
In May 2018, a gang called ‘Carbanak’ tricked two employees of an east European bank into opening a spear-phishing email that consisted of a malicious document containing three exploits for remote code execution in Microsoft Word. In a few minutes of opening the malicious email, the attackers installed a backdoor for deploying new payloads.
One of the payloads was called Cobalt Strike Beacon which is a ‘Carbanak’ malware tool that allowed attackers to map the internal network of the organization so that they could find admin-level credentials to move across the infrastructure.
Within the period of two hours, the attackers managed to compromise a critical infrastructure component and get a hold on admin-level credentials without tripping any alarm.
For the next two months, attackers used these credentials to quietly move around the network and gained access to systems that enabled them to manipulate and withdraw funds from bank’s ATMs. The breach was discovered after a series of security alerts were eventually triggered by the credentials being used to access systems not normally associated with them.
How could the ‘Carabanak’ attack have been prevented?
With the help of reporting tool Threat Alert Button or TAB, bank employees could have reported email that seemed suspicious in nature. Once the email would have got reported, the security team would have verified the nature of that email. This would have eventually prevented the attack.
Let us now understand the detailed process of TAB’s working.
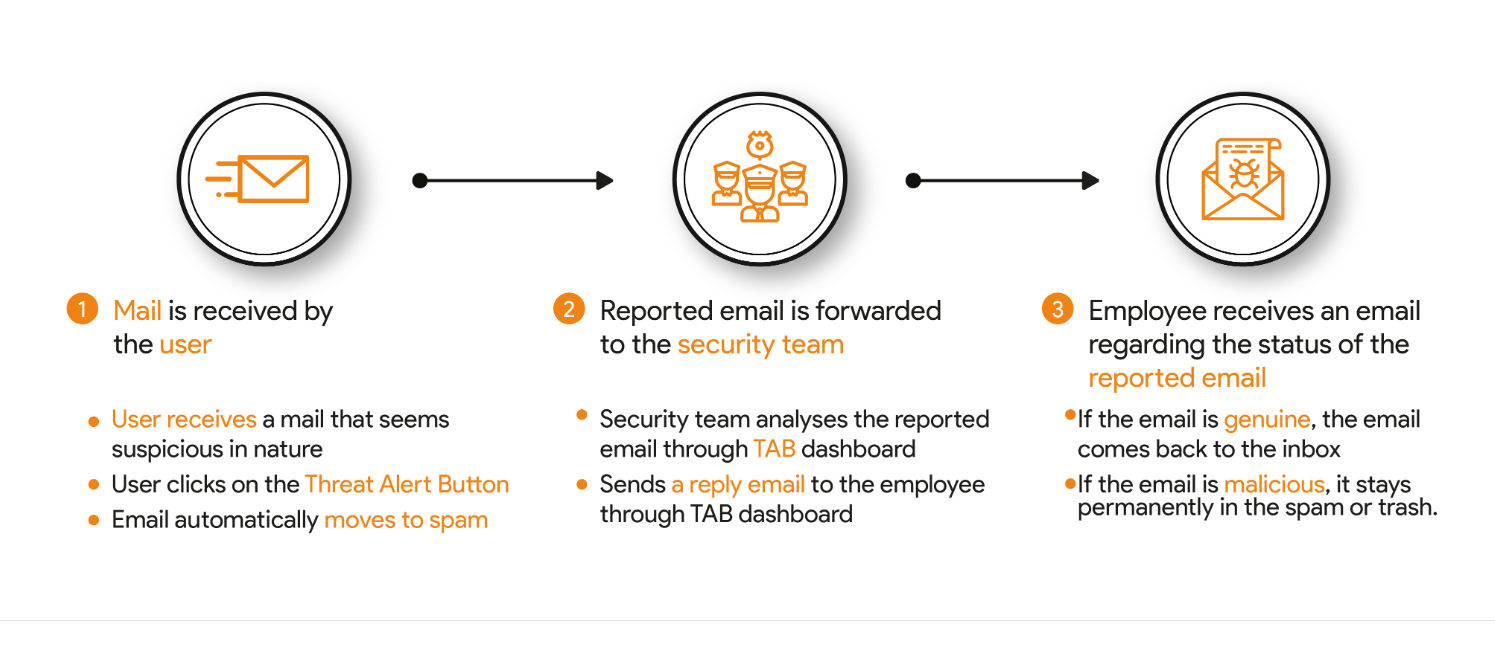
- Employee finds the email suspicious in nature
With TAB, if an employee finds a received email suspicious in nature, he can instantly report it to the security team of his organization by clicking on the reporting button.
