PHP has a reputation for being flexible and reliable, and it’s used in tech and retail. It’s the backbone of about 80% of websites. Developers also like it because it’s easy to work with and can handle many different tasks. But even though PHP is popular and has its good points, it’s not perfect. Like all tech, it has weak spots that could put your apps and users at risk if you’re not careful. Recent studies show PHP has more security weaknesses making it an appealing target for hackers. Because these vulnerabilities are unique to PHP web apps, they’ve become a hot topic for CEOs and CTOs to discuss. This doesn’t mean these trends will hurt your tech stack’s resale value, but if you’re thinking about using PHP in a new web project, you should know about these ongoing talks.
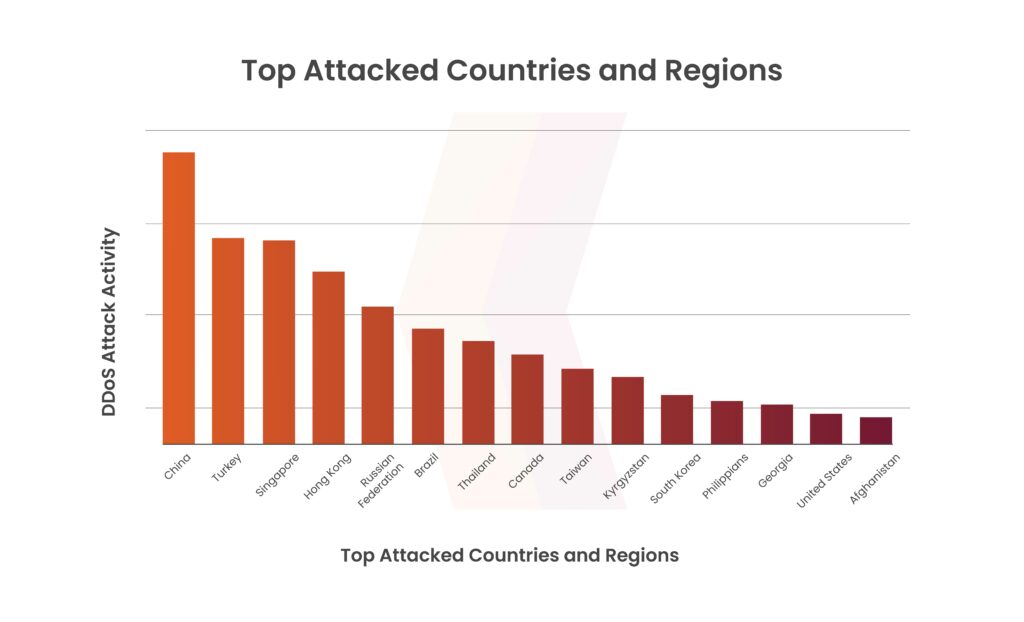
The disclosure of PHP vulnerability CVE-2024-4577 coincides with a 20% jump in DDoS attacks, as Cloudflare’s data shows when compared to the previous year. This spike has a significant impact on nations like China, Turkey, and Singapore as well as sectors such as technology and education.
Table of Contents
Recent PHP Vulnerability (CVE-2024-4577)
A vulnerability has been found in PHP known as CVE-2024-4577 (CVSS score: 9.8) has an impact on many devices. Hackers are using this bug to put harmful software in systems. They’re adding remote access trojans, tools for mining crypto, and networks for DDoS attacks. This problem lets attackers run malicious commands from far away on Windows computers that use Chinese and Japanese languages.
Akamai’s research team spotted hackers trying to exploit the PHP vulnerability within a day of its public announcement in early June 2024. These attacks aim to spread Ghost RAT, RedTail, XMRig crypto miners, and the Muhstik DDoS botnet. In May, Imperva also found that hackers behind TellYouThePass ransomware were using CVE-2024-4577 to spread a .NET version of their file-locking malware.
People and companies using PHP should update to the newest version to protect against these active threats. The shrinking gap between when a bug is revealed and when hackers start using it poses a serious security risk.
Get in!
Join our weekly newsletter and stay updated
Common PHP Vulnerability
Whether you hire PHP developers or utilize your in-house team to create an app or website, it’s crucial to be aware of common PHP vulnerabilities. To assist you, we have detailed these vulnerabilities here.
Cross-Site Scripting
A widespread security flaw in PHP happens when hackers sneak harmful JavaScript or HTML code into your site. This allows them to steal user cookies and passwords or get admin access.
