A survey indicates that more than 98% of mobile applications lack security. This is primarily attributed to a common misconception in app development practices, where mobile application testing is often deferred to the final stages of the development cycle or, in some cases, completely neglected. Developing a mobile app responsibly requires a thorough consideration of its security throughout the build process. However, implementing mobile application security tests can be challenging.
Mobile app testing identifies vulnerabilities using methods similar to those used by hackers. This process occurs prior to the app’s production to guarantee a flawless implementation without any errors. Mobile application testing is done on Windows, iOS, and Android. In this blog, we will discuss why mobile application testing is important for organziations and how to conduct it.
Table of Contents
Why is Mobile Application Testing Important for Organizations?
Mobile application testing is essential to ensure that mobile applications are secure, trustworthy, and function as efficiently as feasible overall. It is essential to provide a flawless user experience and preventing issues that can compromise the functionality of the app. The following are the main factors emphasizing the significance of testing mobile applications:
Predict and Prevent Cyber Attacks
One cannot be certain whether hackers will breach a mobile app, target backend systems, or pilfer data. However, one can anticipate potential scenarios and mitigate associated risks by predicting hacker behaviors. By conducting a penetration as a service, sophisticated tools and advanced IT knowledge are employed to simulate an attacker’s actions, revealing code vulnerabilities and allowing for preemptive fixes before exploitation.
Introducing the New Mobile App
Prior to deploying a new mobile application into an IT environment, it undergoes essential technical and user acceptance testing to confirm alignment with both technical specifications and business needs. These tests ensure user satisfaction and supportability for IT teams. In addition to meeting technical and user criteria, the mobile app testing must fulfill operational requirements to maintain the production environment and avoid introducing security risks. Software engineers and security experts emphasize adopting a security-first approach from the initial idea through Design, Build, Go-live, to routine RUN and Support activities.
Identify the Mobile App Architecture
During mobile app testing, identifying vulnerabilities is crucial to preventing potential security breaches post-launch. With insights into source code flaws, attack vectors, bottlenecks, and security holes beforehand, adjustments to the architecture, design, and code can be made. Addressing issues early is cost-effective, covering technical, legal, PR, and other aspects. It prevents complications in the app’s architecture or breaches later on.
Reduction in Cost
Businesses conduct application security testing primarily to save costs and resources. Despite the initial investment in advanced testing tools, it pales in comparison to the expenses incurred for remediation. Early mobile app testing in the development process allows for the timely discovery and resolution of vulnerabilities. By assessing applications before launch, businesses can pinpoint flaws in source code, bottlenecks, and security gaps, addressing them before the app reaches users.
Book Your Free Cybersecurity Consultation Today!
Mobile Application Security Threats
Exploring strategies and steps to assess the security of mobile apps necessitates a grasp of the prevailing types of security threats.
Data Theft
Data is a vital business asset, and the primary concern for mobile apps is the potential for information theft. Apps frequently store substantial data without sufficient security measures, whether through app permissions, credentials, or the handling of sensitive information. A noteworthy instance of data theft is illustrated by the concept of ‘riskware,’ which encompasses apps transmitting user data to remote servers exploited by cyber attackers.
Session Handling Issues
Mobile apps commonly use session tokens to enable users to execute various functions without requiring a logout or re-authentication. However, mishandling or sharing of these session tokens with threat actors can result in improper session management, providing hackers with an opportunity to act as part of users and access their data.
Broken Cryptography
Weak cryptography or improper usage undermines the effectiveness of encryption. Initially, the mobile app may employ a flawed encryption or decryption process that can be exploited by adversaries to decrypt sensitive data.
Reverse Engineering
This is a common security threat prevalent in mobile apps. This method enables hackers to acquire comprehensive insights into the application’s source code, algorithms, libraries, and other assets. Later, the data is used to exploit app vulnerabilities, allowing unauthorized access to servers and compromising proprietary and user information.
Get in!
