Did you know? NIST’s latest software guidelines rank threat modeling as the first among six key code-verification practices. They specifically recommend that teams perform threat modeling multiple times throughout development, especially when adding new features. This shift signals that government contracts will soon require documented threat models as part of their compliance standards. Industry frameworks like ISO/IEC 27005 (risk management) and the Cybersecurity Maturity Model Certification (CMMC) also emphasize the need for structured threat assessment during the design phase. Even Gartner has highlighted “secure by design”, with threat modeling at its core, as a top cybersecurity priority for 2025. Thus, this blog highlights all the important aspects of Threat Modeling and why your organization should think and act on it at the earliest.
Table of Contents
What is Threat Modeling?
During the software or application development process, it is a crucial initiative to find out the weaknesses and fix the flaws before launching it for the users. This is where threat modeling comes into play as a proactive defense strategy. Threat modeling is a structured approach to identify, prioritize, and mitigate potential threats and security risks before they take the shape of real threats. It is similar to doing a security check at the early stages of the software development life cycle (SDLC).
Furthermore, threat modeling helps security teams gather, organize, and analyze information about possible security threats. When used in software development, threat modeling provides a clear picture of where the risks are, so teams can make smarter security decisions. The process helps organize all possible threats and gives a clear action plan to improve security, whether in the design, code, or setup of the software.
Circumstances Where Threat Modeling is Applicable –
Threat Modeling can be applied as a preventive cybersecurity strategy for ensuring security is software, applications, networks, business processes, and IoT devices. It is best to apply threat modeling throughout the software development project and not just once.
At the beginning, threat modeling can help create a high-level overview of possible threats during the planning stage. As the project moves forward and more details are added, like features, connections, or code, the possibility of new risks appearing is higher. That’s why it’s important to keep updating the threat model as the development proceeds. This helps organizations spot and fix new security issues early, instead of waiting until the end.
In short, threat modeling should be a continuous process that evolves along with your software development.
Book Your Free Cybersecurity Consultation Today!
When Should an Organization Update Its Threat Model?
As a system evolves, new threats naturally appear, especially when organizations make technical choices. That’s why threat models should be updated regularly, not just created once and forgotten. By keeping your threat model up to date, your organization stays ahead of evolving risks and avoids security blind spots. You should revisit and update your threat model whenever:
- A new feature is added or released
- A security incident or breach occurs
- There are major changes in architecture or infrastructure, like moving to the cloud or adding third-party tools.
What is the Threat Modeling 4-Question Framework?
Threat modeling helps you think through potential security issues. This 4-Question framework helps keep threat modeling simple, structured, and actionable, making it easier for teams to build secure systems from the ground up. In short, this framework is a simple way to guide the process:
- What are you working on?
Start by defining the scope of what you’re analyzing. It could be a small feature, an app, or an entire system. The goal is to clearly understand what you’re building.
- What can go wrong?
Think about potential threats and vulnerabilities. This could be done through a simple brainstorming session or by using tools like STRIDE to uncover common attack patterns.
- What are you going to do about it?
For each threat you’ve identified, decide how to reduce or manage the risk. This might involve fixing the issue (mitigation), accepting the risk, transferring it, or eliminating the risky feature entirely.
- Did your organization and the testing team do a good job?
Review the work. Did you find and address the major threats? Is the system secure enough for what it’s meant to do? This step ensures continuous improvement.
Benefits of Threat Modeling
Threat Modeling comes with multiple benefits. They are:
- Detect Problems Early: The security team thinks like a hacker when threat modeling is done during the planning phase. The testing team spots the flaws before the code is written, thus making the fixes quicker and comparatively cheaper.
- Uncover Design Flaws That Tests Miss: Traditional testing looks at finished code. Threat modeling looks at ideas and architecture, revealing hidden issues a test suite can’t see.
- Prepare for New, Creative Attack Tactics: Using frameworks like STRIDE during threat modeling forces security analysts to imagine attacks you’d otherwise overlook, so surprises are less likely to appear in the later stage.
- Plan Your Security Budget Judiciously: Knowing which parts of the software, application, or system are more at risk lets you target VAPT, secure code review, or other testing as and when the need arises.
- Avoid Last Minute Flaws and Re-coding: Fixing a flaw during design takes minutes. On the other hand, fixing it after deployment can lead to expensive patches, downtime, and an unsatisfactory user experience.
- Provide Proof of Due Diligence: Having a threat model documented is evidence that your organization has done the homework. It becomes solid proof that can be presented to auditors, regulators, and customers, if needed.
- Stay Ahead of Both Insider and External Threats: Through Threat Modeling, you can map out who could attack and how. This will help you build defenses way before the hackers try.
