As traditional IT infrastructure proves inadequate for evolving business requirements. They are identified by experts who understand complex behaviors and ensure effective risk management. To effectively manage these risks without compromising their core operations, organizations need to implement cloud security services. To effectively manage these risks without compromising their core operations, organizations need to implement cloud security services.
In this blog, we will talk about cloud security services in detail.
Table of Contents
What Do You Mean by Cloud Security Services?
Cloud pentesting services include a range of offerings designed to reduce risk and maintain compliance in the cloud environment. Instead, specific areas to be addressed are occupied by most of these projects, a concept that will be briefly examined. Outsourcing security offers many benefits such as:
- Threats can be effectively managed, identified by experts who understand complex behaviours, and ensure effective risk management.
- Managed cloud security service providers are trained to help organizations achieve compliance, an area often beyond their expertise.
- The IT team is relieved from managing cyber incidents, enabling them to concentrate on supporting core business operations.
Get in!
Join our weekly newsletter and stay updated
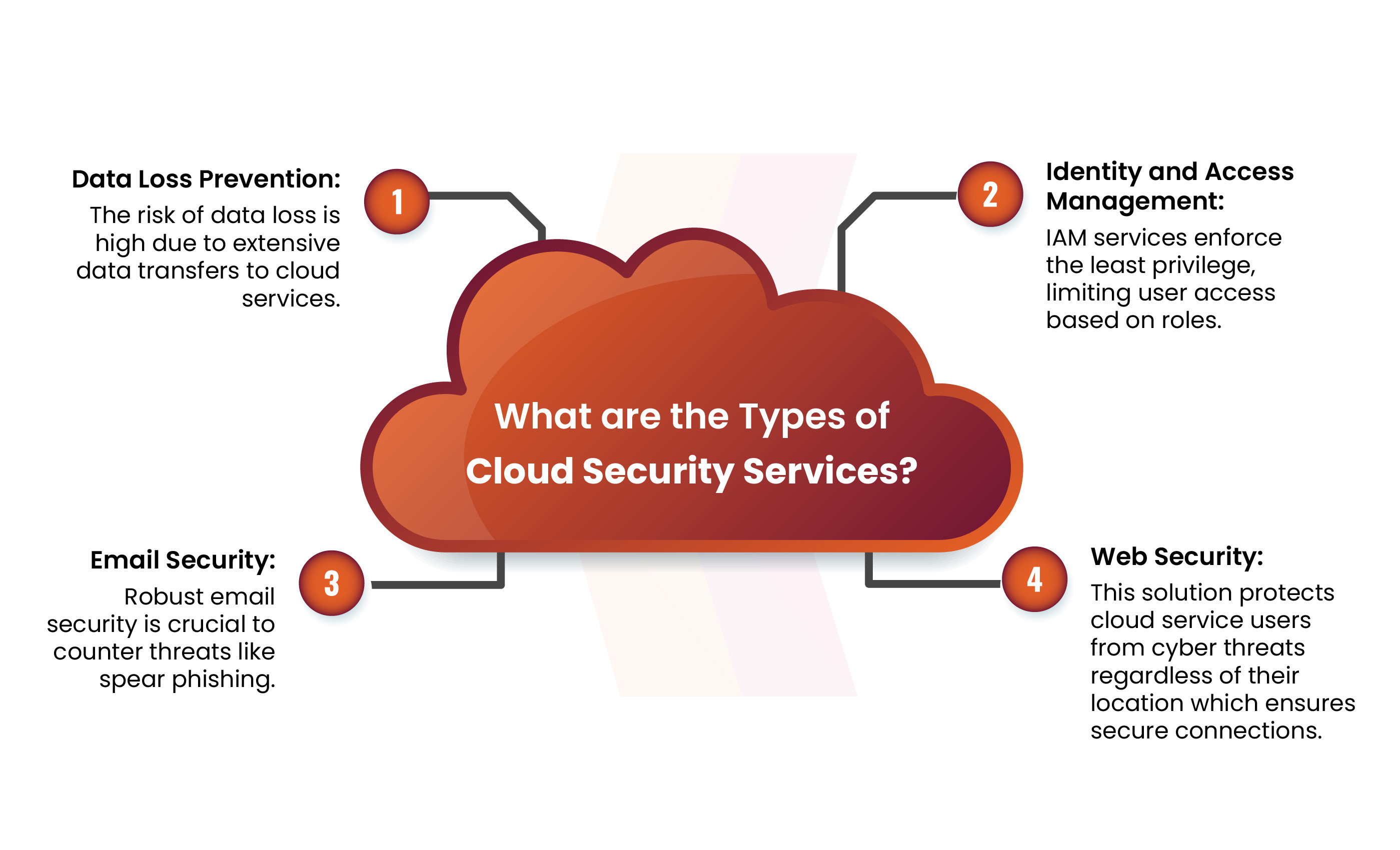
Types of Cloud Security Services
A cloud environment characterized by a mix of technologies and processes can be complex and vulnerable to threats. Therefore, it is generally impossible to encounter a universal cloud security service. Instead, most businesses target specific products. Typical cloud security services include:
Data Loss Prevention
Due to the substantial amount of data created and transferred to cloud pentesting services, along with the widespread access to this data by numerous devices and apps, there is a significant risk of data loss. Sensitive information, including social security numbers, credit card numbers, and virtual Protected Health Information (ePHI), is supposed to be discovered by DLP offerings to prevent unauthorized access.
