The rapid adoption of cloud-based platforms has brought a parallel rise in security risks. Microsoft Azure, a widely used cloud computing platform, enables users to build, manage, and deploy applications through its global network of data centers. Due to the sensitive nature of data stored and processed, Azure pentesting is crucial to uncover and address security vulnerabilities.
According to IBM’s cloud security statistics, the average cost of a data breach in 2023 was $4.45 million. Over 51% of organizations worldwide now plan to enhance their cloud security efforts. Another report reveals that 83% of companies experienced a cloud security breach in the past year, and 58% of developers expect these risks to grow in the coming year.
While Azure offers robust built-in security, users must proactively test their environments to protect critical data and assets. This blog will cover what Azure penetration testing entails and the common misconfigurations that are found during the pentesting process in Azure.
Table of Contents
What is Azure Pentesting?
It is a proactive security assessment method used to identify and address vulnerabilities within Microsoft Azure cloud environments. It involves simulating real-world cyberattacks to test the security posture of Azure-hosted applications, virtual machines, networks, storage, and other cloud resources. This testing helps organizations uncover misconfigurations, insecure APIs, access control issues, and other potential threats before attackers can exploit them. By regularly performing Azure pentests, businesses can ensure compliance with security standards, strengthen their cloud defenses, and maintain the confidentiality, integrity, and availability of their data and services.
Misconfigurations Found During Azure Pentesting
Microsoft Azure has become a go-to cloud computing platform for businesses worldwide, offering unmatched scalability, flexibility, and a wide range of innovative services. However, with its powerful capabilities comes the crucial responsibility of managing and securing Azure environments effectively. Misconfigurations can lead to serious security and performance challenges, including data breaches, increased costs, and reduced system efficiency. Below are some of the misconfigurations found during Azure pentesting:
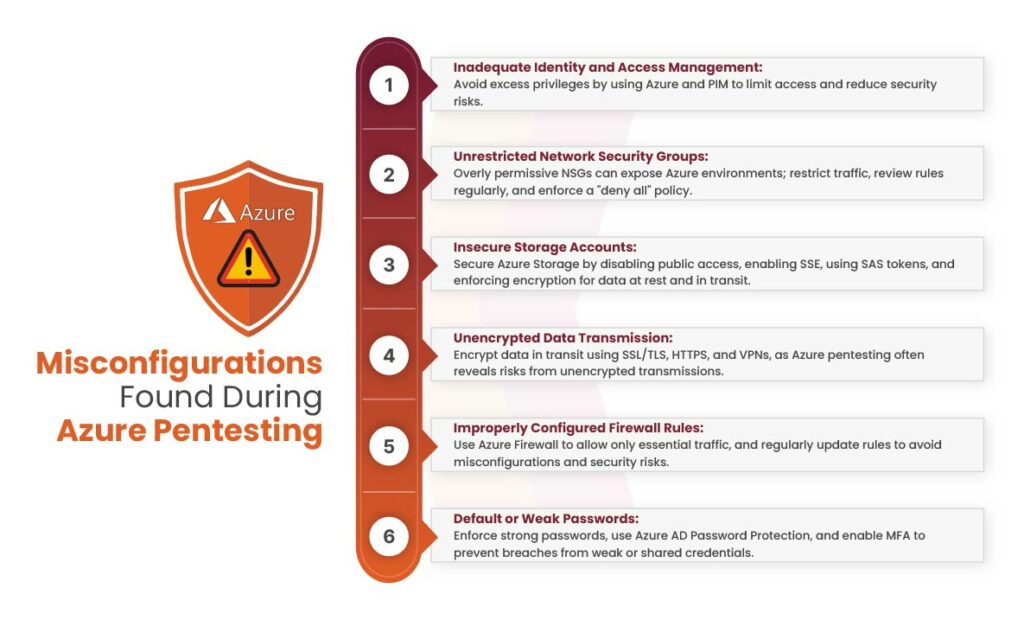
Inadequate Identity and Access Management
Misconfigurations often arise when permissions are overly broad, granting users more access than their roles require—commonly known as excessive privileges. This increases the risk of security breaches, especially if those credentials are compromised. To minimize exposure, use Azure Active Directory (AD) for identity management, implement role-based access control (RBAC), and apply the principle of least privilege to ensure users only have the access necessary for their tasks. Additionally, leverage Azure’s Privileged Identity Management (PIM) to enable just-in-time access, reducing risks linked to constant privileged access.
Unrestricted Network Security Groups
Unrestricted Network Security Groups (NSGs) are among the most common misconfigurations uncovered during Azure pentesting. NSGs act as cloud-based firewalls, managing inbound and outbound traffic to resources within Azure Virtual Networks (VNets). When these rules are too permissive, they can allow unauthorized access, exposing your environment to data breaches and malicious activity. Azure pentesting helps identify such vulnerabilities, emphasizing the need to restrict NSG rules to only essential traffic. Regularly review and update these rules to match current operational needs, and always include a “deny all” rule as the final layer of protection in your NSG configuration.
Insecure Storage Accounts
Azure Storage offers scalable and secure cloud storage for data objects, files, disks, and queues. However, improper configurations can expose your data to unauthorized access and security risks. Common misconfigurations include enabling public access to storage accounts or failing to encrypt data at rest or in transit. Publicly accessible storage can lead to data breaches or loss. To mitigate these risks, disable public access unless absolutely required, enable Azure Storage Service Encryption (SSE) for protecting data at rest, use Shared Access Signatures (SAS) for controlled, time-limited access, and enforce secure transfer to ensure encryption during data transmission.
