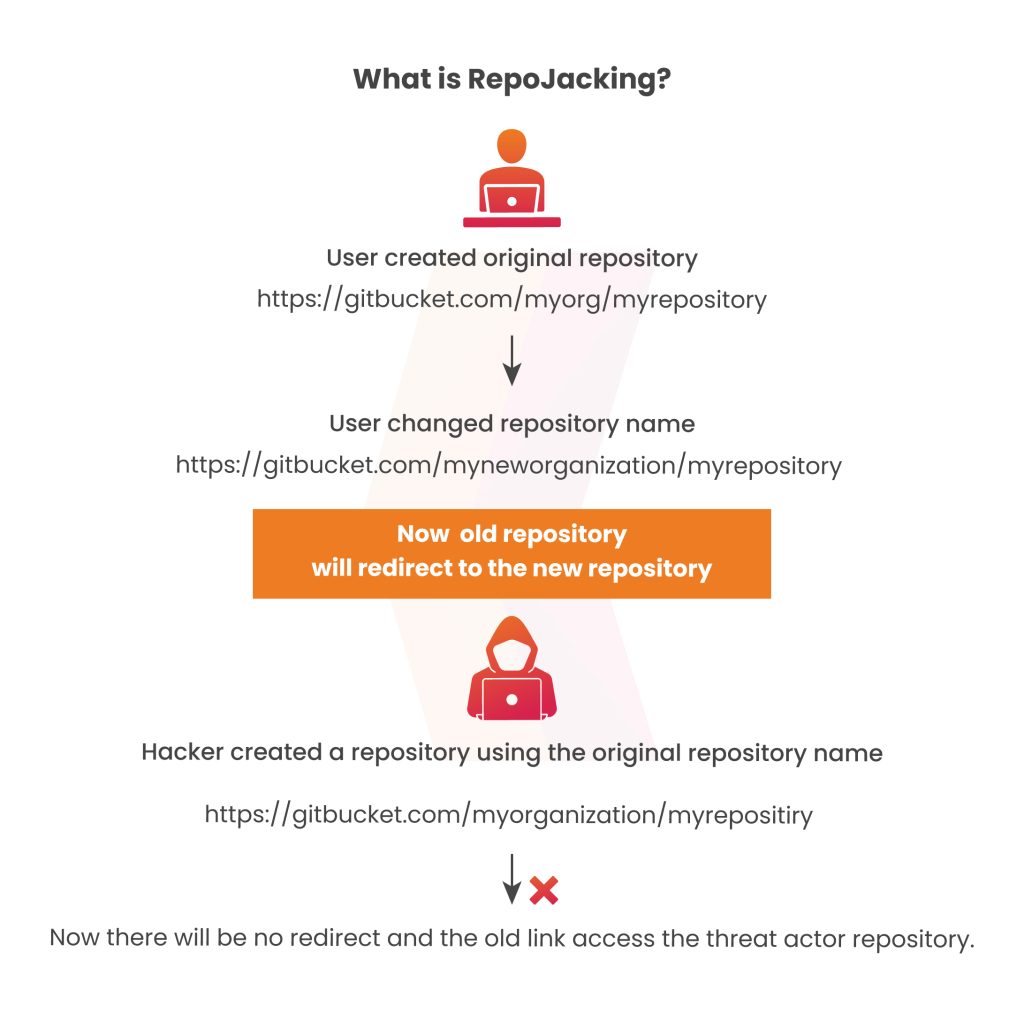
How Does RepoJacking Work?
