
Before understanding the need for endpoint security, let’s make you see through a recent study on the same. Around 68% of businesses experienced a targeted endpoint attack that compromised their IT infrastructure. Devices also experienced the same percentage rise in cyber attacks compared to previous years.
Table of Content
What is Endpoint Security?
Endpoint security can be defined as protecting the endpoints of end-user devices. These gadgets can be desktops, laptops, and mobile phones, which can be misused for malicious activities. These could instantly lead to a cyberattack. Initial compromises or threats frequently target these endpoints on a network or in the cloud.
What is Considered an Endpoint?
An endpoint refers to any hardware capable of connecting to the network infrastructure, including servers, laptops, computers, smartphones, and even IoT devices. With the increasing number of endpoints, particularly in the context of remote work and the Internet of Things, the surface area available to potential cyber threats grows. This makes network or IT infrastructure security an increasingly complex yet vital issue.
This is How Endpoint Security Works
Endpoint security ensures that any device complies with the organization’s security standards before it connects to the network infrastructure. It uses a variety of methods, such as email filtering, firewalls, antivirus software, and more. Some advanced tools like Mobile Threat Defense (MTD) and Endpoint Detection and Response (EDR), can also be useful. Before threats can compromise data or infiltrate a network, these technologies assist in identifying, blocking, and mitigating them.
Components of Endpoint Security
Antivirus and Anti-Malware Software: The fundamental elements that protect against viruses and malware.
Endpoint Detection and Response or EDR: The EDR includes tools for advanced threat detection, investigation, and response.
Application Control: This stops unauthorized apps from being installed in the first place.
NAC (Network Access Control): It checks that devices follow security policies before granting them access to the network.
Data Loss Prevention (DLP): It helps monitor and control data transfer to prevent data breaches.
Book a Free Consultation with our Cyber Security Experts

Endpoint Protection v/s Antivirus
Antivirus software is necessary for identifying and eliminating malware. Yet, we still need more comprehensive solutions to secure your devices in the modern digital defense. Endpoint Protection Platforms (EPP) provide all-around defense against a wider variety of threats. These can include phishing, malware, and zero-day vulnerabilities. A multi-layered defense mechanism that is far superior to standalone antivirus software is provided by EPP Solutions. This integrates several security technologies like firewalls, antivirus, and data encryption.
Importance of Endpoint Security for IT Infrastructure
