Microsoft has admitted that a vulnerability has been discovered in its Azure Active Directory (AD) Open Authorization (OAuth) process which facilitates hackers a complete account takeover. Researchers from Descope, a California-based identity and access management service, have reported the vulnerability and named it ‘NoAuth.’ During April 2023, Descope’s Chief Security Officer, Omer Cohen, described NoAuth as ‘an authentication implementation flaw that primarily affects multi-tenant OAuth applications within Microsoft Azure AD.’
The misconfiguration related to the modification of email attributes under the “Contact Information” section in Azure AD accounts. Exploiting the “Log in with Microsoft” feature, malicious actors could compromise victim accounts. To leverage the “Log in with Microsoft” option for authorization on the vulnerable app or website, an attacker merely needed to modify their Azure AD admin account’s email address to the victim’s address associated with the Azure AD admin account to the victim’s email address.
Table of Contents
Terms you should know to understand NoAuth Better
To understand the NoAuth misconfiguration, let’s briefly go through the terms related to it.
OpenID Connect (OIDC)
An open authentication protocol called OpenID Connect (OIDC) builds on the OAuth 2.0 architecture. OpenID Connect (OIDC) is a consumer-focused standard that enables users to access third-party websites with just one sign-on (SSO) by using OpenID Providers (OPs) such as email services or social networks to verify their identities.
Azure Active Directory (Azure AD)
Azure AD is a widely used cloud-based identity and access management service.
The Azure portal, Microsoft 365, and dozens of other software-as-a-service (SaaS) applications employ OAuth apps. These are just a few examples of the external resources that Azure AD controls user access to. Azure AD integrates with numerous OAuth-enabled SaaS applications, providing users with a seamless and secure experience across different platforms. Its secure features enable organizations to efficiently manage user access, enhance security, and streamline the authentication process.
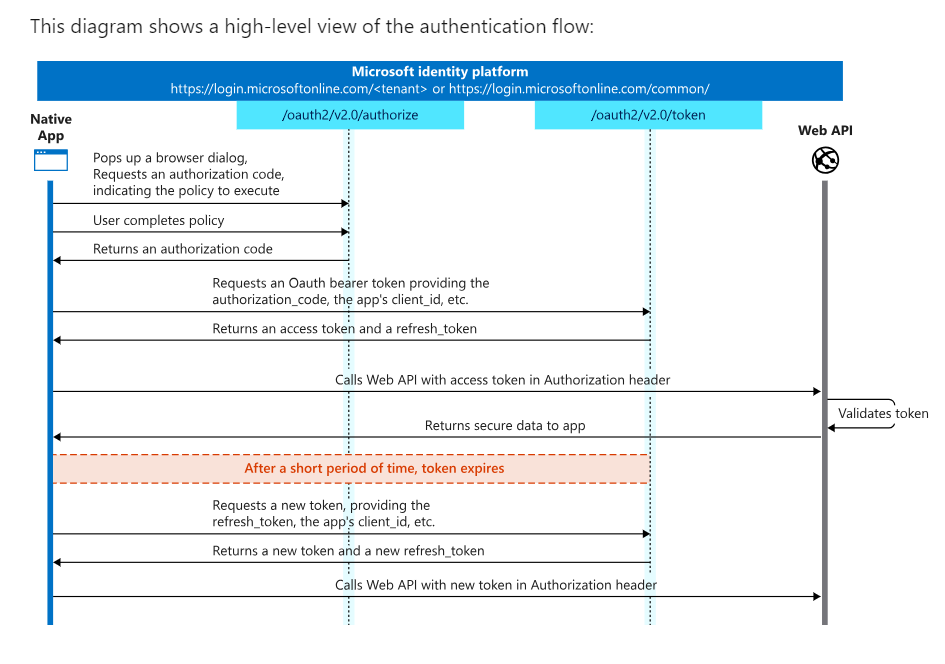
A combination of OAuth and OIDC allows users to sign in to websites using their Microsoft account.
Identity Provider (IdP)
An external source of truth for user IDs is an Identity Provider (IdP). Several well-known identity providers are Azure AD, Okta, Google, and Twitter. The authentication is based on previously established trust with the IdP for the “Open” notion in OAuth and OIDC to function. The entire system collapses if the IdP cannot be trusted with the identity data they give or if an application bases a user’s identity on an assertion that the IdP claims are subject to change.
Open Authorization (OAuth)
An open, token-based authorization mechanism called Open Authorization (OAuth) enables users to authorize access to private resources from one application to another application without disclosing any information about their identities. For instance, Facebook user doesn’t need to provide Medium with their login information to access their profile, read their posts, or post to their feed.
