Table of Contents
What is Flubot Malware?
The NCSC explained in its guidance post, “The tracking app is in fact spyware that steals passwords and other sensitive data. It will also access contact details and send out additional text messages – further spreading the spyware.”
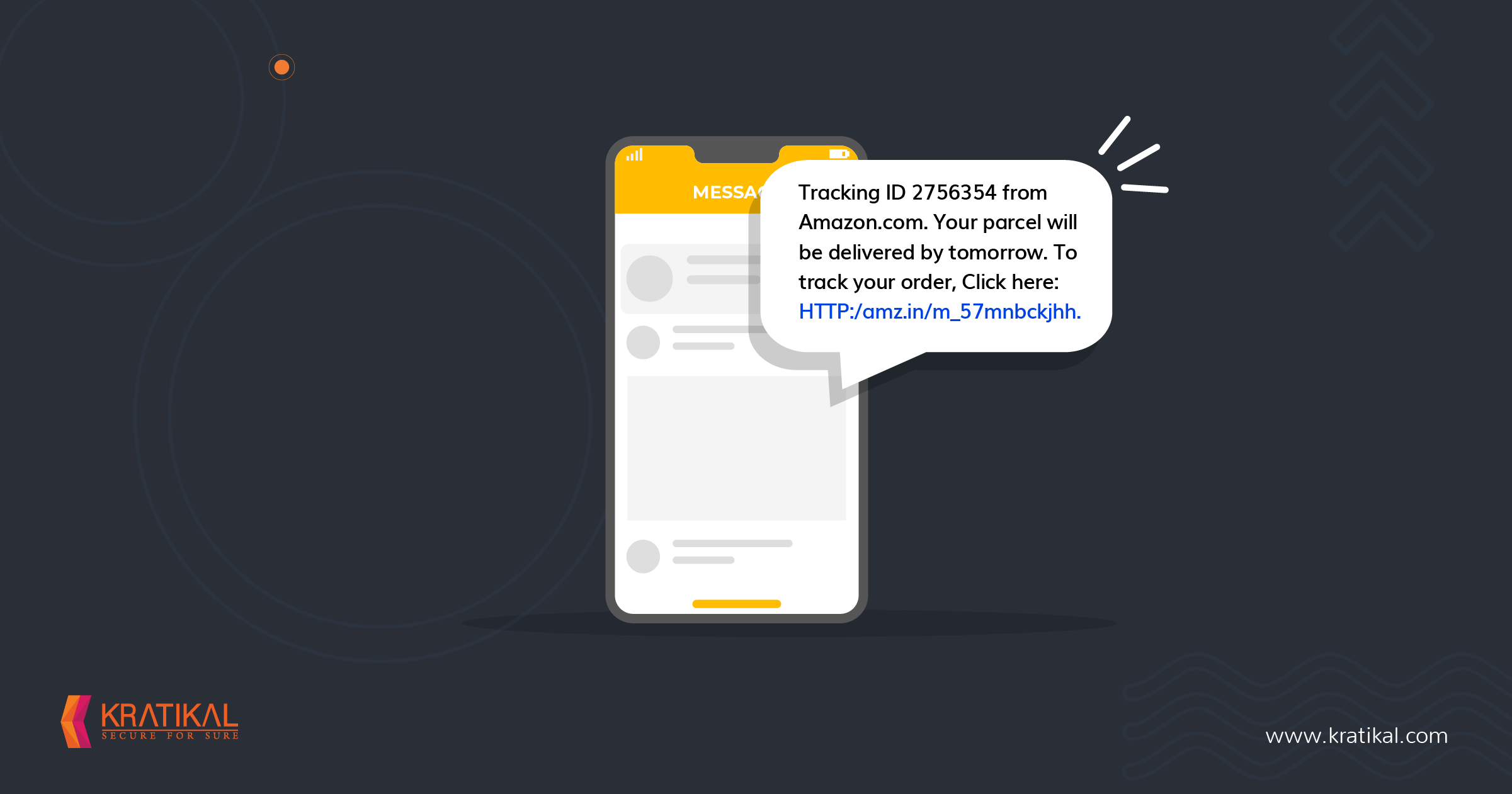
As outlined by the NCSC, the malware tricks the victims, making them feel they have missed a delivery package. Then it urges the victim into downloading a “tracking app” through a link that is delivered via SMS.
