The goal of VAPT Testing is to improve digital security in an organization. Cyber attacks and vulnerabilities are increasing rapidly. Here’s where Vulnerability Assessment and Penetration Testing come into play. The usage of a proactive methodology to find cybersecurity infrastructure flaws in business networks. In this blog, we will discuss what VAPT is and how it may prevent corporations from data breaches.
Table of Contents
What is VAPT Testing?
Vulnerability assessment examines digital assets for flaws to identify the issues in an organization’s inventory. Vulnerability Assessment and Penetration Testing help detect application-level vulnerabilities, network and system vulnerabilities, API and data vulnerabilities, and many others. It helps businesses by taking advantage of flaws in your organization’s assets. You can improve your entire cybersecurity posture by prioritizing and installing effective security measures with the help of this proactive testing strategy. Additionally, it will help you understand in detail the extent of the security flaws in your organization.
Why is VAPT Testing Essential for Organizations?
VAPT services are essential for finding vulnerabilities inside the IT infrastructure of the organization. Malicious actors might take advantage of the vulnerabilities to gain unauthorized entry to the software programs, applications, and network of the enterprise, making it vulnerable to protection breaches and different security issues. Any organization in a regulated industry that manages sensitive data or uses connected systems needs to conduct VAPT testing. If you don’t, you become vulnerable to cyberattacks because you will be unaware of the loopholes in your IT infrastructure, which might give way to potential risks in the future. You must evaluate and identify the risks in the networks, which include data breaches, malware, and much more.
Book Your Free Cybersecurity Consultation Today!
Difference Between Vulnerability Assessment and Penetration Testing
| Vulnerability Assessment | Penetration Testing |
| This method comprises identifying and evaluating weak points within an organization’s network. | It generates a listing of vulnerabilities primarily based on their severity. |
| It entails discovering and exploiting flaws to bypass safety features. | This testing also helps identify potential entry points for hackers to get unauthorized access to the company’s virtual assets. |
| The assessment is performed internally, examining networks and applications within the organization. | These tests are conducted remotely, targeting external networks and applications to pinpoint vulnerabilities and potential threats. |
| The assessment aims to identify established vulnerabilities that could harm a system and expose essential business assets to a data breach. | The conducted test aims to uncover unidentified threats and vulnerabilities within a system which helps in assessing the level of risk to which the systems are exposed. |
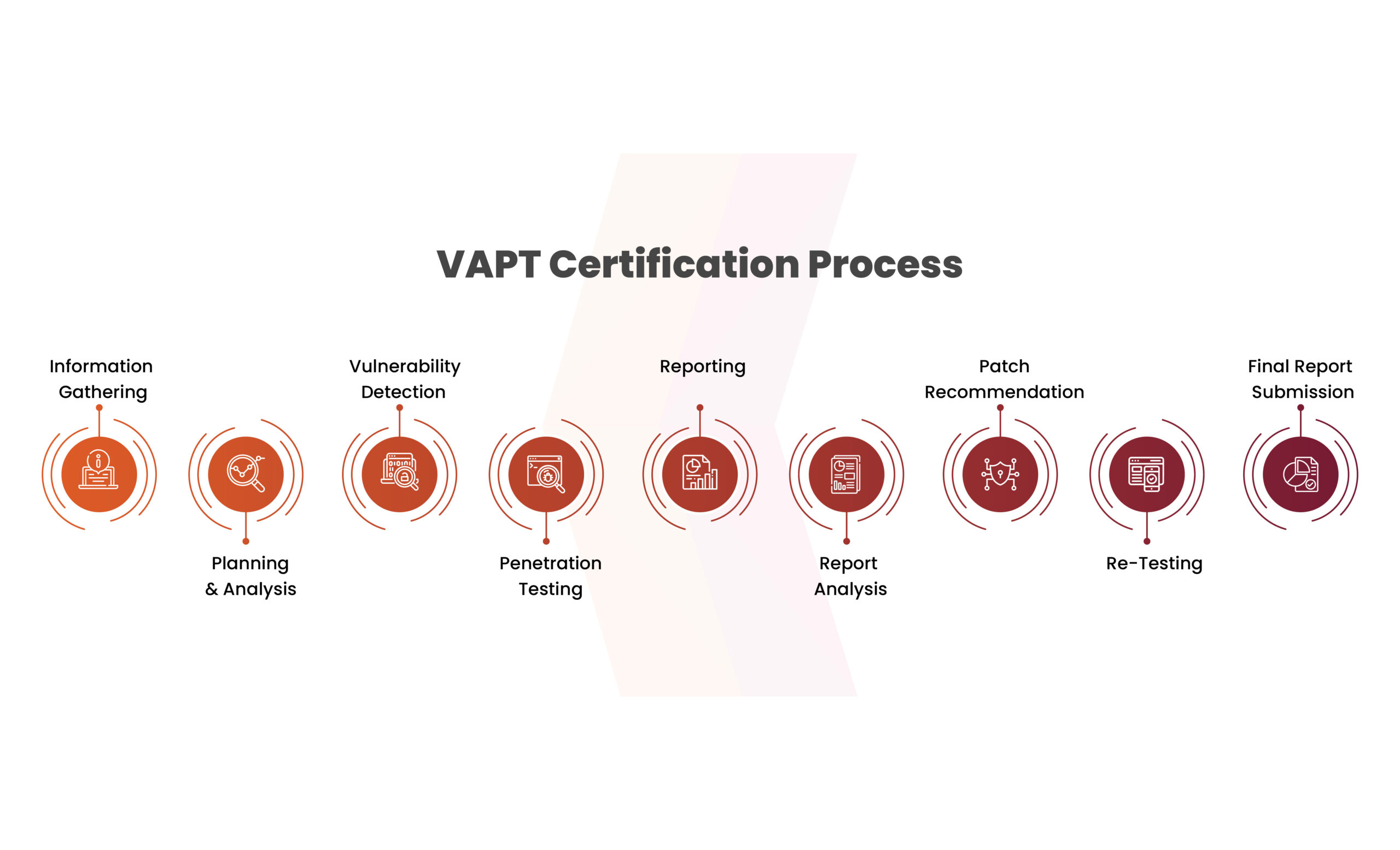
Process of VAPT Certification