- Reported email is forwarded to the security team
Once the security team receives the reported email, it starts analysing the email through the TAB dashboard. The security team consists of people who have the expertise to identify even the most complex cyber-attacks.
- The employee will receive the status of the reported email
In case, the email is found to be genuine in nature, a copy of the reported email is sent to the inbox of every employee. Else, it permanently stays in the spam folder.
What are the features of TAB?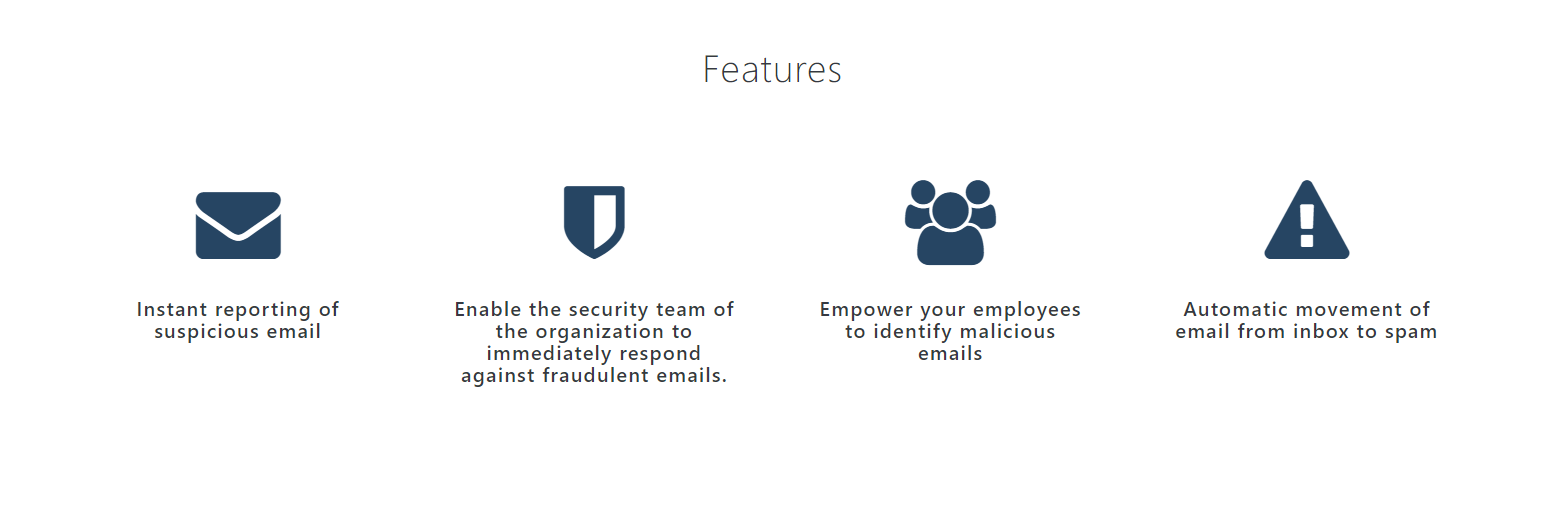
- Reporting suspicious emails instantly
In case, an employee finds an email suspicious in nature, he can click on TAB. That email will automatically move to spam and it will be forwarded to the security team.
- Responding to malicious emails
Each reported email is analyzed through GCTX. GCTX is a database that consists of millions of Indicators of Compromise including IP addresses, Domains, Hostnames (subdomains), Email, URL, File Hashes such as SHA1, SHA256, MD5, PEHASH, IMPHASH, CIDR Rules, File Paths, MUTEX name, CVE number etc. This database is updated every hour. GCTX helps in detecting threat actors present in a fraudulent email.
- Automated mitigation of cyber attacks
With the help of the reporting tool TAB, approved threat emails are moved from the inbox to spam folder for every employee in the organization. The approved fraudulent e-mail would result in blacklisting the sender’s address from every employee’s email ID within the organization.
Employee empowerment

TAB plays a huge role in empowering employees. With the power of a reporting tool, even a single vigilant employee can protect the entire organization against cyber-attacks. Since the employee who reports an actual malicious email is acknowledged, this will highly benefit your organization since most of the fraudulent emails usually remain undetected.
Most of the organizations work on web nowadays. Entire businesses are being run through email as a point of contact between organizations and customers. Hence, it has become a necessity for organizations to invest in cyber-security and cyber awareness in order to safeguard its sensitive and confidential data against from getting into the hands of cyber-criminals. Cyber-security companies like Kratikal ensure that an organization can maintain the confidentiality of its sensitive data and information without being misused by malicious entities.