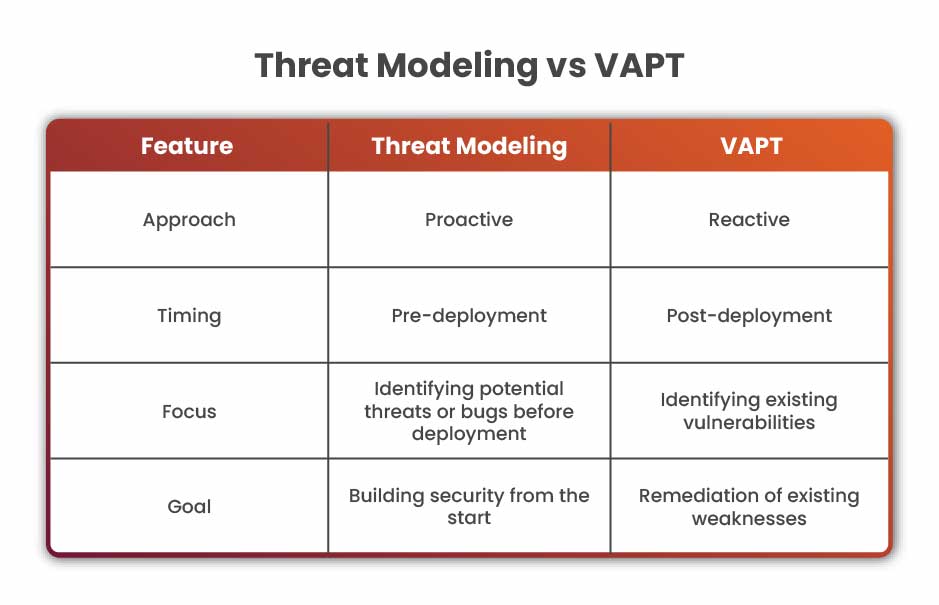
Difference Between Threat Modeling and VAPT
Threat Modeling is reactive and is done to identify potential threats a vulnerabilities before a software or application is built or deployed. It involves analyzing the application or software architecture to identify potential attack vectors and determine the likelihood and impact of those threats. It is usually performed at the time of the design and development phase.
On the other hand, VAPT (Vulnerability Assessment and Penetration Testing) is reactive and focuses on finding vulnerabilities that already exist in a software, system, or application. It involves identifying, assessing, and prioritizing vulnerabilities, followed by emulating real-life attacks to test the level of exploitability and suggesting patching recommendations. It is performed after a software or application is developed and deployed.
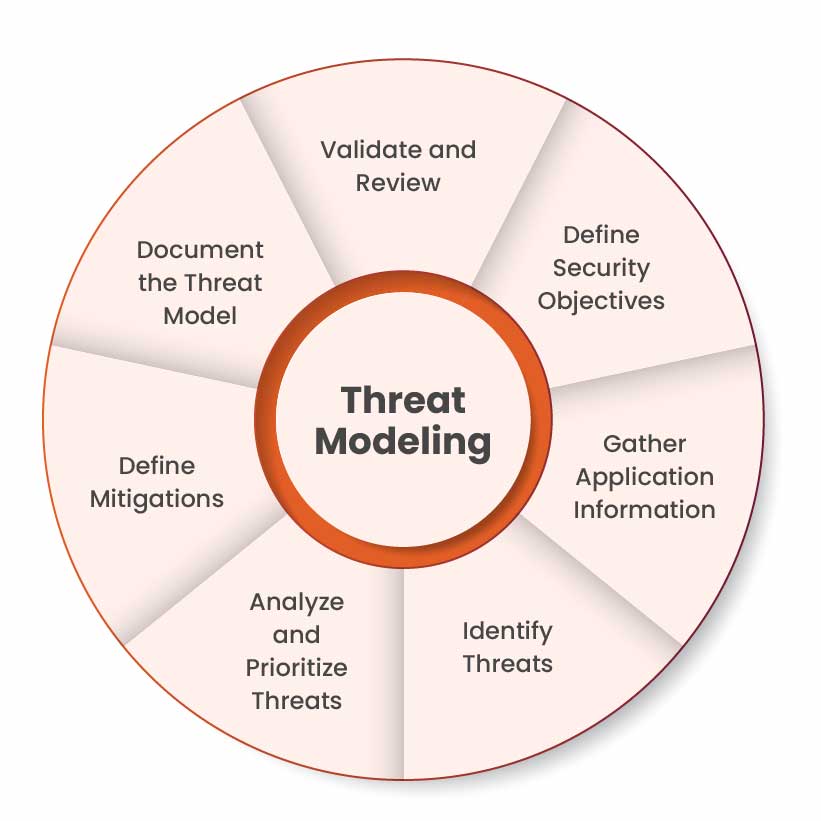
Kratikal’s Threat Modeling Methodology
This threat modeling methodology by Kratikal ensures your organization builds security into your app from the ground up, rather than fixing issues after they happen. It’s proactive, practical, and protects your business and users. It is done in the following manner:
Step 1: Define Security Goals
Understanding the purpose of your application and what you need to protect.
- What does the app or software do? What’s important to its success?
