SOC 2 (Service Organization Control Type 2) is an audit report that verifies the trustworthiness of a service organization’s offerings, particularly for outsourced software solutions that store customer data online. Conducted by a Certified Public Accountant (CPA) under AICPA standards, SOC 2 audits evaluate attributes like Security, Availability, Processing Integrity, Confidentiality, and Privacy. These reports confirm that a service, such as a SaaS solution, has been rigorously assessed for risks in these areas, ensuring the organization’s commitment to protecting customer data. To achieve SOC 2 certification, an organization must first define its security controls and determine which Trust Service Criteria (Security, Availability, Processing Integrity, Confidentiality, and Privacy) are relevant to its services. Read this blog and get to know how organizations can obtain SOC 2 certification.
Table of Contents
Overview of SOC 2 Framework
The SOC 2 framework is widely adopted by service organizations, particularly SaaS companies, due to its flexibility. Unlike rigid cybersecurity frameworks, SOC 2 certification allows organizations to define how they implement cybersecurity controls, as long as they meet the intended criteria and adequately address risks. SOC 2 is closely aligned with the 17 principles of the COSO framework from 2013, using these as a foundation for many of the Common Trust Services Criteria.
In the U.S., SOC 2 certification has become the standard for service organizations to demonstrate the quality of their controls. Global companies seeking business with U.S. customers often pursue SOC 2 attestation to secure new contracts or retain existing clients.
To obtain a SOC 2 report, an organization must undergo a third-party audit of its system and organizational controls. The auditors review evidence and documentation to ensure that management’s claims about internal controls are accurate. In short, third-party auditors verify that companies seeking SOC 2 attestation are following through on their security controls.
For preparation for a SOC 2 audit, organizations must implement policies, procedures, and controls that align with SOC 2 criteria. While the American Institute of CPAs (AICPA) doesn’t conduct the audits, it provides guidance on what criteria make a company compliant with SOC 2. During the preparation process, organizations may need to establish access controls, data protection measures, and consider a readiness assessment or conduct an internal audit before the external review.
Book Your Free Cybersecurity Consultation Today!
How to Choose the Right SOC 2 Report Type for Your Organization?
Companies typically rely on two main types of SOC 2 reports, both of which address the same principles but differ significantly in scope and detail.
SOC 2 Type 1
A SOC 2 Type 1 audit serves as a detailed blueprint. It analyzes the design of an organization’s security controls at a given point in time. This audit provides an important snapshot, indicating a commitment to strong security design. However, it does not evaluate how well those controls are implemented in practice.
SOC 2 Type 2
A SOC 2 Type 2 audit is the preferred method for a more thorough review. It goes beyond the planning stage, functioning as the main part of the SOC 2 audit after SOC 2 Type 1 audit. Here, the auditor carefully assesses the operational efficiency of the controls. They evaluate not just the required controls, but also evaluate how consistently they are implemented.
SOC 2 Certification Process
To achieve SOC 2 certification and comply with the latest report framework standards, teams must adopt the 2017 Trust Services Criteria (TSC).
The Trust Services Criteria, formerly known as Trust Services Principles, outline the required controls that organizations must implement across their operations and IT infrastructure. The five categories of control criteria are:
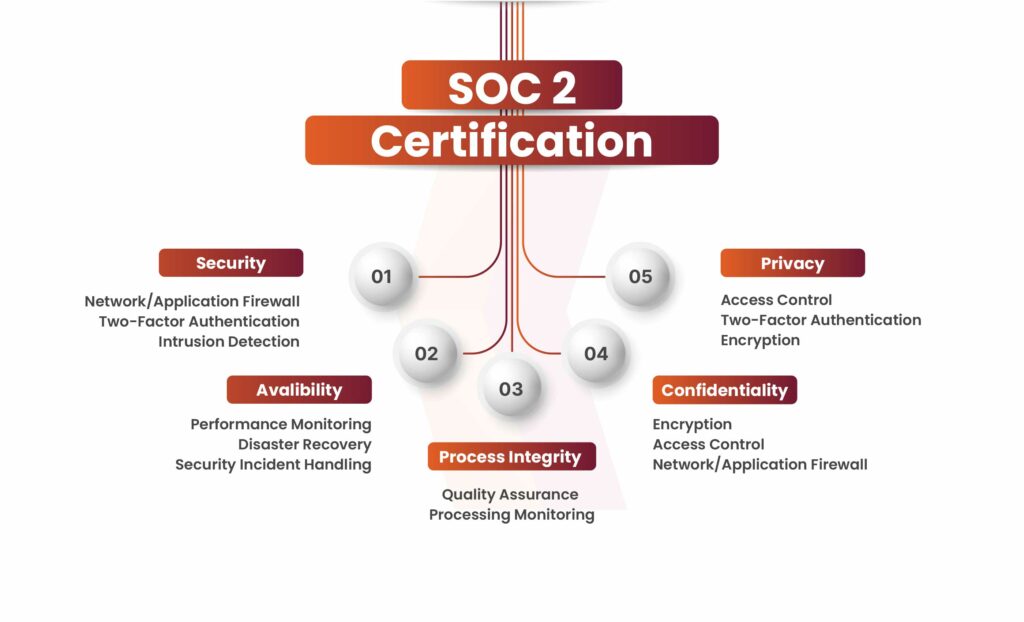
Security
A business’s data and computing systems must be fully protected from unauthorized access, improper information disclosure, and potential damage that could compromise the processing integrity, availability, confidentiality, or privacy of data or systems, which may impact the organization’s ability to achieve its objectives.
