Security is getting harder to centralize as the nature of remote work changes and more businesses abandon the physical office. End users are scattered more widely, and Work From Anywhere is getting more and more popular. With devices and users spread out throughout the world, how are you ensuring the security of your business? The solution is no longer an internal server room. Decentralizing your cybersecurity rules is rapidly turning into a requirement. By using this approach, any device, wherever it may be, is secured.
In order to distribute security responsibilities and safeguard data everywhere while keeping a high level of technological flexibility, decentralized security is being used in companies of all shapes and sizes.
Table of Contents
Get in!
Join our weekly newsletter and stay updated
What is Decentralized Cyber Security?
It is described as a comprehensive network of proactive and reactive defenses that monitor targets across endpoints in the cloud and on-premises regardless of where they are, what they do, or who they connect with. Risk management and security enforcement are made possible throughout the entire organization via decentralized security. It gives each team more authority and makes security everyone’s responsibility. It incorporates security into system architecture so that it can be weaved throughout every component of your IT infrastructure, thereby assisting in protecting your company.
Advantages of Decentralized Cyber Security Model –
The policies created under this paradigm are in line with the distinctive business models of each unit, which is a benefit. Additionally, when adjustments or actions are required, the departments can decide quickly and effectively without relying on one another. To get a thorough knowledge of it, let’s talk about a few more of them.
- Increased company-wide understanding of information security.
- Facilitates quicker innovation.
- More independence to pursue company objectives.
- Employees assume more responsibility for risk.
- Each department has information security built in.
Disadvantages of the Decentralized Cyber Security Model –
- There is a lack of uniformity within the company.
- Risk can be missed or mischaracterized, necessitating greater and more consistent communication.
- Strong central support and direction are still needed.
Protecting all of your digital assets at each endpoint without relying on a conventional perimeter is the aim of decentralized cybersecurity. In order to better ensure that you neutralize any potential threat, your infrastructure is protected by a number of tiered and adaptable safety nets that are designed to catch intruders at all of the various points.
Trending Way to Adopt Decentralized Cyber Security–
By now, it should be obvious why decentralized cybersecurity is superior to centralized methods in so many ways. If these benefits alone aren’t enough to persuade you of the value of decentralizing, take into account the numerous global trends that call for a more decentralized approach to cybersecurity:
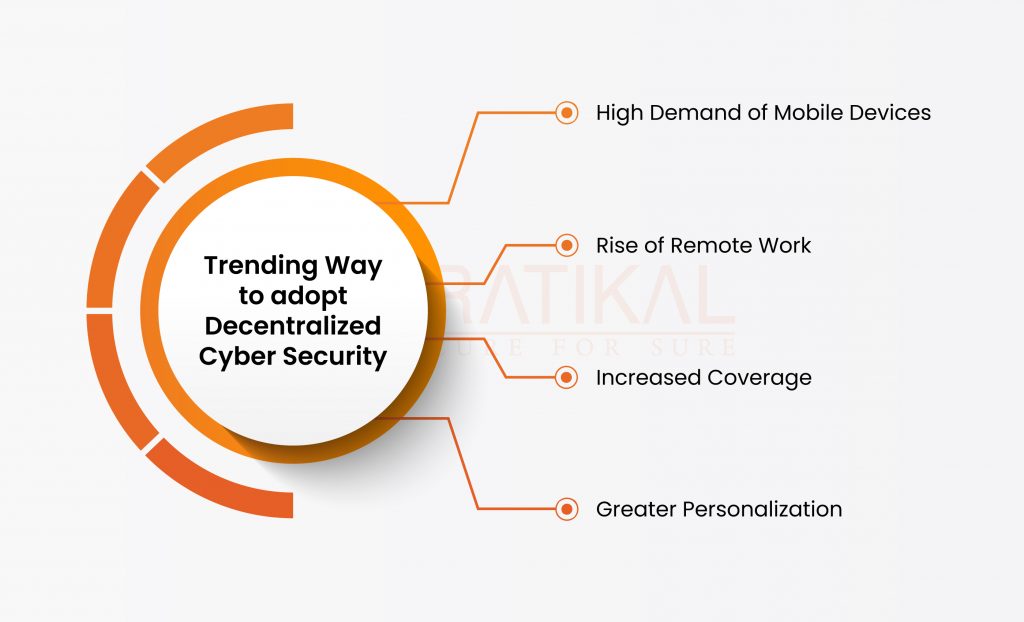
- High Demand of Mobile Devices – Although it isn’t a brand-new trend, the spread of mobile devices is also not one that is going away. There will be additional endpoints to secure as a result of modern enterprises’ requirement to enable mobile working for their staff. Mobile devices can be brought inside the security of a company’s network with the help of decentralized cybersecurity.
- Rise of Remote Work– Prior to March 2020, many businesses were already shifting to remote and hybrid work arrangements, but the pandemic forced almost every industry to reconsider how they may jump on the remote work train. However, remote work puts a pressure on a single channel’s capacity to continue guarding all of a company’s digital assets.
- Increased Coverage – Decentralization not only broadens coverage but also narrows it down. Businesses that adopt decentralized cybersecurity safeguard every endpoint that requires protection and don’t waste resources safeguarding assets that aren’t being used for whatever reason. Decentralized cybersecurity makes sure that each user has their own personal, always-deployed, cutting-edge shield.
- Greater Personalization– Compared to conventional cybersecurity systems, decentralized cybersecurity can offer a set of security measures that is far more tailored to an enterprise. Decentralized cybersecurity is exactly what it sounds like: a flexible, scalable answer to any company’s cybersecurity demands.
Decentralized cybersecurity excels in this area because it enables IT to expand the protected network with additional devices while maintaining security. The fundamental concept of decentralized cybersecurity is straightforward: rather than securing a system as a whole, IT experts concentrate on safeguarding the endpoints of that system.
A paradigm shift like this cannot be introduced in a single, ideal way. Instead, it is the responsibility of IT experts to assess their own networks to determine what advantages a decentralized strategy for cybersecurity might offer and how to start moving in that direction.
Embrace Decentralized Cyber Security With Kratikal–
Today, numerous teams are under tremendous pressure to speed up time to market while managing and managing their own application deployment. This has a significant impact on how businesses view their need to secure their systems. Decentralized security shifts duties and controls from the center to the particular regions that are currently most susceptible to attack. Risk management and security enforcement are made possible by decentralized security throughout the entire organization. It gives each team more authority and makes everyone accountable for security. It incorporates security into system architecture so that it may be integrated into all facets of your IT infrastructure, protecting your company.
If your business is prepared for this impending shift and is willing to make the necessary adjustments, the professionals at kratikal, a CERT-IN Empanelled organization, will assist you in integrating VAPT services into your security programme. Kratikal offers decentralized cyber security, which has so far proven to be useful. We also offer security auditing for Compliance, including ISO/IEC 27001, GDPR, PCI DSS, and many more, to help your business to decentralize the security of the organization..
Decentralized cybersecurity enables businesses to appropriately decentralize their IT infrastructure and provide their staff with the flexibility and freedom to perform what they do best, in a secure environment.
What are your thoughts on the matter? Share your thoughts about Decentralized Cyber Security in the comment section below!








Leave a comment
Your email address will not be published. Required fields are marked *