- What are the key security goals?
- Confidentiality: Keep user data private
- Integrity: Make sure data and actions can’t be tampered with
- Availability: Ensure the system stays up and running
- Are there any compliance requirements?
Step 2: Understand the Application
Breaking the application or software into parts to understand how it works and where it might be attacked. Flow charts like Data Flow Diagrams (DFDs) and System Architecture Diagrams are used to determine the same. This is done by –
- Listing components: servers, APIs, databases, third-party services
- Mapping data flow: How data moves from the user to the backend and back
- Identifying trust boundaries: Points where control shifts (e.g., frontend to backend)
- Noting entry/exit points: Like login forms, API endpoints, file uploads.
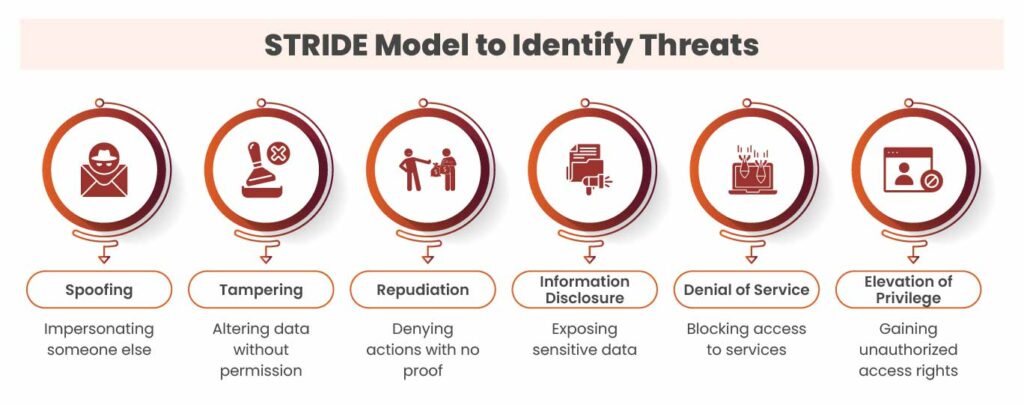
Step 3: Identifying Threats
Figuring out what can go wrong using the STRIDE model. It includes pretending to be someone else, modifying data without permission, denying actions with no proof, leaking sensitive info, shutting down services, and gaining access to things you shouldn’t.
Step 4: Analyze and Prioritize Risks
Not every threat is equally dangerous. Thus, Kratikal’s security team ranks them by risk level using models like:
- DREAD – Damage, Reproducibility, Exploitability, Affected users, Discoverability
- CVSS – Common scoring method for software vulnerabilities
- OWASP Risk Rating – Popular method for web application threats
Step 5: Planning Mitigations
Deciding how to deal with each threat through;
- Technical controls: Input validation, access control, encryption
- Process controls: Secure coding rules, security checks in CI/CD, peer reviews
- Monitoring controls: Web firewalls (WAF), logging, alerts, SIEM tools
Step 6: Documenting Everything
Writing down the security team’s findings and plans. The document includes Diagrams (DFDs, architecture), a list of threats, risk levels, plans to fix them, and any assumptions or limitations. This is done because good documentation helps with:
- Audits
- Team communication
- Future updates
Step 7: Validating and Keeping It Updated
Reviewing the model with key teams like developers, security, DevOps, and product owners. Also, updating the threat model in collaboration with the testing organization when:
- New features are added
- The system architecture changes
- New threats emerge in the real world.
Adopting Threat Modeling for Smaller Organizations or Startups
If you are a startup, a small enterprise, or have limited resources, this is how you can incorporate threat modelling to enhance the security of your organization:
- Contact Kratikal for a detailed explanation and focus on what is more important based on your organizational goals.
- Instead of focusing on all the vulnerabilities, start by focusing only on the critical vulnerabilities that your organization is most vulnerable to.
- Add threat modeling into regular activities like sprint planning, design reviews, or change management, so it becomes a natural part of the process, not extra work.
Get in!
Join our weekly newsletter and stay updated
As per recent reports, there has been a 34% increase in the exploitation of known vulnerabilities as compared to the previous year. Not only that, it became the initial access method for 20% of breaches. It has been found that incidents containing a breach in under 200 days saved over $1 million on average compared to slower responses. Failing to invest in shift‑left security, like threat modeling, means redesigns and incident response consume more time and budget later. Therefore, investing in threat modeling is important, and given the facts, this adjective is no more subjective.
FAQs
- Why is threat modeling important?
Threat modeling is crucial because it identifies and mitigates security risks early in the SDLC. It prevents costly fixes, supports “secure by design” practices, and helps meet compliance standards.
- How often should threat modeling be performed?
Threat modeling should be a continuous process, not a one-time task. It must be updated whenever new features are added, major architecture changes occur, or security incidents happen.








Leave a comment
Your email address will not be published. Required fields are marked *