Router vulnerabilities present significant risks to both individuals and organizations. One such vulnerability has been identified in the TP-LINK Archer series, specifically affecting the Archer C5400X Tri-Band Gaming Router. Our recent analysis, conducted using our cutting-edge binary zero-day identification feature, revealed multiple severe vulnerabilities, including Remote Code Execution (RCE). In this blog, we will discuss how OneKey discovered the vulnerability.
Table of Contents
What Happened in TP-Link Archer C5400X?
The vulnerability identified in the TP-Link Archer C5400X gaming router, designated as CVE-2024-5035, poses a significant risk due to its potential for remote code execution. This flaw, with a severity score of 10.0 on the Common Vulnerability Scoring System (CVSS), affects all firmware versions preceding 1_1.1.6. The exploit revolves around a binary component called “rftest” within the router’s firmware, which inadvertently opens up a network listener on TCP ports 8888, 8889, and 8890.
By crafting and sending specific requests to these ports, malicious actors can inject commands containing shell meta-characters, enabling them to execute arbitrary code on the device remotely. To address this critical security issue, TP-Link has released a patch in firmware version 1_1.1.7 on May 24, 2024. This update mitigates the vulnerability by filtering commands with problematic special characters, safeguarding the router and ensuring network security for users.
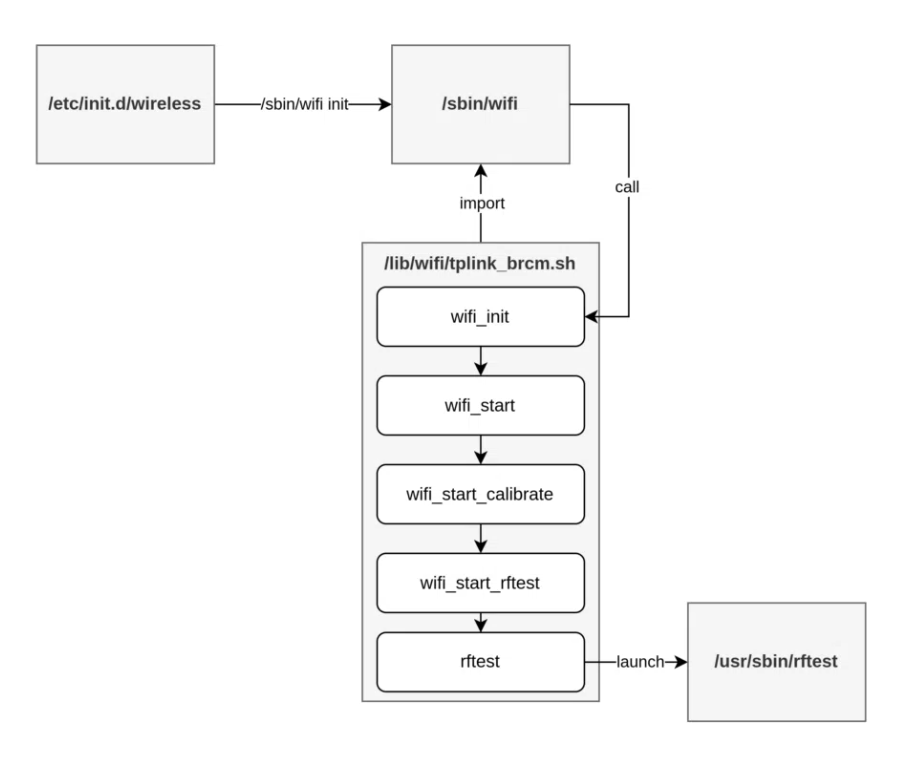
OneKey’s binary static analysis pipeline identified a command injection vulnerability in the TP-LINK Archer C5400X router. The flaw originates from a TCP socket listening on port 8888, where user input is read and propagated to two different popen() calls if the input contains “wl” or starts with “nvram” and contains “get”. The vulnerable rftest binary launches at boot, starting a TCP server on port 8888 that accepts specific commands. This command restriction can be bypassed by injecting commands with shell meta-characters like ;, &, or |, allowing arbitrary command execution. TP-Link addressed the issue by discarding any commands containing these meta-characters.’
