Authentication bypass vulnerability is a security defect that enables a threat actor to circumvent or bypass the authentication process of an application or system. On May 29, 2023, a team of cybersecurity experts discovered a vulnerability in Abandoned Cart Lite. This was for WooCommerce developed by Tyche Software. This detected bug was an authentication bypass vulnerability, CVE ID: CVE-2023-2986, found in the Ultimate Member plugin of WordPress. The Ultimate Member plugin is a free user profile plugin that allows users to create efficient resources and membership websites
This grants unauthorized access to sensitive data or functionalities. This security vulnerability can occur due to backdoors in authentication mechanisms, such as improper session management, and poor password strength. This even happens because of improper input validation. It holds a significant risk to the integrity and security of the system. This happens as it lets unauthorized individuals impersonate legitimate users and potentially perform malicious activities. Robust security measures and proper authentication protocols are vital in mitigating this vulnerability.
Table of Contents
Technical Analysis of the Vulnerability
According to its settings, Abandoned Cart Lite for WooCommerce shoots a notification to the email address of the prospects who have left their cart. They left the cart without making any purchases or simply abandoned their cart.
The notification message incorporates a link that logs in the user to complete the pending purchase. After reviewing the code, experts unveiled that the code contains an encrypted value to identify the abandoned cart.
Get in!
Join our weekly newsletter and stay updated
The notification link functions only when the encryption value is proper and valid, which needs an encryption key to be in place to create the values. But after examining the code, experts found out that the encryption key was hardcoded in the plugins, which directly indicates that the threat actors can also access the encryption key and create a valid value that can be injected in the link of the abandoned cart identifier of other customers because each cart identifier is a sequentially increasing in value starting from one.
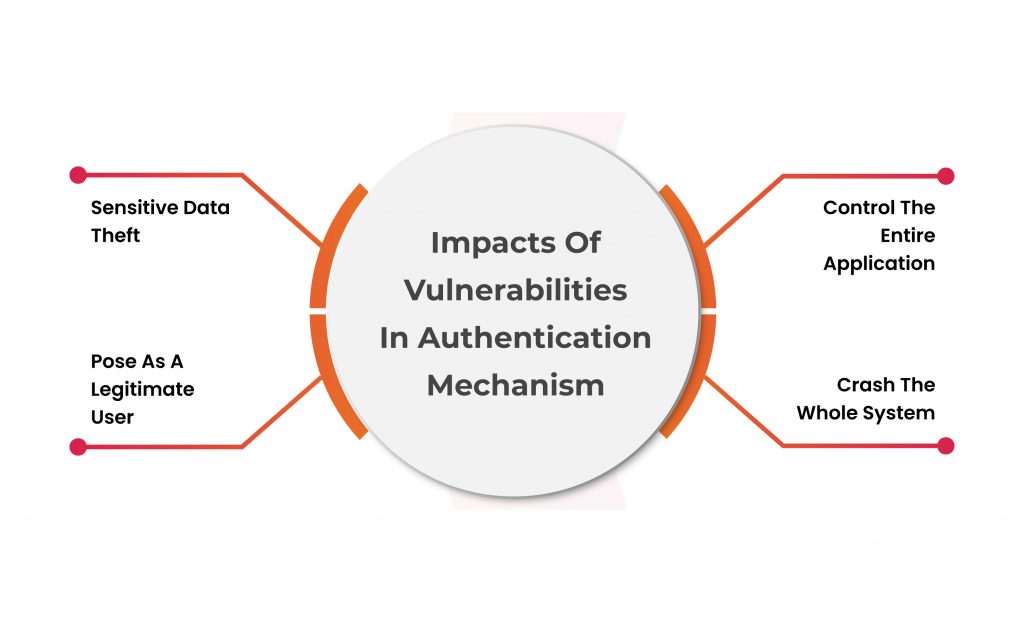
However, a threat actor is only restricted to accessing the abandoned cart accounts, meaning an attacker can only access the account of the users who have not completed the purchase and left the site in the middle, because, with the manipulated encryption value, they can only login as users with abandoned carts. Taking into account, a threat actor can access the user-level accounts but potentially can exploit this Authentication Bypass Vulnerability to access the administrative account or another higher-level user account.
How WordPress Plugins Are Prone to Authentication Bypass Vulnerability?
WordPress plugins can be prone to authentication bypass vulnerabilities due to a variety of reasons. A few of them are given below:
- Weak or Predictable Credentials: If a WordPress plugin uses weak or easily guessable credentials for authentication, attackers can exploit this weakness. Attackers attempt this to bypass the authentication process.