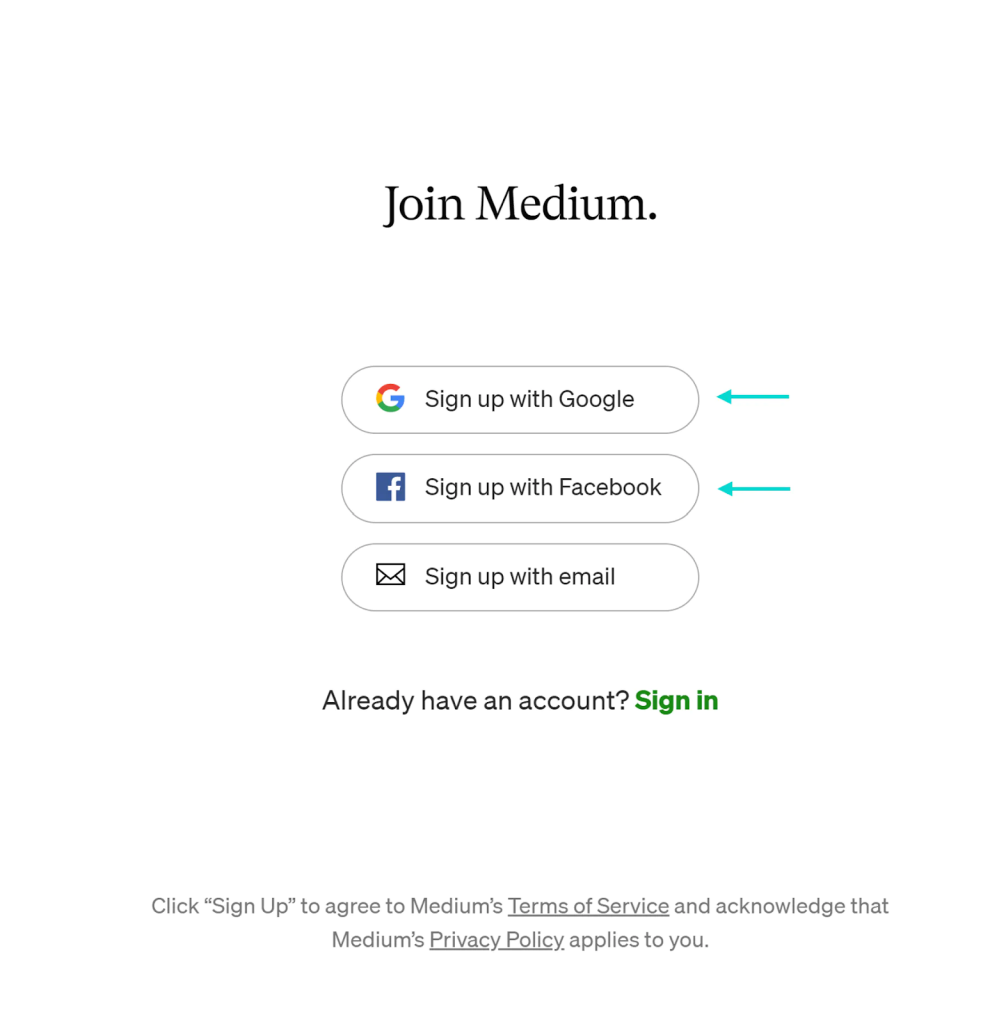
Email Magic Link
Magic links are links that are delivered to the customer only once throughout the authentication procedure. After providing their username, users are texted or given an email with a URL to their mobile device. Without typing a password, the user clicks to authenticate themselves, and since some people might perceive this as “magic,” the system is called “Magic Link.”
How NoAuth can affect Your Account?
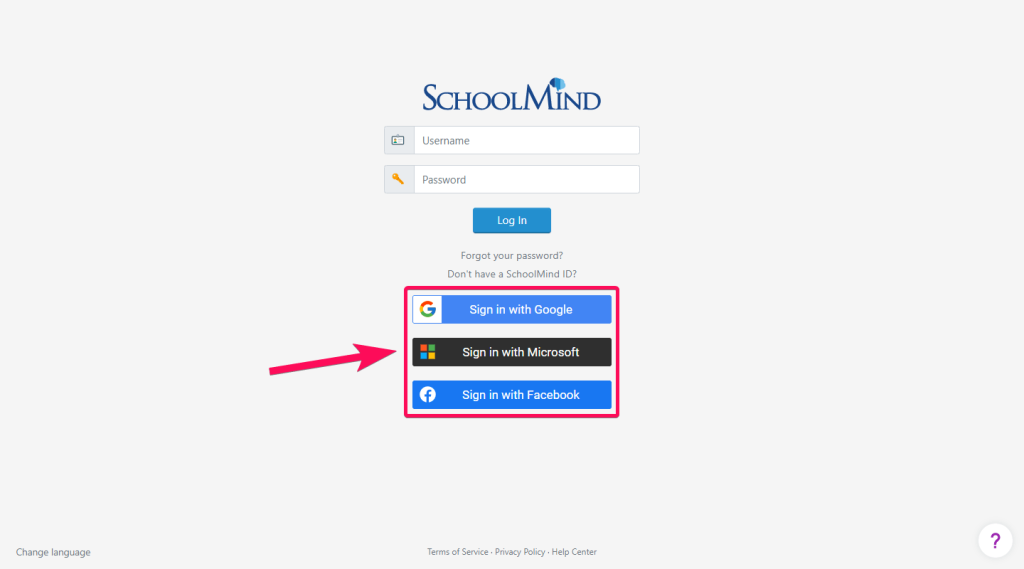
Consider a login screen for an app where the options for authentication include “Log in with Facebook,” “Log in with Microsoft,” and “Email Magic Link.” And a user registers via a magic link, makes use of the service for a bit, and then stops using it. There are chances that the user can forget the type of authentication they used to log in the last time they visited the app. They might unintentionally select “Log in with Microsoft” in this situation.
