As cloud computing continues to advance, companies are ramping up investments in these transformative technologies. However, the broader adoption also introduces higher security risks, making cybersecurity a top priority for global organizations in 2024. A critical component of cybersecurity is compliance, which plays a key role in mitigating cloud security issues. One of the leading security standards in this area is ISO/IEC 27017:2015, designed specifically for cloud data security, cloud service providers, and cloud computing.
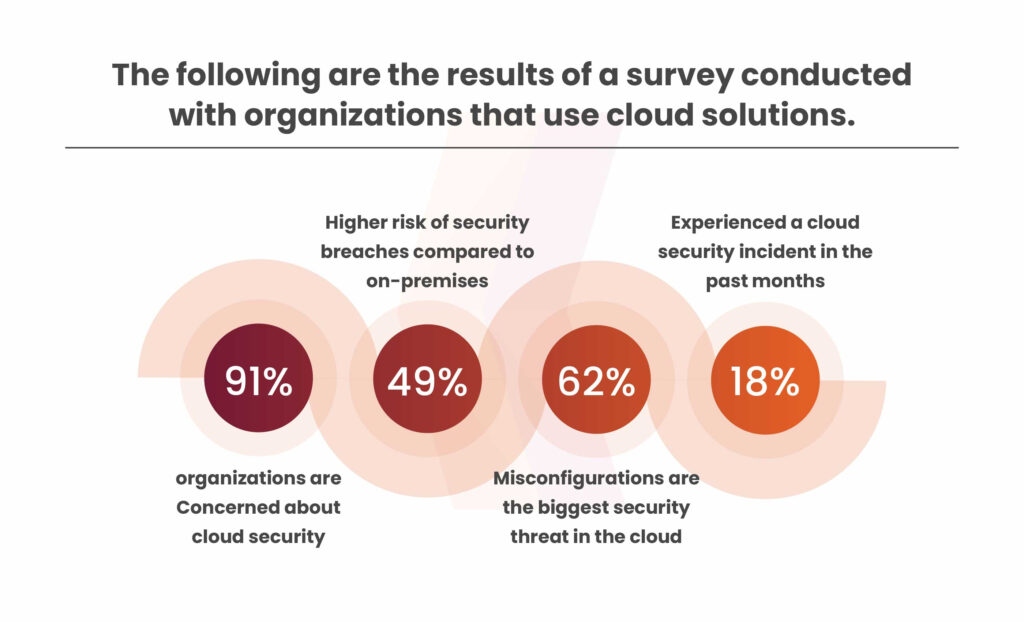
In this blog, we will explore ISO 27017 and its role in cloud security.
Table of Contents
What is ISO 27017 Compliance?
ISO 27017: 2015 standard is a comprehensive framework for cloud security that focuses on providing guidance for information technology controls and security techniques specifically tailored for cloud services. It offers additional controls beyond those in ISO/IEC 27002, with a total of 37 controls based on ISO 27002 and 7 exclusive controls. These controls cover key areas such as shared roles and responsibilities within a cloud computing environment, removal and retrieval of customer assets post-contract termination, and much more. ISO 27017 is designed to help organizations, both cloud service providers and cloud service customers, enhance their security posture in the cloud environment and reduce the risk of security breaches.
Scope of ISO 27017 Compliance
ISO 27017 is applicable to cloud service providers that have implemented an Information Security Management System according to the requirements set forth in ISO 27001. Additionally, it evaluates seven controls that are unique to cloud service providers:
- The roles and responsibilities of customers and service providers concerning cloud computing and security.
- The deletion and retrieval of data upon the termination of customer contracts.
- Ensuring the protection and isolation of a customer’s virtual environment from others.
- Implementing machine hardening practices or minimizing the vulnerability surface in line with business needs.
- Defining the operational responsibilities of administrators.
- Facilitating monitoring capabilities for cloud customers.
- Aligning security management practices for both physical and virtual cloud computing environments.