One cannot emphasize how important endpoint security is for protecting the IT infrastructure in 2024. Securing endpoints ensures the availability, integrity, and confidentiality of vital data, considering the growing sophistication of cyber threats. Additionally, it is essential to adhere to data protection laws and safeguard against data breaches that might cause serious harm to one’s finances and brand reputation. Moreover, endpoint security is fundamental to establishing resilient network or IT infrastructure security to ensure that networks are protected and can adapt to evolving threats.
Benefits of Endpoint Protection to Secure IT Infrastructure
Endpoint security is essential for protecting IT infrastructure from the wide range of cyber threats that businesses encounter today.
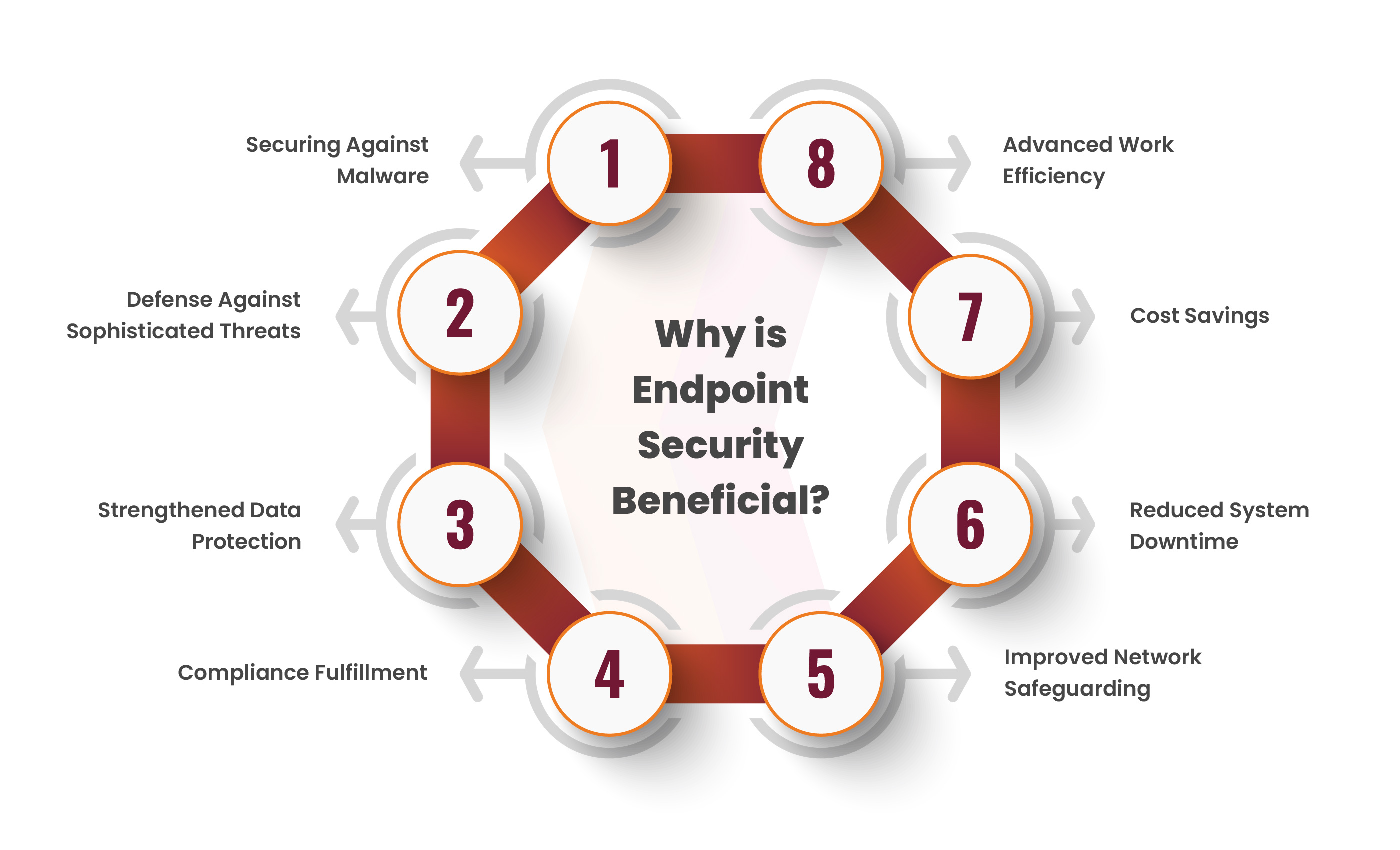
The following are the main advantages of having a strong endpoint security strategy in place:
Protection Against Malware: Endpoint security solutions effectively block various forms of malware, including viruses and spyware. This can help prevent devices from being compromised.
Protection Against Advanced Threats: Technologies such as Endpoint Detection and Response (EDR) and Advanced Endpoint Protection (EPP) provide defense against advanced threats like ransomware and zero-day attacks.
Enhanced Data Security: By securing endpoints, businesses can prevent breaches and unwanted access to sensitive data. This ensures data integrity and confidentiality.
Adherence to Compliances: Endpoint security keeps businesses out of troubles like legal issues and heavy penalties. This is done by guiding them to follow strict data protection laws.
Enhanced Network Security: Protecting endpoints reduces the possibility that hackers will breach the network. This enhances the security of the network and overall IT infrastructure.
Decreased Downtime: Effective endpoint security lowers the possibility of cyberattacks that might disrupt business operations.
Cost Savings: Organizations can reduce the high expenses of data breaches, such as remediation expenses, reputation harm, etc., by preventing breaches and attacks.
Increased Productivity: Protecting endpoints from attacks and malware helps maintain optimal device performance, contributing to increased employee productivity.
An early move towards implementing endpoint security for secured IT infrastructure creates a huge impact for a more reliable, secure, and effective solution.
Kratikal’s Enhanced Endpoint Security Solutions
Kratikal, a CERT-In empaneled auditor, has improved endpoint security solutions and has tailored them as per the changing IT infrastructure. In 2024, it is necessary to respond to the escalating endpoint security threats. Kratikal’s endpoint network security services, along with compliance services, offer comprehensive protection for your digital data. This includes not only, vulnerability management and, threat intelligence but also ensures that organizations can maintain a robust defense against cyber threats.
The secret to a strong digital defense is realizing how critical endpoint security is and putting in place all the right solutions that can change with the swiftly changing tactics of hackers to attempt a cyber attack.