Unencrypted Data Transmission
When data travels across the network without encryption, it becomes vulnerable to interception and misuse, increasing the risk of unauthorized access and data breaches. Azure pentesting often reveals such misconfigurations, where services are set up to transmit data without Secure Sockets Layer (SSL) or Transport Layer Security (TLS). To mitigate these risks, it’s essential to enforce encrypted connections for all data in transit. Azure provides features to enable secure transfer (HTTPS) for web applications and services like Azure Storage and Azure SQL Database. For virtual networks, implementing IPsec or SSL VPNs enhances security, while solutions like Azure VPN Gateway and Azure ExpressRoute establish secure, private communication channels.
Improperly Configured Firewall Rules
Firewall rules control network traffic by allowing or blocking it based on parameters like source and destination IP addresses, ports, and protocols. When misconfigured, these rules can either be too permissive—opening the door to unauthorized access—or too restrictive, disrupting application or service functionality. To maintain a secure environment, use Azure Firewall to allow only the traffic that is essential. Additionally, make it a regular practice to review and update your firewall rules to reflect changes in your network architecture and the evolving threat landscape.
Default or Weak Passwords
Default, simple, or shared passwords significantly increase the risk of unauthorized access, making it easier for attackers to compromise your resources. A single compromised account can often escalate into a broader security breach across the organization. To prevent this, enforce strong password policies and leverage Azure AD Password Protection to block weak or easily guessable passwords. Additionally, enable Multi-Factor Authentication (MFA) to add an extra layer of security and safeguard user accounts.
Book Your Free Cybersecurity Consultation Today!
Features of Azure Pentesting
Cloud misconfigurations can expose sensitive data, creating security risks. AutoSecT helps you detect and fix misconfigurations, prevent public exposures, analyze attack paths, and protect your cloud networking resources like VPC, load balancers, firewalls, etc., ensuring a secure, compliant, and resilient cloud environment. Below are the list of features in AI-driven VMDR and pentesting tool AutoSecT:
Detect Misconfigurations:
Cloud security tools, such as those integrated with Azure environments, play a vital role in maintaining a strong security posture by continuously monitoring your cloud infrastructure. These tools perform automated, periodic scans to detect any security gaps, misconfigurations, or deviations from best practices. They examine settings related to access control, storage permissions, encryption, firewall rules, and more. When a misconfiguration or vulnerability is identified, the tool generates immediate alerts, enabling your team to take swift corrective action.
Identifying Internet Facing Risks
One of the key functions of our cloud security tool is detecting critical resources that are unintentionally exposed to the public internet—such as open storage buckets, databases, virtual machines, or APIs. These internet-facing assets are prime targets for attackers and can lead to serious breaches if not secured promptly. Our tool continuously monitors your cloud environment and automatically flags these exposures. It prioritizes remediation efforts by highlighting high-risk resources, ensuring that the most vulnerable components are addressed first.
Configuration and Attack Path Analysis
Our cloud security tool continuously monitors and analyzes configuration changes across your cloud environment to detect risky modifications that could weaken your security posture. It keeps a historical record of how your cloud settings evolve over time, making it easier to spot deviations from best practices or compliance requirements. In addition to tracking changes, the tool performs attack path analysis by mapping out potential routes a hacker might take to exploit vulnerabilities, escalate privileges, or gain access to sensitive data.
AI-Powered Alert Management
Our VMDR (Vulnerability Management, Detection, and Response) tool uses advanced AI to intelligently manage and prioritize cloud security alerts. Instead of overwhelming your team with hundreds of individual notifications, it groups related alerts based on context, severity, and potential impact—bringing attention to the most critical threats first. The AI engine also provides actionable insights and tailored remediation steps for each issue, helping teams resolve vulnerabilities faster and more efficiently.
Book Your Free Cybersecurity Consultation Today!
Conclusion
As organizations increasingly migrate to cloud platforms like Microsoft Azure, ensuring robust security becomes not just important—but essential. While Azure provides a strong foundation with its built-in security capabilities, these alone cannot guarantee complete protection. Misconfigurations, overly permissive settings, weak credentials, and unencrypted data transmissions are just a few of the vulnerabilities that can easily go unnoticed without proactive security assessments. This is where Azure penetration testing proves invaluable, uncovering hidden weaknesses before attackers can exploit them.
Advanced tools like AutoSecT elevate cloud security by automating and enhancing the entire vulnerability management lifecycle. With features such as real-time misconfiguration detection, identification of internet-facing risks, attack path analysis, and AI-driven alert prioritization, AutoSecT empowers organizations to detect, prioritize, and respond to threats with speed and precision. It transforms reactive security efforts into a proactive, streamlined defense strategy.
FAQs
- Is conducting Azure pentesting essential?
Yes, Azure hosts critical applications and sensitive organizational data. Penetration testing is crucial for identifying and addressing potential security vulnerabilities within the platform.
- Which is the best practice to protect sensitive data in Azure?
The most effective way to safeguard sensitive data in Microsoft Azure is through encryption and data masking. Additionally, conducting penetration testing helps enhance security by uncovering and resolving vulnerabilities within the Azure environment.








Leave a comment
Your email address will not be published. Required fields are marked *