A repository attack, also known as a supply chain attack, typically exploits vulnerabilities in hosting platforms like GitHub. There are two common methods used in RepoJacking:
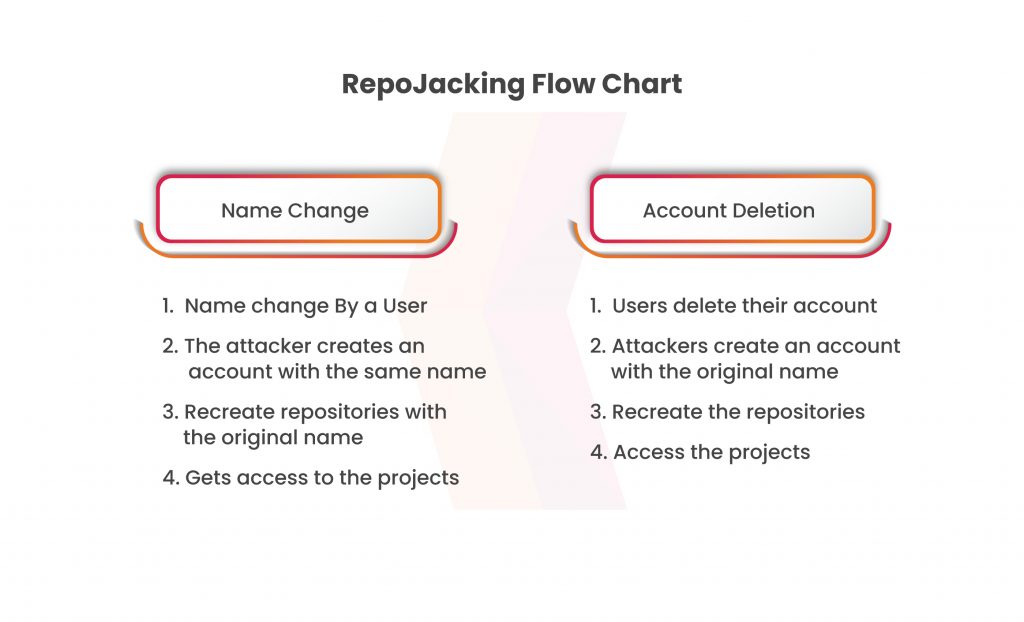
- Name change: When a user changes their username on a hosting platform, an attacker can potentially register the repository with the original username. This allows them to recreate the repository, and packages depending on the project may still access the original repository URL for updates.
- Account deletion: Similar to the aforementioned method, a malicious actor can re-register a deleted account and re-create the original repository. This method can cause errors for projects trying to fetch the repository through a URL, as the link would be broken. However, attackers can bypass this issue by registering the deleted username between the time of deletion and the refresh of projects attempting to fetch the repository.
Once the attacker gains control of the repository, they can carry out various privileged actions. This includes appointing other malicious users or self-created accounts as administrators or maintainers, enabling them to approve unauthorized code changes. They can force the inclusion of malicious or unwanted code in new project versions or even delete functional code from the repository, leading to the sabotage or corruption of existing functionality.
What are the Security Impacts of Repojacking?
The security impact of successful repository hijacking attacks can be severe, especially for users of affected packages that act as dependencies. These attacks allow the upload of unrestricted malicious code through existing or newly released versions, which can directly affect external projects by automatically or manually upgrading to the latest versions.
Repojacking attacks often go unnoticed for extended periods, sometimes lasting for days or weeks. They are typically disclosed by vigilant researchers, observant users, or the original owners who realize their repository has been hijacked. The responsibility of addressing the problem generally lies with the hosting platform, which can take actions to mitigate the impact of malicious package versions by removing or suspending compromised accounts.
While these attacks may seem straightforward to exploit, they depend on specific conditions, which are not commonly found in the accounts of popular project owners, particularly those that receive frequent updates. Attackers often target active account owners using phishing or more sophisticated “whaling” techniques to gain access to their accounts or manipulate them into carrying out actions through cross-site scripting attacks. However, many browsers and sites have built-in protections against such attacks.
Get in!