The VAPT certification process involves the following steps: Information Gathering, Planning and Analysis, Vulnerability Detection, Penetration Testing, Reporting, Patch Recommendations, Re-Testing and Final Report.
How can Kratikal VAPT Testing Services Prevent Data Breaches?
Data breaches pose enormous challenges, affecting not only targeted companies and organizations but also individuals who face risks such as identity theft, financial loss, and reduced trust. Data stands as the weakest asset in any organization. Conducting VAPT testing stands out as one of the most effective ways to protect an organization’s network and data from cyber-attacks.
Benefits of VAPT Testing
VAPT benefits organizations like yours in the following ways:
- Secures confidential data and information, preventing unauthorized access, theft, or breaches.
- Adheres to a systematic approach for identifying crucial vulnerabilities and enhancing risk management practices.
- It offers a thorough examination and assessment of web/mobile applications, network, cloud, IoT, OT, and other assets in your IT infrastructure.
- Identifies the gaps and flaws in the infrastructure that may result in cyberattacks.
- Helps shield businesses from financial and reputational damage.
- Aids in attaining and upholding compliance with national codes and regulations.
Get in!
Join our weekly newsletter and stay updated
Conclusion
VAPT Testing is essential for mitigating cyber threats and vulnerabilities and for improving cyber safety. Through the proactive identity and evaluation of risks in a company’s cybersecurity structure, VAPT offerings help companies recognize vulnerabilities. Combining penetration testing with vulnerability assessment provides a proactive way to strengthen safety features. Kratikal, a CERT-In empanelled auditor, provides comprehensive cybersecurity solutions aimed at protecting businesses from a wide range of cyber threats. With a special focus on securing your IT environment, Kratikal helps businesses identify potential risks and effectively mitigate them. By partnering with us, companies are proactively able to address security vulnerabilities, thwarting the efforts of malicious hackers to exploit these vulnerabilities.on’s network and data from cyber-attacks.
FAQs
- What do you mean by VAPT report in cybersecurity?
The VAPT report outlines the vulnerabilities in an organization’s IT infrastructure or applications during the testing procedure. It describes potential vulnerabilities, their severity, and solutions to correct identified vulnerabilities. This report is essential for organizations to protect themselves from cyber risks.
- What is the use of VAPT Testing?
Such testing is done to ensure and enhance the security of a business’s digital assets. Vulnerability Assessment and Penetration Testing identify vulnerabilities in a business’s digital environment, applications, and networks. This testing is used to assess how to combat cyber threats and protect against cyberattacks.









Leave a comment
Your email address will not be published. Required fields are marked *