- Insecure Authentication Mechanisms: Some plugins may implement insecure or flawed authentication mechanisms, such as improper session management or weak encryption of user credentials. These vulnerabilities can be exploited to bypass the authentication mechanism.
- Lack of Input Validation: Insufficient input validation in WordPress plugins can lead to authentication bypass. Attackers may manipulate input fields or parameters to bypass authentication checks and gain unauthorized access.
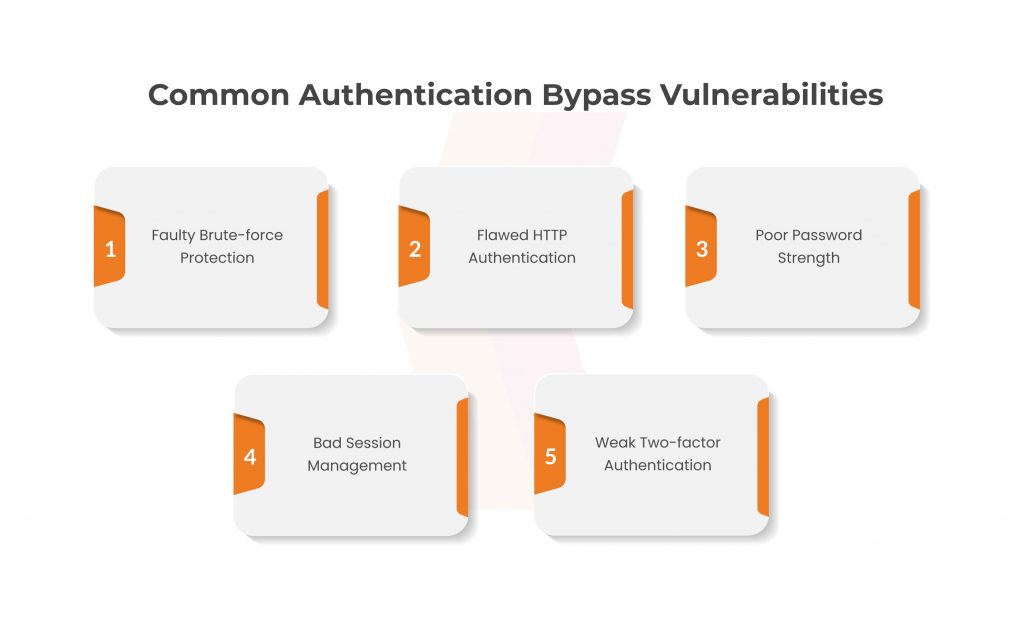
- Software Bugs or Design Flaws: Plugins with software bugs or design flaws can introduce vulnerabilities that allow authentication bypass. These flaws may arise from inadequate handling of user input, improper access control, or insecure storage of authentication-related data.
- Failure to Enforce Authentication Checks: In certain cases, plugins may fail to enforce authentication checks on critical functions or resources. This inadvertently allows unauthorized access without proper authentication.
- Outdated or Vulnerable Plugin Versions: If WordPress plugins are not regularly updated or maintained, they may contain known vulnerabilities. These can be exploited for authentication bypass. Attackers can leverage these vulnerabilities to bypass authentication mechanisms.
To mitigate authentication bypass vulnerabilities in WordPress plugins, it is crucial to follow best practices. Practices like using strong and unique credentials, keeping plugins up to date, and performing regular security audits play a vital role. This is done to employ secure coding practices to ensure robust authentication mechanisms.
Conclusion
It is to be noted that the developers developed the functionality backward, which was compatible with version 5.15.0. This means that old or previous abandoned carts can still be exploited even if the plugin is upgraded to the latest version. Additionally, security strengthening was launched in one version advance which is 5.15.1. This makes sure websites are foolproof through old abandoned cart notification links. Hence, it is necessary to ensure all sites are upgraded to the version.
Authentication Bypass Vulnerability can be detected by secure code review and Kratikal is working seamlessly to ensure no backdoors. Kratikal, a CERT-In empanelled organization, believes in rendering versatile cyber security solutions to businesses that face complexity in strengthening their information security posture.
As a firm, we have bagged several awards. We have incorporated a range of expert and qualified cybersecurity professionals that deliver best-class services and solutions. Our in-house pen-testing team has secured thousands of clients’ websites, applications, clouds, networks, etc. Our motto is to make digital resources secure for sure.








Leave a comment
Your email address will not be published. Required fields are marked *