Security criteria focus on safeguarding:
- Information is collected, created, used, processed, transmitted, and stored throughout its collection, creation, and storage.
- Systems that process, transmit, or store electronic information to help the organization meet its objectives.
Security controls are designed to prevent or detect issues like system failure, incorrect processing, theft, unauthorized access, segregation of duties breakdowns, software misuse, and improper disclosure, alteration, or destruction of information or resources.
Availability
All information and computing systems must be consistently available and ready for operation to support the organization’s objectives.
Availability refers to the accessibility of information within your organization’s systems, as well as the products or services offered to customers.
While availability criteria don’t establish a minimum performance standard, they ensure that systems have controls in place for operation, monitoring, and maintenance. These criteria focus on accessibility but do not cover system functionality (the specific tasks a system performs) or usability (how users apply system functions to tasks or issues).
Processing Integrity
All system processing must be accurate, complete, valid, timely, and authorized to ensure the organization meets its objectives.
Processing integrity refers to the controls and procedures that ensure:
- The completeness, accuracy, validity, timeliness, and authorization of system processing.
- Systems achieve their intended purpose and function properly, free from errors, delays, omissions, and unauthorized or accidental manipulation.
Confidentiality
Confidential information must remain secure to ensure the organization meets its objectives. Confidentiality refers to the controls and procedures that ensure:
- Protection of confidential information from its collection or creation through to its final disposition or removal.
- Compliance with confidentiality requirements set by laws, regulations, contracts, or agreements made with customers or third parties.
Unlike privacy, which applies specifically to personal information, confidentiality covers a broader range of sensitive data types.
Privacy
The privacy principle governs the collection, disclosure, storage, use, and disposal of personal information in line with the Generally Accepted Privacy Principles (GAPP) established by the AICPA. It applies to Personally Identifiable Information (PII), which can identify individuals, such as names, addresses, phone numbers, and Social Security numbers. Other data, like race, gender, medical records, and religion, are also protected under GAPP. Auditors must verify that appropriate controls are in place to prevent the unauthorized sharing of PII.
Process to Get SOC 2 Certified
- Determine which trust principles you wish to have audited. While the security principle serves as the foundational requirement, you may also choose to include the principles of availability, processing integrity, confidentiality, and privacy in the audit.
- Establish the controls that will reflect the selected trust principles within your environment. You can accomplish SOC 2 certification with assistance from a third party, or through internal resources. Additionally, ensure that these controls are agreed upon in principle by your designated auditor.
- Conduct a self-assessment of your security processes and controls in relation to your chosen trust principles, or seek the support of cybersecurity professionals to ensure you are adequately prepared for a formal audit.
- Participate in a formal SOC 2 audit conducted by a certified CPA, which generally takes several weeks to complete. This process may involve employee interviews, documentation review, screenshots, log analysis, and a considerable investment of time. A third-party partner can manage the audit process for you, helping to make it as efficient and seamless as possible.
- Obtain a SOC 2 attestation report detailing how effectively your security controls met the security standards and trust principles of SOC 2.
Get in!
Join our weekly newsletter and stay updated
How Can Kratikal Help You With SOC 2 Compliance?
Kratikal can assist you in achieving SOC 2 compliance by providing expert guidance throughout the entire certification process. As the lead implementer and auditor, our expert team provides a comprehensive approach by helping you define essential controls aligned with the Trust Services Criteria, conducting readiness assessments, and performing internal audits to identify and address potential gaps. Additionally, Kratikal can facilitate the formal audit process by coordinating with certified auditors, ensuring that your security processes are thoroughly evaluated and that you receive a detailed SOC 2 attestation report. With their support, you can navigate the complexities of SOC 2 compliance efficiently and effectively, ultimately strengthening your organization’s commitment to data security.
FAQs
- How to get SOC 2 certification?
To obtain SOC 2 certification, you must appoint an auditing firm. Choosing the right firm is critical to the auditing and implementation process. An experienced auditor helps ensure the certification is completed on time.
- Who provides SOC 2 certification?
Any licensed CPA can conduct a SOC 2 audit, as there is no official certifying body. While the American Institute of CPAs (AICPA) establishes SOC 2 standards, it does not issue certifications, meaning there is no universally recognized SOC 2 certification.
- How to start SOC 2 audit?
Conduct a SOC 2 readiness assessment to identify any control gaps and address any issues. Choose the Trust Service Criteria that align best with your customers’ needs for your audit.
- Which companies need SOC 2?
The following organizations meet the description: Software as a Service (SaaS) providers and companies involved in business intelligence or analytics. This includes financial institutions such as banks, investment firms, insurance, and security companies. Additionally, any organization that stores customer data in the cloud also fits the criteria.







Leave a comment
Your email address will not be published. Required fields are marked *