Prevention Tips
- Put in place strong checks to make sure user input doesn’t contain harmful scripts. Clean and verify all data that users provide.
- Always encode data that’s sent out to stop HTML or JavaScript code from running in the browser when it shouldn’t. Use the right encoding functions for different situations.
- Set up a Content Security Policy (CSP). This policy spells out which sources can provide content like scripts, stylesheets, and images. Its goal is to stop unauthorized scripts from running on web pages.
- Add the “HttpOnly” flag to cookies. This keeps scripts on the client side from getting their hands on sensitive cookie data.
- Put context-aware output filtering into action based on the specific output context (like HTML, JavaScript URL). Use security libraries or frameworks that have built-in output filtering systems to handle context-specific encoding.
- Carry out regular security checks, look for vulnerabilities and test for weak points to find and fix any possible XSS weak spots in your PHP application.
Cross-Site Forgery
CSRF (Cross-Site Request Forgery) tricks your browser into clicking a harmful link. This link can steal your session info, override your access without you knowing, or send commands that look real to the server on a trusted site where you’ve logged in. Hackers take advantage of this trust to do things you didn’t agree to pretending to be you.
Prevention Tips
To protect against CSRF, a PHP vulnerability, you need to add a unique CSRF token to all forms and AJAX requests.
- Check the CSRF token on the server before you process the request.
- You can also use SameSite cookies and anti-CSRF libraries to give more protection from CSRF attacks.
SQL Injection
SQL injection is a type of cyber attack that targets databases by inserting malicious SQL code into a database query through an application’s input fields. The goal of an SQL injection attack is to manipulate the structure and behavior of the database query, enabling the attacker to access, modify, delete data, or even execute arbitrary commands.
Prevention Tips
- Split user input from SQL code by using parameterized queries or prepared statements.
- Put input validation and sanitization in place on the server side.
- Give application accounts the smallest database privileges possible to follow the principle of least privilege.
- Cut down on creating dynamic SQL and stay away from building queries with input from users.
- Teach developers how to code and check code often to find weak spots.
- Think about using a Web Application Firewall (WAF) to spot and stop attempts at SQL injection.
- Keep software up to date with the newest security patches.
- Conduct security testing, to identify and address vulnerabilities.
Remote Code Execution
Remote Code Execution (RCE) is a PHP vulnerability that allows attackers to execute their code remotely on a target system. This occurs when PHP code lacks proper security measures, enabling unauthorized code execution. RCE vulnerabilities can result in unauthorized access, data manipulation, and system control.
Prevention Tips
To mitigate RCE vulnerabilities in PHP applications, it is crucial to adhere to secure coding practices, including:
- Check and clean all user input before you put it in PHP code to stop malicious code from getting in.
- When you work with databases, use parameterized queries or prepared statements to prevent SQL injection attacks.
- Keep PHP and its libraries up to date to get security fixes and bug repairs.
- Set strict access rules on the server to stop unauthorized code from running.
- A WAF can spot and block attempts to exploit RCE weak spots.
Book Your Free Cybersecurity Consultation Today!
How PHP Security can be Improved?
Here are the top methods to enhance the overall security of PHP applications.
- Keep PHP, libraries, and frameworks up to date with the latest versions to take advantage of security patches and bug fixes.
- Adhere to secure coding practices, including input validation, output encoding, and proper user data handling, to prevent vulnerabilities.
- Use robust password hashing algorithms and consider implementing multi-factor authentication (MFA) for enhanced security.
- Sanitize and validate user input to prevent cross-site scripting (XSS) vulnerabilities.
How can Kratikal help you Prevent PHP Vulnerabilities?
Kratikal offers a comprehensive range of cybersecurity services to help prevent vulnerabilities in PHP applications. Our expert team conducts thorough vulnerability assessments and penetration testing, performs detailed secure code reviews, and implements Web Application Firewalls (WAF) to protect against common web attacks. We also provide regular security audits, continuous monitoring, incident response, and patch management to keep your applications secure. Additionally, our training programs and consulting services equip your development team with the knowledge and strategies needed to build and maintain secure PHP applications, ensuring your digital assets remain protected against evolving cyber threats.
Ref: https://thehackernews.com/2024/07/php-vulnerability-exploited-to-spread.html








Leave a comment
Your email address will not be published. Required fields are marked *