Two government organizations in two different Middle East countries were attacked by the Chinese hacker group known as ‘Emissary Panda’. Allegedly, the hacker group has exploited a recently patched vulnerability in Microsoft SharePoint tracked by CVE-2019-0604. The remote code execution vulnerability is exploited to compromise servers and install a webshell.
The hacker group uses number of methods to access target’s system that includes hacking the webmail server or phishing emails that include malicious emails or attachments within them.
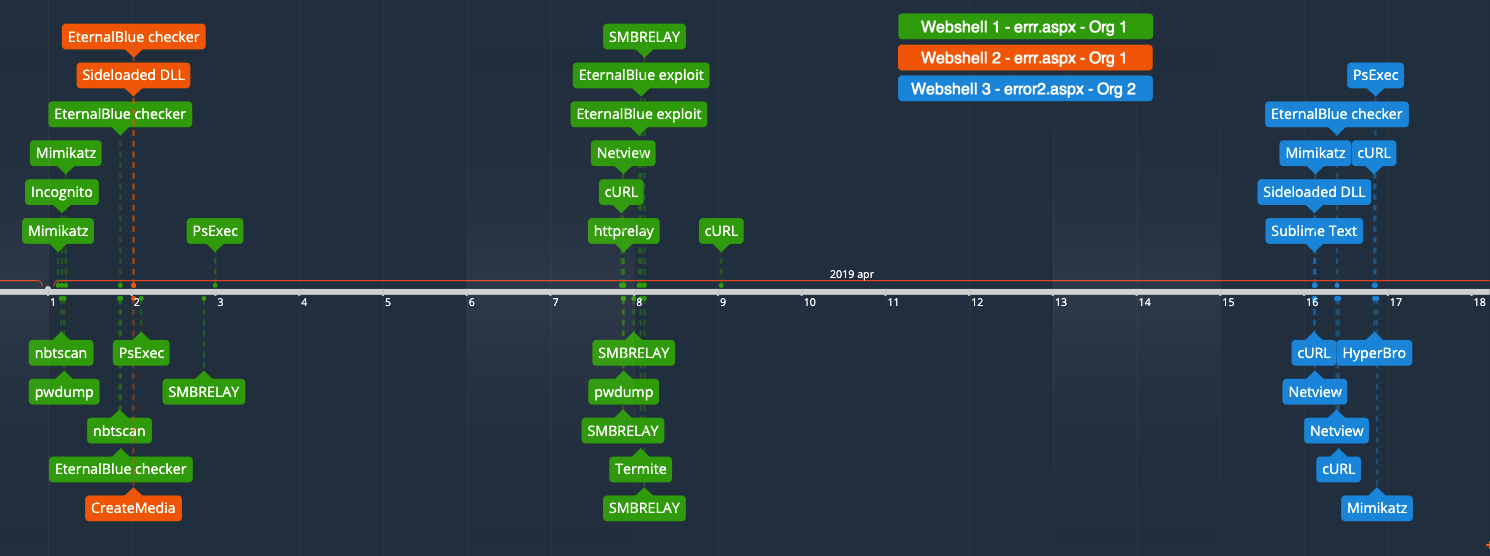
Timeline of file uploads across three related webshells
The webshell activity occurred across three different SharePoint servers where the actors uploaded 24 different executables from April 1st to April 16th, 2019. Sharepoint is a web based collaborative program that incorporates with Microsoft Office. The affected software versions are Microsoft SharePoint Foundation 2010 Service Pack 2, Microsoft SharePoint Foundation 2013 Service Pack 1, Microsoft SharePoint Server 2010 Service Pack 2, Microsoft SharePoint Server 2013 Service Pack 1, Microsoft SharePoint Enterprise Server 2016 as well as Microsoft SharePoint Server 2019.
The actors used these webshells to upload legitimate executables that could be used for DLL sideloading for running a malicious DLL which has a code that overlaps with known Emissary Panda attacks. China Chopper webshell was also found on the SharePoint servers, which can also be used by the Emissary Panda threat group.
The group has been active since 2010 and has targeted organizations worldwide including financial service firms, national data centre in Central Asia as well as U.S. defence contractors. Once the network is compromised, attackers will upload a variety of tools for performing activities like dumping credentials, locating additional systems on the network.
Attackers used tools to scan the network for systems vulnerable to CVE 2017-0144 that can be exploited by NSA-linked EternalBlue exploit. The vulnerability was first discovered by Markus Wulftange who further reported it to Microsoft.
How can organization combat such attacks?
Running software as an unprivileged user: Try running non-administrative software as a non-privileged user with minimal rights.
Monitor network traffic: Deploy Network Intrusion detection system to monitor the network traffic for malicious activities.
Patch Application: Apply and update operating system patches from Microsoft.
Periodic Penetration Testing: Organizations should ensure periodic vulnerability assessment and penetration testing services (VAPT) that will help in finding vulnerabilities that can be patched before being exploited by the attackers.
According to the statistics, the cyber security market is expected to cross $300 billion by the year 2024. Small businesses are spending more than $500 per year on cyber security products. This assures us that with an increase in the rate of cyber-crimes, cyber security is becoming a prior concern for organizations. Cyber security companies like Kratikal are becoming a part of this process to safeguard organizations with its state-of-the-art cyber products and services.
Cyber-attacks are becoming sophisticated in nature and this makes threat detection difficult for attackers. Organizations are gradually gaining awareness about the impacts of such attacks. It is, therefore, extremely important to invest in cyber security.

