It has come to light that Chinese hackers are carrying out cyber attacks on the Afghan government as a part of an espionage campaign. Cyber security researchers believe that this campaign might have started in the year 2014.
According to an article by The Hacker News, research into this matter has led experts to believe that these attacks are being carried out by the hacker group IndigoZebra APT. In the past, this hacker group has been linked with cyber attacks targeting Central Asian countries.
Take a Moment to Stay Tuned Forever
Subscribe to get weekly cyber security updates!
Details of these Attacks
“The threat actors behind the espionage leveraged Dropbox, the popular cloud-storage service, to infiltrate the Afghan National Security Council (NSC),” the researchers said in a technical write-up shared with The Hacker News, adding that the hacker group designed and launched a ministry-to-ministry style deception, in which an email is sent to a high-profile target from the email of another high-profile victim.
The email sent to the recipients asked them to review the modifications made in an attached document related to the pending Afghan National Security Council (NSC) press conference. However, this was a malicious password-protected RAR archive (NSC Press conference.rar) file, opening which triggers an infection chain that ends up installing a backdoor (spools.exe) on the victim’s system.
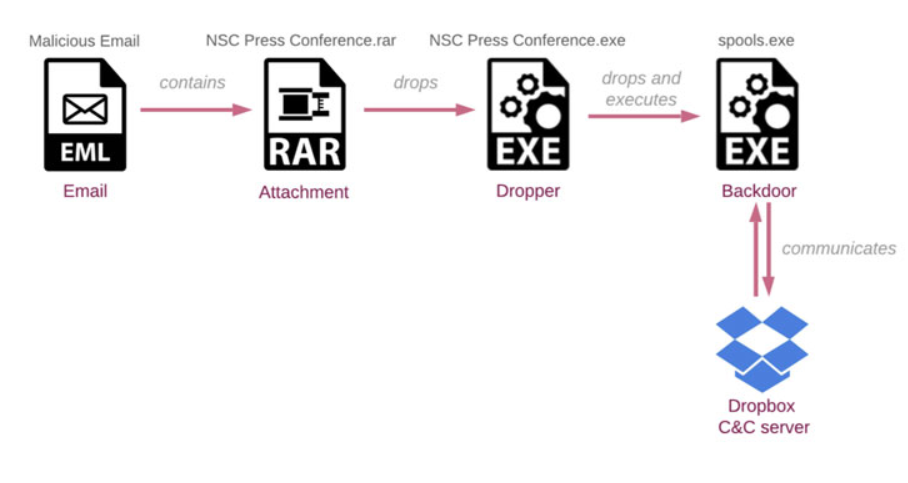
Source – The Hacker News
In addition to this, the attacks inserts malicious commands into the victim’s system, camouflaged using Dropbox API. This creates a unique folder in an attacker controlled Dropbox account for every compromised user.
The malware deployed in this cyber attack, codenamed BoxCaon, can steal confidential data stored on the device, run arbitrary commands, and source back the results back to the Dropbox folder. The ‘c.txt’ commands are placed in a separate subfolder of the victim’s Dropbox folder. This is utilized by the malware prior to its execution.
The article mentions that the ministry-to-ministry deception and the use of Dropbox to avoid detection is a very clever tactic.






Leave a comment
Your email address will not be published. Required fields are marked *