So the the remote code execution was affected by a binary file called rftest when the binary starts a network it allows the injection attack on the device.
Impact of Remote Code Execution
The impact of a successful Remote Code Execution (RCE) attack can be risky for both businesses and individuals. Key outcomes of RCE attacks include:
Loss of Sensitive Information
This could involve personal data, such as social security numbers and credit card information, or corporate data, like trade secrets, customer databases, and financial records. Such data loss can result in monetary loss, reputational damage, compliance risks, and legal exposure.
Disruption of Services
For businesses, this could result in the disruption of essential services, leading to lost revenue and diminished customer trust. In the case of critical infrastructure, such as power grids or hospitals, the consequences could be even more severe, potentially putting lives at risk.
Gateway to Most Sensitive Data
For example, an attacker might gain control of a non-sensitive system and then move laterally to access mission-critical systems. This can potentially lead to the compromise of the entire corporate network.
Ways to Prevent and Mitigate RCE Attacks
Below is the list of how RCE attacks can be prevented:
Secure Coding Practices
Secure coding practices are the first line of defense against RCE attacks. Developers should write code with security in mind, following principles such as input validation, least privilege, and defense in depth. Regular code reviews and security audits are essential to identify and fix potential vulnerabilities before they can be exploited.
Patching and Updates
Regular patching and updates are vital for preventing RCE attacks. Software vendors often release patches to address known vulnerabilities, and it is crucial for organizations to apply these updates promptly. Delayed patching can leave systems susceptible to attacks, as demonstrated by the Zerologon exploit.
Vulnerability Scanning and Penetration Testing
Vulnerability scanning and penetration testing are essential for identifying potential security weaknesses in a system. These techniques can detect vulnerabilities that could be exploited for RCE attacks, enabling organizations to take proactive measures to mitigate the risk. Vulnerability scanning should be conducted continuously, while penetration testing, being more complex and costly, can be performed periodically.
Use Firewalls
Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS) offer an additional layer of protection against RCE attacks. RCE exploits often communicate with a remote command and control (C&C) server. These tools can monitor network traffic for suspicious activity, block potentially malicious C&C traffic, and alert administrators.
Book Your Free Cybersecurity Consultation Today!
How Kratikal Helps in Preventing Remote Code Execution?
Kratikal offers comprehensive cybersecurity solutions to shield organizations from the devastating consequences of Remote Code Execution (RCE) attacks. We follow a multi-layered approach, including vulnerability scanning to identify and patch software weaknesses, network security solutions to detect and block suspicious traffic, and security awareness training to empower employees to recognize and avoid potential threats. Kratikal’s combined strategies help organizations build robust defenses against RCE attacks, reducing the risk of data breaches, operational disruptions, and financial losses.
Get in!
Join our weekly newsletter and stay updated
Conclusion
The recent discovery of a critical remote code execution (RCE) vulnerability in the TP-LINK Archer C5400X router underscores the significant risks posed by such security flaws. This vulnerability, identified as CVE-2024-5035, has been effectively mitigated by TP-Link’s prompt release of a firmware update. However, the incident highlights the importance of proactive cybersecurity measures, including secure coding practices, regular patching, vulnerability scanning, penetration testing, and the use of firewalls and IDS/IPS systems.
Kratikal provides businesses with a wide range of cybersecurity solutions & services. Trusted by over 450+ SMEs and Enterprises worldwide, Kratikal delivers robust cybersecurity solutions. We are one of the fastest-growing firms committed to safeguarding companies and organizations of different sectors, for instance, SaaS, Fintech, Healthtech, Govt., etc., against cyber risks.
FAQs
- How does RCE vulnerability occur?
Remote code execution attacks typically occur in web applications and network infrastructure. These vulnerabilities are flaws in software that enable an attacker to execute malicious code on a target system.
- What is the impact of RCE?
A Remote Code Execution (RCE) attack can lead to a comprehensive cyber attack, potentially compromising an entire web application and its web server. Additionally, RCE can result in privilege escalation, network pivoting, and the establishment of persistence within the system.








Leave a comment
Your email address will not be published. Required fields are marked *