Identity And Access Management
These services enforce the least privilege, limiting user access and actions to their designated roles. For instance, standard users should not have permission to create instances or delete snapshots, which an IAM (Identity and Access Management) service can enforce. Through an IAM service, administrators can create permission policies and assign them to individual users or user groups.
Email Security
Users commonly perceive the most vulnerable aspect of the security chain, which is frequent targets in cyberattacks. Some of the attacks pose a risk to cloud environments, such as spear phishing attempts targeting cloud administrator credentials. Implementing a robust email security service capable of detecting phishing emails and malicious attachments is a method to mitigate threats.
Web Security
Users can access cloud pentesting services from a variety of locations, including their head office, home office, branch locations, and beyond. Web security solutions between users, regardless of their location and internet access, provide businesses with the tools to secure these networks and defend against cyber threats.
Best Practices of Cloud Security Services
With so many cloud pentesting services available in today’s market, integrating them in an effective and secure way can be a challenge In the following sections, we will outline some best practices for providing cloud security services implementation has been greatly improved.
Before starting any cloud security initiative, it’s important to take a role in shared security responsibilities. Typically, your project deals with cloud security when you are running security in the cloud. Different cloud service models, such as Software as a Service (SaaS) and Infrastructure as a Service (IaaS), may interpret these models differently, ensuring organizations consider them accordingly.
Address Security Policy and Procedure Concerns
Although large cloud providers implement different security measures, the presence and extent of these controls can vary between providers. Therefore, it is important to understand the specific security measures in place and associated with them.
How do they prepare for disasters? Do they have documentation showing how their security measures meet legal standards? What measures are in place for access control, encryption, and backup? How comprehensive is their technical support, including availability? These questions arise.
Implementation of Cloud Security Services
For a seamless implementation of your cloud security program, document all pertinent policies, processes, and procedures. These will act as guidelines for all members of your organization. Leadership must actively encourage employee adherence and lead the implementation of these security policies.
Book Your Free Cybersecurity Consultation Today!
How does Kratikal help to enhance Cloud Security Services?
Kratikal, a CERT-In empanelled auditor enhances cloud pentesting services aimed at testing the cybersecurity posture of a cloud-based environment through simulated attacks to identify and address vulnerabilities. We help to mitigate cyberattacks by offering a range of services, including compliance and risk management, network and cloud security, and web and mobile application security. The testing method uses the most vulnerable areas in cloud applications as well as prioritizes and provides actionable solutions to enhance. Kratikal focuses on platforms such as Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform, etc. Our approach is based on best practices and we automate cloud security testing tools and manual techniques are used to identify security vulnerabilities.
Conclusion
Cloud security offerings are varied and include intrusion detection, web security, email security, identification, and access management, and data loss prevention a they will be prevented. Each of those functions plays an important role in protecting the assets stored in the cloud and mitigating risk. Companies using cloud solutions face a new and complex security environment. It is important to use cloud security services to mitigate risk while focusing on core operations. It includes checking to see if the target server is behind a firewall, checking S3 to trace resources installed in the cloud, and authority to determine whether the threat actor has the ability to write to the target machine.








Leave a comment
Your email address will not be published. Required fields are marked *