Needless to say, it’s actually spyware and not a “tracking app.” Once the victim downloads the app, it gains access to the device including information such as:
- Credentials
- Passwords
- Banking information
- Personal information
Basically, it gains access to almost every piece of information available on the device. Something that’s even worse about it is that it also sends out the same message as the victim received to all the contacts that are available in the phone’s contact book.
In order to succeed in tricking the victim, these messages impersonate big brands like Amazon, DHL, etc.
Telecom network providers such as Vodafone and EE have also cautioned their users that they should be aware of the scam.
A tweet from Vodafone UK News Centre tweeting about the malware (Source: Twitter)
At the present time, the spyware is only targeting Android devices, so iOS or any different operating system is safe. However, clicking the link on the scam message may redirect them to a phishing website which can result in loss of personal information. Therefore, it is better to stay aware of such scams and avoid them.
Cyber Security Expert Explains How Flubot Works
“When an Android user taps the malicious link, they are forwarded to a page where they are prompted to download an app so they can track their package. Once installed, the infected app Flubot can intercept and send SMS messages, display screen overlays, and steal contacts. iOS users, by comparison, are directed to phishing pages that link to other malware or impersonate major banks in the hopes of stealing that user’s mobile banking login credentials. Almost 80% of mobile phishing attacks are intended to deliver malware like FluBot.”- Burak Agca, Mobile Cyber Security Expert, Mobile Threat Defence, Mobile Threat Intelligence.
How to Prevent Flubot Malware?
Malicious actors will go to any extent to steal your personal information. With the current COVID-19 situation, almost every company in the nation is adopting remote working culture. This means an increase in usage of unsafe networks and mobile applications for connecting with colleagues and also other activities such as online shopping.
Moreover, no one would want to miss a parcel, especially in times like these. So, in order to stay protected from Flubot malware or similar spyware, it is best to implement the right cyber security measures. Therefore, here are two steps you should implement:
Step 1. If you or any of your employees have already downloaded the spyware
The first thing you need to do if you have logged into any accounts after downloading the spyware then change the password of those accounts immediately. Moreover, if you are using the same password for different accounts then it needs to be changed as well. Also, convey the same message to your employees or colleagues.
Make your employees or colleagues be aware of such attacks and let them know that if they receive such messages then they should delete them.
Step 2. Be prepared to combat such scams, this is not the first nor will it be the last
It is always best to stay prepared to tackle such cyber attacks. As you must be pretty aware, thousands of cyber attacks have taken place and billions of personal data have been lost in the past. Cyber criminals will always find their way to come back at you to steal your valuable data.
Such a kind of cyber attack, that targets their victims through SMS, is called smishing. It is worth mentioning that such attack vectors on top of phishing, ransomware had surged up significantly during the last lockdown. You wouldn’t want that to happen again.
According to Mint, cyber attacks surged 3-fold to 1.16 mn last year in India. Moreover, as per Intelligent CISO, UAE witnessed 70,000 cyber attacks on smartphones in 2020 during the quarantine period.
It is time now organizations realize they need to be prepared in order to tackle such cyber crimes. For that employees are to be focused in the first place, after all, they are the first line of defense against cyber attacks.
Providing them cyber security awareness training with tools like ThreatCop will help them know how these cyber attacks look like. Moreover, it will also make them aware of how to avoid such attacks.
All the resources you need are available to you, in order to prevent your organization and yourself. However, implementing them is up to you! Meanwhile, let’s not forget “Prevention is better than cure.”
If you like reading our blogs, you can also follow us on LinkedIn or subscribe to our Newsletter to get cyber security news and updates regularly.








Leave a comment
Your email address will not be published. Required fields are marked *