 Security analysts and researchers from around the globe have made recent discoveries regarding an Iran-linked rookie hacker group, carrying out financially-motivated cyber attacks. These malicious activities by the hacker group started back in June 2020. The Iranian cybercriminals have been perpetrating ransomware attacks on victims, using “Dharma Ransomware” and a combination of publicly available hacking tools.
Security analysts and researchers from around the globe have made recent discoveries regarding an Iran-linked rookie hacker group, carrying out financially-motivated cyber attacks. These malicious activities by the hacker group started back in June 2020. The Iranian cybercriminals have been perpetrating ransomware attacks on victims, using “Dharma Ransomware” and a combination of publicly available hacking tools.
They have been mainly targeting companies headquartered in Russia, Japan, China, and India. The companies that were affected by the Dharma Ransomware attack reportedly had employees with Internet-facing Remote Desktop Protocol and were using weak credentials. After successfully encrypting the systems of victims, the hackers demanded a ransom of around 1 to 5 BTC.
The group originated from Iran, much like most of the infamous APT groups that have been functioning for the past decade. Researchers have also claimed that some of these infamous hacking groups might even be sponsored by the state itself.
While most of the attacks perpetrated in the past by these Iranian cybercriminals were information-driven, the recent attacks with the use of Dharma Ransomware were more financially-motivated.
Table of Contents
What is Dharma Ransomware?
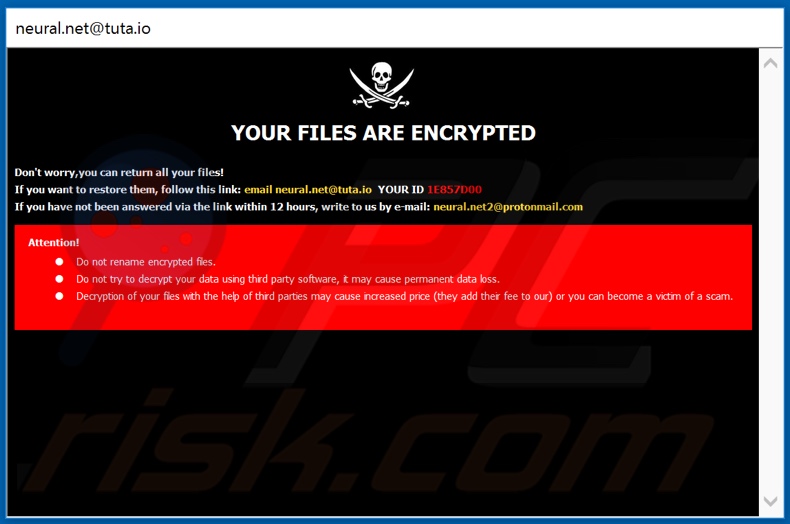
Dharma Ransomware Attack
Security analysts have been noticing an increased distribution of Dharma Ransomware in recent times. The ransomware is infamously known as Crysis, which has been sold or distributed as a RaaS (ransomware-as-a-service) model since the year 2016.
In March 2020, the source code for Dharma Ransomware was auctioned for sale online, making it easily available for a much wider range of interested audiences.
During an incident response session of a Russian Organization, security professionals first detected that a group of Iranian rookie hackers was using Dharma Ransomware to encrypt the systems of company officials.
The accurate number of victims who had fallen prey to the ransomware attack is yet to be disclosed. However, researchers have claimed that the methods and tools implemented by the criminals were far from advanced, and were not at all as sophisticated as those implemented by other popular Iran-linked APT hacking groups from Iran.
Details on the Ransomware Attack
Iranian Rookie Hackers Launch Ransomware Attack
The attackers run scans trying to hunt down potential victims from companies focusing on IPs of hosts with Internet-facing RDP and weak credentials. The scans were run on companies situated in Russia, China, India, and Japan.
This was done with the help of a software known as Masscan. This software was also deployed by Fxmsp, a seller who has access to a wide range of corporate networks, dispensing access to unauthorized hackers in exchange for money.
As soon as cybercriminals identified their potential victims, they launched NLBrute to enforce their way into the operating system of the victim. Once inside the system, the attackers further checked whether the credentials that they had obtained were valid for other victims sharing the same network.
To search for more accessible systems of victims sharing the same network, attackers made use of Advanced Port Scanner, a publicly available tool. While perpetuating the attack on some of the victims, the attackers even attempted to increase their access by running an exploit for CVE-2013-0213.
It appeared to researchers that criminals did not have a well-defined plan of action regarding what to do with the networks they had infiltrated. After establishing RDP connections, the hackers determined the tools to be used to move ahead with the attack.
They took the help of Defender Control and Your Uninstaller to disable the pre-existent antivirus software present in the victim’s system. Researchers searched in Google artifacts to discover that the latter was installed by the hackers from an Iranian website using the google search query “ دانلود نرم افزار “, in Persian.
The agenda of the criminals was to ultimately deploy a variant of Dharma Ransomware in the system of the targeted victims and charge a ransom to decrypt the system.
The Importance of Social Engineering Attack Awareness
Oleg Skulkin, Senior Digital Forensic Specialist says,
“The fact that Dharma source code has been made widely available led to the increase in the number of operators deploying it. It is surprising, Dharma landed in the hands of Iranian script kiddies who used it for financial gain, as Iran has traditionally been a land of state-sponsored attackers engaged in espionage and sabotage.
Despite that these cybercriminals use quite common tactics, techniques, and procedures they have been quite effective. Therefore, we believe it’s important to provide some recommendations on how to protect against them and give a complete outline of the MITRE ATT&CK mapping.”
While criminals are deploying various tactics to take advantage of the naivety of the employees in organizations, it is important to stay one step ahead. Propagating awareness of cyber attacks and attack vectors can be an extremely useful and effective solution to such a complicated problem.
Companies must ensure that their CISOs, CIOs, and equivalents are implementing cybersecurity awareness and training programs that cover all necessary attack vectors such as Phishing, Vishing, Smishing, and Ransomware.
How Does a Cybersecurity Awareness and Training Program Work?

Cybersecurity Awareness and Training in Organizations
As a CISO in a leading organization, implementing a robust cybersecurity policy to safeguard sensitive company information, is imperative. Security analysts may ask for aid from the IT department to come up with AI-driven cybersecurity solutions and tools in their respective organizations.
A social engineering attack awareness and training program can help employees to gain better insights into the various attack vectors used by hackers to infiltrate corporate networks and systems. Proper awareness among employees can reduce the chances of ransomware attacks such as the one by Iranian rookie hackers.
A cyber attack awareness and training program starts by simulating sophisticated impersonations of real-life cyber attacks on a company’s employees. This is followed by imparting knowledge of the various types of attack vectors.
This is done through awareness content giving a detailed insight into them, visual presentations on attack identification, as well as video lectures and advisories on the same.
Cumulative assessments or quizzes are then taken to ensure improvements and initiate a better response against attacks. Detailed analysis of simulation reports is provided that discloses accurate details on how many employees had received the malicious email, how many had clicked on the fraudulent link, and how many of them had submitted their corporate credentials.








Leave a comment
Your email address will not be published. Required fields are marked *