In simpler terms, when a user chooses to log in with their Microsoft account on an application, it’s common for the app to check if the user already has an existing account based on their email address. If they do, the app usually merges the accounts to keep everything organized for the user.
However, in the case of the NoAuth vulnerability, the problem is that the email address can’t be trusted or verified. This means that if the app blindly merges the user accounts based on the email address, it can lead to a situation where an attacker gains complete control over the victim’s account. It’s a serious security issue that needs to be addressed to prevent unauthorized access to user accounts.
To show this vulnerability, Descope took two emails:
Victim’s email address: omer@descope[.]com
Attacker’s email address: badguy@l33th4x0r.onmicrosoft.com
And during this proof of concept (PoC), two steps were discovered: preparation of the attack and the stage of the attack.
Stage of Preparation
- The attacker gains access to their Azure AD admin account.
- They change the “Email” attribute in Azure AD to the victim’s email address (Robin@gmail.com).
- Microsoft doesn’t require any validation for this email change.
Attacking Stage
- The attacker visits a vulnerable website or app that uses the email address as a unique identifier and offers a “Log in with Microsoft” option.
- If the app merges user accounts without proper validation, the attacker gains full control over the victim’s account, even if the victim doesn’t have a Microsoft account.
- Once logged in, the attacker can carry out various malicious activities like maintaining access, stealing data, exploring other parts of the app or website, and more.
Take a look at the screenshot below, which displays two separate logins using OAuth to access the same application. It’s important to notice that all the claim values are identical, except for the “email” claim.
In the demo provided below, you can see a to-do list application that offers three authentication options: “Sign in with Google,” “Sign in with Facebook” and “Sign in with Microsoft.” Unfortunately, by exploiting the NoAuth vulnerability, an attacker can utilize the “Sign in with Microsoft” option to gain control over a legitimate user’s account. They can then manipulate the user’s to-do list by adding malicious tasks.
Has Microsoft Patched the NoAuth Vulnerability?
After Descope reported the NoAuth configuration issue to Microsoft on April 11, 2023, they promptly opened a ticket the following day. On April 18, 2023, Microsoft responded, acknowledging the issue and committing to guide customers while working on a fix. Microsoft updated its documentation to address OAuth claims.
In May, Descope notified authentication providers about the flaw, and both providers acknowledged and confirmed the issue on May 4, 2023. Taking swift action, the authentication providers resolved the issue by May 6, 2023. Finally, on June 20, 2023, Microsoft released the necessary fixes, and in collaboration with Descope, conducted a joint public disclosure to ensure users were informed about the vulnerability and its resolution.
Guidelines Suggested by Microsoft for Securing Azure AD Applications
- Microsoft said that it is crucial for applications to avoid using the “email” claim for authorization purposes due to its susceptibility to change and lack of uniqueness. The tech giant acknowledges that addressing this vulnerability requires removing any business logic that relies on the email claim for authorization. Understanding that this process may take time, Microsoft recommends implementing short-term mitigations.
- Developers are advised to consult the provided documentation, which offers guidance on migrating away from email claim usage and outlines Microsoft’s mechanisms for mitigating risks. To ensure the security of applications, developers need to review their source code and ensure that this insecure authorization pattern is not being used.
Get in!
Join our weekly newsletter and stay updated
- Following published documentation on claims-based authorization best practices is crucial. If an application is currently affected, developers should refer to the guidance provided for short-term risk mitigation and transitioning away from email claims.
Bottom Line
OAuth vulnerabilities can lead to serious exploitation of user accounts and leverage several legitimate accesses. Microsoft advised developers to review their source code before making it live. Source code review is one of the best cyber security practices that organizations can mandate to avoid any loopholes or backdoors in the code.
Kratikal offers secure code review service along with many other services, for instance, web application testing, mobile application testing, cloud penetration testing, IoT, and Medical devices penetration testing at premium prices. We are a CERT-In empanelled organization with 11 years of legacy of serving clients with the best solutions.









Leave a comment
Your email address will not be published. Required fields are marked *