Role of ISO 27017 in Cloud Security
ISO 27017 plays a critical role in strengthening cloud security by offering a specialized set of guidelines tailored for cloud environments. Building on the Information Security Management System (ISMS) foundation of ISO 27001, ISO 27017 provides specific controls that address unique challenges in the cloud. These include safeguarding data privacy, ensuring secure data deletion upon contract termination, and protecting virtual environments from unauthorized access or data breaches. It also clarifies the responsibilities of both cloud providers and customers, enhancing accountability and establishing best practices for monitoring and managing cloud infrastructure security. By adopting ISO 27017, organizations can better manage cloud security risks, foster customer trust, and comply with international standards, ensuring a more resilient cloud ecosystem.
Get in!
Join our weekly newsletter and stay updated
ISO 27017 Certification Process
The certification process for ISO/IEC 27017 closely resembles that of ISO 27001, encompassing control implementation, audit preparation, and both Stage 1 and Stage 2 audits, along with a three-year certificate lifecycle. Additionally, ISO 27017 serves as an extension of ISO 27001; therefore, an organization seeking ISO 27017 certification must either already hold ISO 27001 certification or pursue certification for both ISO 27001 and ISO 27017 simultaneously.
The detailed process of ISO certification:
Gap Analysis
The initial step toward achieving ISO 27017 compliance is to evaluate your existing cloud security practices against the requirements of ISO 27017 and identify any gaps.
Once you’ve pinpointed the areas where your practices fall short of the standard’s criteria, create a remediation plan to address these gaps. Ensure that your plan includes specific timelines, required resources, and designated individuals responsible for implementation.
Control Implementation
Next, implement the required cloud-specific controls, ensuring that both Cloud Service Providers (CSPs) and Cloud Service Customers (CSCs) understand and fulfill their respective responsibilities. Create or update documentation to accurately reflect these controls, including relevant policies and procedures, and make sure these documents are accessible to all stakeholders. If needed, conduct training sessions to increase awareness among personnel about cloud security, highlight the specific risks relevant to the business, and explain the policies and processes in place so that everyone understands their roles and responsibilities.
Internal Audit
After implementing controls and addressing any compliance gaps, conduct an internal audit to evaluate the effectiveness of your cloud security controls in practice. Document any necessary corrective actions based on the audit results.
Share audit findings with senior management to highlight leadership’s commitment to supporting ISO 27017 compliance and ensuring robust cloud security.
Certification Audits
While preparing certification audit elect an accredited and experienced certification body for ISO 27017. The audit process mirrors that of ISO 27001, with two stages. In the Stage 1 Audit (Pre-assessment), the certification body reviews your documentation and readiness, identifying any issues that must be addressed before moving to the Stage 2 Audit (Certification audit). The Stage 2 Audit then involves an in-depth evaluation of the implementation and effectiveness of your cloud security controls through interviews, observations, and control testing. Upon satisfactory results, the certification body issues the ISO/IEC 27017 certification, typically valid for three years, with annual surveillance audits conducted to ensure continued compliance and to address any non-conformities.
Book Your Free Cybersecurity Consultation Today!
How can Kratikal Help you with ISO 27017 Compliance?
Kratikal can support your journey to ISO 27017 compliance by providing expertise across all stages of the certification process. From initial assessments and gap analysis to identifying cloud-specific controls, Kratikal’s team ensures your organization meets all ISO 27017 requirements. Their experts can assist in developing and updating documentation, implementing tailored security controls, and training personnel to raise awareness about the risks and compliance obligations. Furthermore, Kratikal offers internal audit services to evaluate the effectiveness of your controls and prepare you for the external certification audit, providing ongoing support to maintain compliance through regular assessments and guidance. For more information, refer to Kratikal’s ISO 27017 compliance services.
FAQs
- What is the scope of ISO 27017?
ISO 27017 provides guidelines and controls specifically aimed at enhancing information security in cloud computing environments. It addresses the distinct challenges and risks involved in adopting and using cloud services.
- What is the ISO 27017 code of practice?
ISO 27017 is a standard focused on guiding information security in cloud computing, offering recommendations and support for implementing cloud-specific security controls.








Leave a comment
Your email address will not be published. Required fields are marked *