A network vulnerability scan checks and evaluates security vulnerabilities in a computer network. It uses special software to look at systems, devices, and apps in a network to find possible vulnerabilities. These might include outdated software wrong setups, or security gaps. Network vulnerability scanning aims to spot and rank security risks, so organizations can fix these problems before hackers can take advantage of them. This scanning is a key part of staying ahead in cybersecurity. It helps protect sensitive data and keeps an organization’s overall security strong. In this blog, we’ll take a deep dive into what a network security scan is all about.
Table of Contents
Importance of Network Vulnerability Scanning?
Network vulnerability scanning is key to keeping cybersecurity strong in any organization. By checking for weak spots in IT systems, these scans help organizations find security holes before bad guys can use them. This helps teams focus on fixing the biggest threats first and stops data leaks and unwanted access. Also, doing these scans often keeps companies following industry rules and standards, which protects important info and keeps business running. By dealing with weak spots, companies can boost their overall security keeping their work safe and reliable.
What is a Network Vulnerability Scanner?
Vulnerability scanners play a key role in spotting and reporting known flaws in a company’s IT setup. Using a vulnerability scanner is a simple but crucial security step that helps every organization. These scans offer useful insights into possible security gaps helping companies grasp the security risks they might face. Scanners can identify thousands of vulnerabilities, often prioritizing remediation based on the CVSS (Common Vulnerability Scoring System) rating. However, these scores don’t always consider an organization’s unique setup.
A vulnerability might have a moderate risk score, but if it can be exploited as a pivot point to access other vulnerabilities or resources, it could pose significant risks to the organization.
To get full coverage many companies use several vulnerability scanners making sure they check every asset. Over the years, lots of scanners have come out giving companies many options and features to pick from. This lets them shape their approach to fit their specific needs.
Book Your Free Cybersecurity Consultation Today!
Types of Network Vulnerability Scans
Network vulnerability scans can be classified into 2 categories:
Non Intrusive Vulnerability Scans
This method finds vulnerabilities and creates a report for users to fix them. The scanning tool spots these problems without taking advantage of them or messing up daily work. It has an impact on how we deal with security issues allowing teams to tackle vulnerabilities head-on.
Intrusive Vulnerability Scans
Intrusive assessments go beyond just spotting weak points. They involve coming up with an attack plan and exploiting the vulnerabilities in a mock attack to show their possible effects and outcomes. This approach tests how well a company’s defenses can stand up to different threats.
Benefits of Network Vulnerability Scanning
Network vulnerability scanning has a big impact on business security. It helps spot potential risks before they turn into breaches, which cuts down on the chances of unauthorized access and data theft. This approach gives a full picture of network security letting companies make smart choices about cybersecurity. It also helps businesses follow the rules, which is key to keeping customers’ trust and staying out of legal trouble. Keeping an eye on things through regular scans means companies can react to new threats. Continuous monitoring of risks is cost-effective and prevents expensive data breaches. Checking the security of partners and suppliers helps protect the whole supply chain from weak spots.
Process of Network Vulnerability Scanning
Network vulnerability scanning is a methodical process designed to spot and rank weaknesses in a network’s structure. This in-depth approach includes several key steps making sure all parts of the network are checked for possible security threats. Here’s a breakdown of the step-by-step process:
