Table of Contents
Introduction
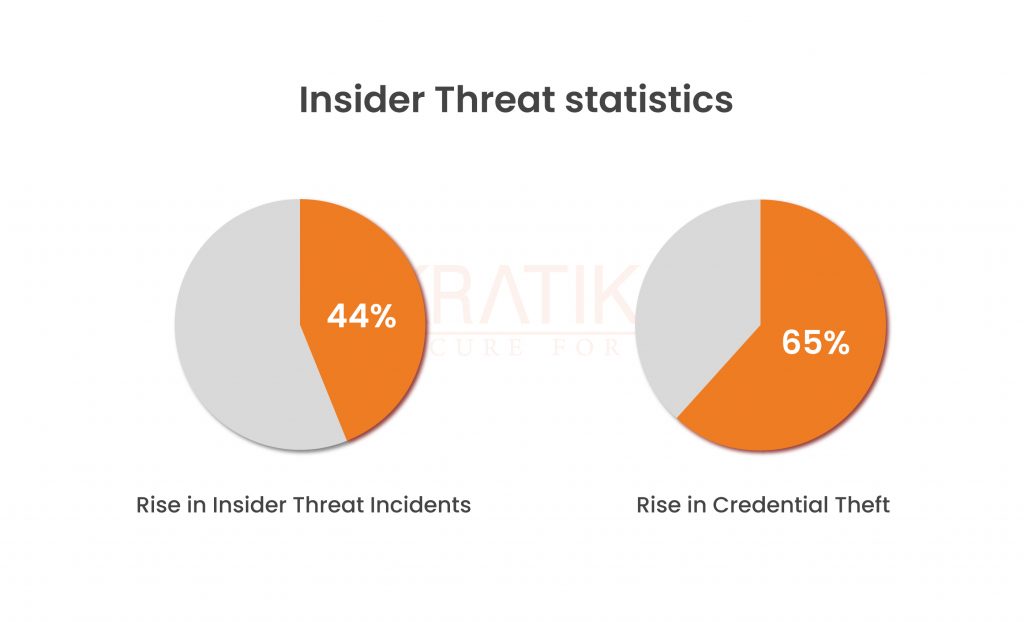
According to recent research, the cost of each incident has increased by 44% and is now $15.38 million. The primary focus is on credential theft, which has increased by a startling 65%. There is an increase from $2.79 million in 2020 to $4.6 million in 2022.
Organizations today allow employees to work remotely which is a big change or a global shift to digital technology. However, there are many risks associated with this new technology. These days, insider attacks are a serious security concern for many firms. But do you all understand the insider threat and what it entails? We all live in a world where there is a significant chance that our data will be stolen or that an insider threat would sabotage the systems.
Insider threats have changed over the past few years in a number of ways, posing dangers that businesses must manage. These include the methods by which sensitive data depart the organization and the ways that privileged access is abused. By examining a few actual occurrences that occurred as a result of this threat, we will examine the idea of insider threat in this blog.
Get in!
Join our weekly newsletter and stay updated
Define Insider Threats
The term “insider threat” refers to a human security risk that originates within an organization. The malicious actors here aren’t your typical cybercriminals; instead, your data’s security is compromised by current or former workers or contractors. They could do it consciously or unintentionally. They may do it accidentally or they can also do it intentionally.
Insider threats can be exceedingly difficult to identify because they already know where sensitive data is kept and have authorized access to it. These dangers can come in a variety of shapes and sizes, from a well-planned attack to obtain the business’s confidential information to the alteration of crucial data to an unintended but damaging data leak.
Insider Threats Cost to Organization
Have you ever considered the worrying results from the cyber security insider that many security teams might not be aware of the financial impact insider threats have on the organization? Currently, the average cost of a cyber event in large corporations can be anything from $ 2,70,000 to over $ 20 million. (https://www.coresecurity.com/blog/how-identify-and-prevent-insider-threats-your-organization)
Besides dealing with forensic difficulties to determine how the incident occurred, there are also financial losses to consider. The internal security teams will need to spend a lot of work on this to fix the problem.
Types of Insider Threats
There are several different types of insider threats, including:
- Malicious Insiders: They are staff members or company insiders who consciously aim to hurt your company. They might commit further crimes like stealing data or destroying your systems.
- Accidental Insiders: These are insiders who accidentally cause harm to your business. For example, they may unintentionally download malware, share sensitive information, or make a mistake that results in a security breach.
- Negligent Insiders: Insiders who are negligent with the information or resources of your business are these. They could disregard security guidelines or protocols, use passphrases that are too simple or obvious, or leave their machines open.
Get in!
Join our weekly newsletter and stay updated
Instances of Insider Threats
- Employee carelessness resulted in significant data losses for the city of Dallas. 8.7 million significant files—including video, pictures, audio, case notes, and other materials—that the Dallas Police Department had gathered as evidence for its cases were erased by an employee. The family violence unit was the owner of the majority of the erased material.
- Hackers took advantage of a third-party application that Marriott was using to offer guest services in January 2020. 5.2 million guest records from Marriott were accessed by the attackers. These records contained information on passports, contact information, birthdays, gender, dates of birth, loyalty account information, and personal preferences. At the end of February 2020, Marriott’s security staff identified unusual behavior and patched the security hole caused by an insider.
https://www.ekransystem.com/en/blog/real-life-examples-insider-threat-caused-breaches
Protecting Your Business from Within
To protect your business from insider threats, you should take a multi-layered approach that includes the following:
- Develop a Comprehensive Security Policy: Guidelines for access control, data handling, and incident response should all be included in your security policy. It should also specify what you anticipate from insider behavior. Ensure that your staff and insiders are familiar with your policies and receive ongoing training on security best practices.
- Monitor Your Networks: You should keep an eye out on your networks for any strange login patterns, unwanted access, or data exfiltration. Use security tools to assist you to identify and stop insider threats, including intrusion detection systems, data loss prevention software, and network analytics tools.
- Control Access to Sensitive Data: Only employees who require it for their job duties should have access to sensitive information. To prevent unwanted access to your data, user access controls such as role-based access control, multi-factor authentication, and encryption.
- Conduct Background Checks: Do rigorous background checks on potential new hires or contractors before hiring them to make sure they have a history of moral behavior and are clear of any criminal activity.
- Respond Quickly to Security Incidents: If you suspect an insider threat, respond quickly to contain the incident and prevent further damage. Have an incident response plan in place and test it regularly to ensure that it’s effective.
Conclusion
In conclusion, safeguarding your company against insider threats necessitates a multifaceted strategy that includes keeping an eye on key assets, developing strict policies and procedures, performing background checks and ongoing monitoring, limiting access and permissions, and putting data loss prevention tools into place. You can protect your company from the potentially disastrous effects of insider threats by following these steps.
Kratikal, Cert-In-empanelled organization with expertise in cybersecurity that provides useful information and strategies to assist companies in protecting themselves against insider attacks. They help businesses identify key assets, develop policies and processes, perform background checks, set access and permission limits, and implement data loss protection solutions. Businesses can reduce the risks associated with employee misconduct and data breaches by collaborating with Kratikal or other cybersecurity experts to take preventative measures to safeguard themselves from insider threats. A company’s reputation, financial stability, and long-term success can all be protected by investing in cybersecurity measures.
Want to Protect Yourself from Insider Threats?
Get your Security Testing Now!!









Leave a comment
Your email address will not be published. Required fields are marked *