Join our weekly newsletter and stay updated
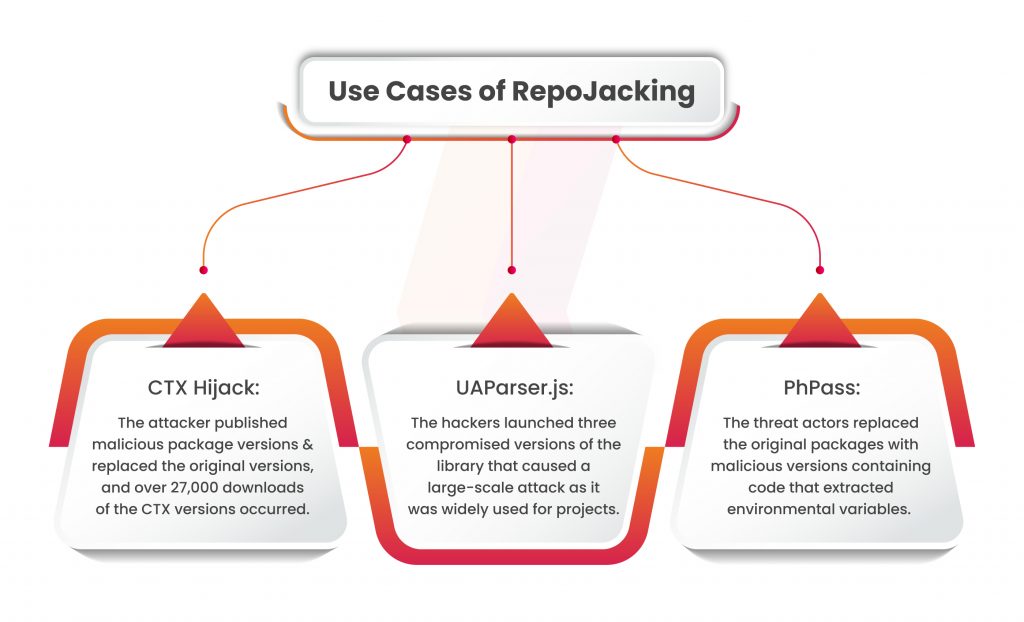
There have been real-world examples of RepoJacking incidents:
- CTX Hijack: In May 2022, the Python package CTX experienced repository hijacking on PyPI. The original domain-hosting email for the owner account expired, allowing a third party to reset the password and re-register the domain. The attacker quickly uploaded malicious packages, replacing the original versions. The hijacking remained undetected for 10 days, during which over 27,000 downloads of the malicious CTX versions occurred. The added code in the package exfiltrated sensitive user information to an external endpoint. PyPI administrators suspended the hijacked account and removed all versions of CTX.
- PhPass: The PHP package PhPass was exploited in a similar manner in May 2022. The owner’s account was deleted and registered again with the same name, accessing to the original repository. The attacker replaced the original package versions with malicious versions containing code that extracted environmental variables. As a solution, a forked repository was created to host the non-malicious versions, and the original download URL was redirected to the new fork.
- UAParser.js: In October 2021, the popular JavaScript library UAParser.js was weaponized when the author’s NPM account was taken over. The attacker published three malicious versions of the library, leading to a large-scale attack as it was widely used across projects. The malicious code in these versions downloaded and executed binaries from a remote server, including cryptocurrency mining software and a trojan that exfiltrated sensitive information from Windows systems. The compromised versions were quickly removed, and new versions were released to mitigate automatic upgrades to the malicious versions.
Conclusion
Several measures can be implemented to protect organizations from RepoJacking and other supply chain attacks. One crucial approach is the use of multifactor authentication, particularly two-factor authentication (2FA). GitHub has announced that 2FA will be mandatory for all maintainer accounts starting in 2023, significantly increasing its adoption. However, some platforms like NPM have yet to enforce 2FA despite the risks. Domain takeovers can also be prevented by proactively suspending or removing accounts with expired or expiring domains. However, this approach requires increased maintenance and monitoring by hosting platforms.
As open-source projects continue to grow and become more dependent on dependencies, repojacking incidents are likely to increase. To address this, greater adoption of preventative technologies such as 2FA is necessary. Mandatory enforcement of security measures like 2FA could help mitigate the impact of repository hijacking by ensuring a higher level of account security for repository owners.
Kratikal, a CERT-In empanelled organization, has helped organizations to mitigate Repojacking vulnerabilities. Kratikal can also help organizations secure their code vulnerabilities by secure code review which helps organizations to mitigate supply chain risk.








Leave a comment
Your email address will not be published. Required fields are marked *