Join our weekly newsletter and stay updated
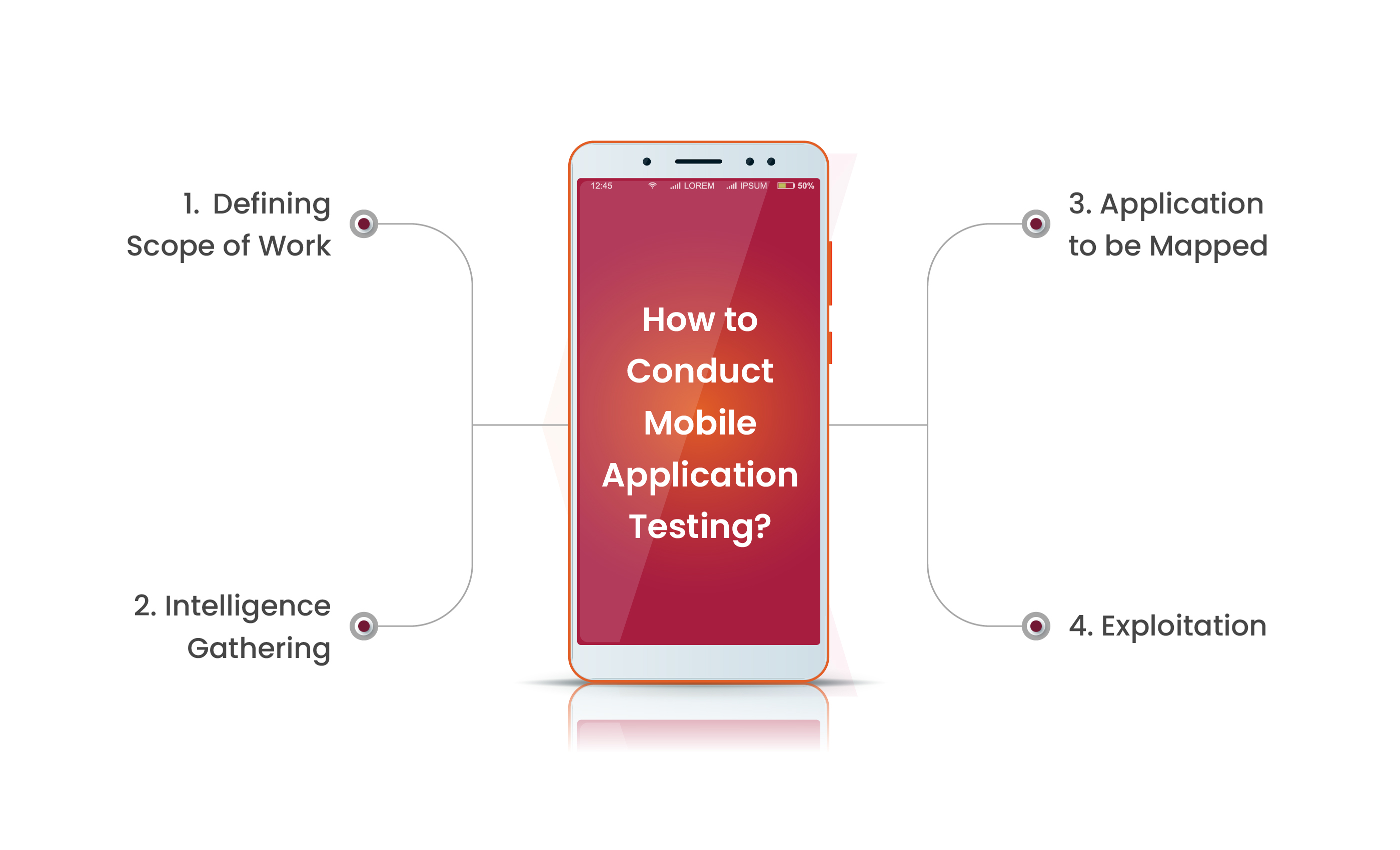
How to Conduct Mobile Application Testing?
Mobile app testing is a comprehensive approach that protects user information and system integrity by identifying and fixing any vulnerabilities. Here are key steps to perform effective mobile application security testing:
Defining Scope of Work
The mobile application’s scope includes determining the implemented security measures, testing objectives, and handling sensitive information. Essentially, this step involves thorough client collaboration, ensuring both the client and examiner reach an agreement to safeguard against legal actions.
Intelligence Gathering
It involves gathering information about potential threats to individuals or organizations and utilizing this information for protective purposes. To establish a comprehensive understanding of the application, this stage entails analyzing its design and scope.
Application to be Mapped
The subsequent step is application mapping, encompassing both manual and automated scanning of programs to conclude the preceding phase. Mapping provides testers with enhanced insights into the program under examination, including entry points, stored data, and other potential significant vulnerabilities.
Exploitation
This phase involves security testers exploiting vulnerabilities discovered in the earlier process to gain access to the application. It is crucial at this juncture to discern actual weaknesses and strengths within the system.
Reporting
The final evaluation report, derived from the reporting and analysis phase, is a pivotal outcome of the entire assessment process. An essential moment for the client occurs when security testers articulate the identified weaknesses in applications and explain the potential negative repercussions.
Conclusion
Mobile application testing emerges as a critical shield against the prevalent vulnerabilities that jeopardize the integrity of mobile apps. Recognizing the need for security in app development, this process not only rectifies the common misconception leading to insufficient security but also plays a pivotal role in protecting user data. The exploration of security threats, coupled with strategies for comprehensive testing, emphasizes the significance of early detection and remediation. From defining the scope to the final reporting phase, a meticulous approach is essential to protect against cyber threats, ensuring that businesses not only meet technical and user criteria but also foster trust by prioritizing security throughout the app development journey.
As a CERT-In empanelled organization, Kratikal is equipped to enhance your understanding of potential risks. Our manual and automated Vulnerability Assessment and Penetration Testing (VAPT) services proficiently discover, detect, and assess vulnerabilities within your IT infrastructure. Additionally, Kratikal provides comprehensive security auditing services to ensure compliance with various regulations, including ISO/IEC 27001, GDPR, PCI DSS, and more, assisting your business in adhering to legal requirements set forth by diverse governments.








Leave a comment
Your email address will not be published. Required fields are marked *