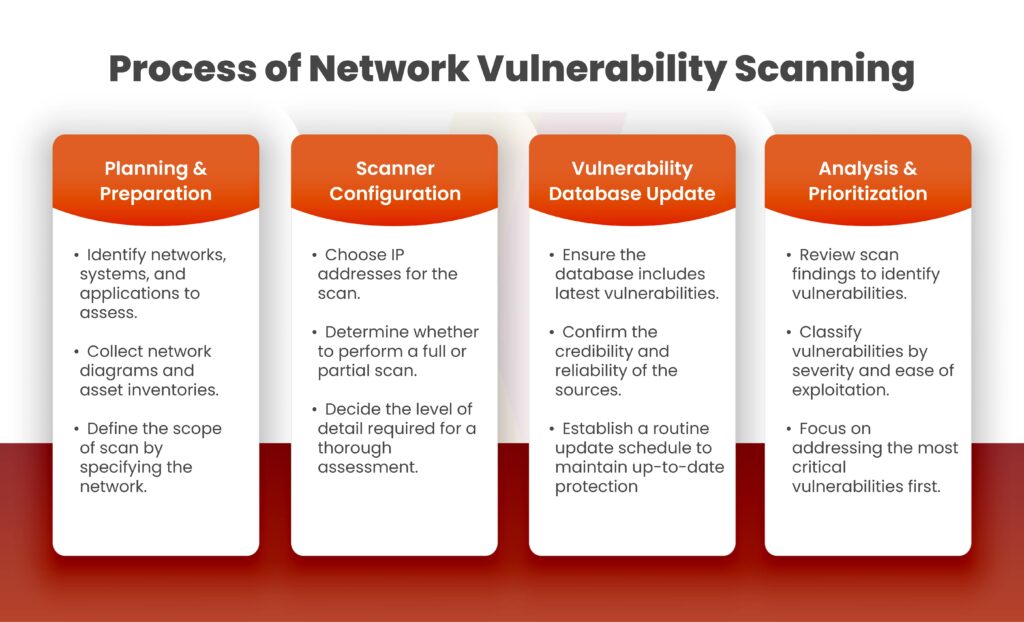
Planning and Preparation
Before kicking off the scan, IT staff need to set the boundaries of the assessment. They do this by figuring out which networks, systems, and apps they’ll look at. This step involves collecting network docs and making a detailed list of assets.
Scanner Configuration
The next step involves setting up the vulnerability scanner with the right options. This means picking the target IP addresses deciding on the scan type (full or partial), and figuring out how deep to scan to make sure everything’s covered.
Vulnerability Database Update
Before starting the scan, the scanner updates its database of known vulnerabilities to include the newest threat information. This allows the scan to find both recent security weaknesses and existing flaws.
Analysis and Prioritization
Once the scan wraps up, experts analyze the results. They spot and sort vulnerabilities based on how serious they are, looking at things like possible damage and how easy they are to exploit. This key step helps paint a picture of where the weak spots are and lets teams focus on fixing the most important problems first.
Key Considerations When Choosing Vulnerability Scanning Tools
When selecting a vulnerability scanning tool for your enterprise, prioritize the following capabilities:
- Frequency of Updates: The scanner’s database needs constant updates to include new vulnerabilities.
- Quality and Quantity of Vulnerabilities: The tool should be able to spot all weak points while cutting down on wrong alerts, both false alarms and missed issues. It should give in-depth details about flaws how risky they are, and how to fix them.
- Actionable Results: It should generate comprehensive reports that enable practical, corrective actions.
- Integrations: The scanner should seamlessly integrate with your broader vulnerability management program, including patch management and other solutions.
Proper implementation of a vulnerability scanning tool is crucial for identifying and assessing security risks, enabling regulatory compliance, and maintaining a robust cybersecurity posture.
Why do Organizations Need Network Vulnerability Scanning?
Network security plays a key role in helping businesses protect important data, keep client information safe, boost network productivity, and stop ransomware attacks. When companies safeguard business and personal data, they can steer clear of big losses and possible business failures. Network security also makes sure businesses follow privacy laws and rules in fields like finance. What’s more, it helps prevent identity theft by protecting the company’s brand identity from cyber criminals. In the end, a strong network security system is crucial to keep data intact and to make sure operations run smoothly.
Get in!
Join our weekly newsletter and stay updated
How can Kratikal Help you with Network Vulnerability Scan?
Kratikal provides network vulnerability scanning services to spot and tackle weak points in your setup. Our group carries out in-depth checks, gives detailed reports, and offers useful tips making sure your company is safe from the newest threats. With solutions, you can tailor and that fit into your current security system, we help you keep a strong cyber defense and stop possible break-ins. Count on Kratikal for thorough vulnerability handling and steps to stay ahead of problems.
FAQs
- What are Network Vulnerabilities?
A weak spot or bug in software, hardware, or how an organization operates is called a network vulnerability. Threat actors can take advantage of these flaws, which can lead to a security breach. Most of the time when we talk about non-physical network vulnerabilities, we’re referring to issues with software or data.
- How does the network vulnerability scanner work?
Vulnerability scanning works by using special software tools to check and examine computer systems, networks, and applications. These tools find known security weak spots wrong settings, and old software versions.








Leave a comment
Your email address will not be published. Required fields are marked *