Cloud Security Posture Management (CSPM) focuses on managing risks in public cloud infrastructures. CSPM tools help identify and fix misconfigurations in cloud resources (like Amazon EC2 instances) through automation. By leveraging CSPM, organizations operating in public and multicloud environments can minimize the risk of breaches and enhance compliance with regulations.
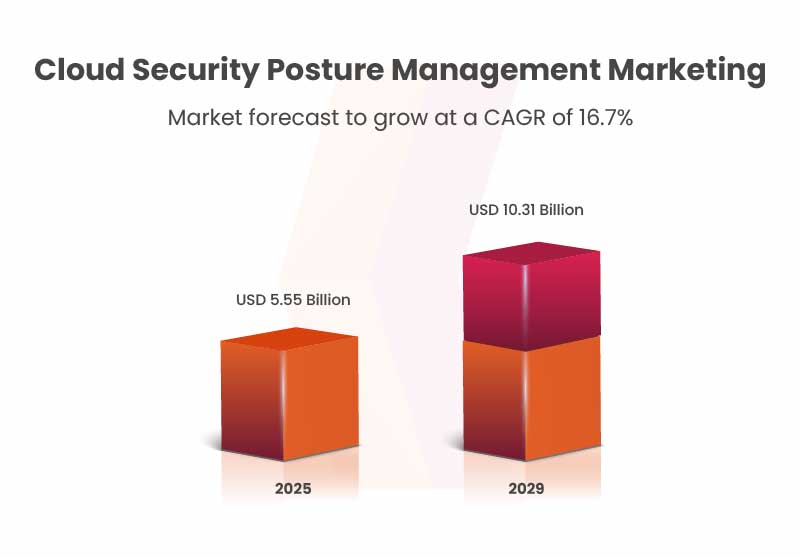
The CSPM market has experienced significant growth in recent years. It is projected to expand from $4.92 billion in 2024 to $5.55 billion in 2025, reflecting a compound annual growth rate (CAGR) of 12.8%. This growth is driven by factors such as the increased adoption of cloud computing, heightened concerns about data breaches and cybersecurity threats, and much more. The market is expected to reach $10.31 billion by 2029, growing at a compound annual growth rate (CAGR) of 16.7%.
Table of Contents
An Overview of Cloud Security Posture Management
CSPM reduces risks and ensures compliance by detecting and addressing misconfigurations in public cloud environments. CSPM tools support security and compliance teams with automated visibility, continuous monitoring, and workflows for remediating issues across Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS).
Typically, organizations adopt CSPM as a key security measure when migrating applications to cloud providers like Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP). Cloud security posture management tools play a crucial role in the shared responsibility model of cloud security by assisting client organizations in several significant ways.
The Role of AutoSecT in Enhancing CSPM
CSPM is essential as businesses continue to embrace public cloud platforms like AWS, Microsoft Azure, and GCP. Public and multicloud environments allow IT and development teams to configure and launch services and applications, driving faster innovation. Below are the points explaining the importance of Cloud security posture management with AutoSecT:
Cloud Security Configuration
AutoSecT enhances cloud security by detecting and resolving misconfigurations, preventing public exposures, and securing networking resources like VPCs, firewalls, and load balancers. It scans cloud environments like AWS, Azure, and Google Cloud for vulnerabilities, ensuring proactive detection and resolution. It prioritizes fixing critical risks while analyzing configuration changes and identifying attack paths. Our VMDR tool consolidates cloud-related security risks to spotlight the most critical threats, minimizing alert fatigue and providing actionable recommendations for effective remediation.
Compliance Management
AutoSecT simplifies cloud compliance management by automating checks, periodic monitoring, and generating audit-ready reports. It ensures compliance with industry standards such as PCI-DSS, GDPR, and HIPAA across multi-cloud platforms. By preventing regulatory violations, it supports maintaining a robust and secure compliance framework.
Data Security
AutoSecT’s CSPM solution enhances cloud data security by providing full visibility, control, and automated governance. It strengthens Data Privacy and Data Risk Analysis by detecting sensitive data, monitoring vulnerabilities, and preventing risks like excessive access and non-compliant transfers. With Data Access Governance (DAG), it maps permissions, tracks data interactions, and alerts on unauthorized access. The Data Detection and Response (DDR) feature ensures rapid threat identification and mitigation through agentless monitoring and instant alerts, enabling efficient incident response and compliance management.
Container Security
AutoSecT’s Container Security solution provides complete visibility and protection for Jenkins clusters and containerized workloads in the cloud. It tracks assets, scans for vulnerabilities, and enforces security controls with features like compliance assessment and risk prioritization. Additionally, it secures the DevOps pipeline by integrating security checks into CI/CD tools, enabling early detection and prevention of vulnerabilities in container environments.
Periodic Security
AutoSecT’s Periodic Security feature supports robust cloud security by enabling regular security audits and scheduled reviews to identify vulnerabilities and gaps. It also facilitates third-party risk management by assessing the security posture of cloud providers and vendors through periodic compliance checks.
Vulnerability Exposure Management
AutoSecT delivers proactive vulnerability exposure management by identifying, prioritizing, and remediating risks across your cloud, container, and CI/CD environments. It goes beyond surface-level scans by mapping vulnerabilities to real exposure paths, ensuring your team focuses on what truly matters. With contextual risk analysis, AutoSecT helps reduce attack surfaces and strengthens overall security posture.
Agentless Asset and Vulnerability Discovery
AutoSecT’s agentless asset and vulnerability discovery feature eliminates the need to install agents within your cloud environment, ensuring seamless deployment and zero disruption. By leveraging cloud provider APIs, AutoSecT collects real-time configuration and security data directly from your cloud infrastructure. This lightweight, non-intrusive approach offers comprehensive visibility into all assets.
Real-Time Monitoring
Real-time cloud monitoring involves continuous log analysis to identify and respond to security events promptly. It ensures compliance by proactively detecting and alerting on IAM policy changes, helping organizations maintain robust access controls and safeguard critical resources.
AI Driven Reconnaissance
AutoSecT enhances vulnerability assessment through intelligent risk detection and automated analysis. This feature leverages advanced AI algorithms to efficiently scan, classify, and eliminate redundant vulnerabilities, ensuring high-precision threat identification. By embedding AI into its security framework, AutoSecT optimizes attack surface monitoring and accelerates remediation workflows.
Book Your Free Cybersecurity Consultation Today!
How Does CSPM Work?
Grasping the fundamentals of Cloud security posture management is key to recognizing its impact on cloud security. The next section talks about how CSPM contributes to securing cloud infrastructure.
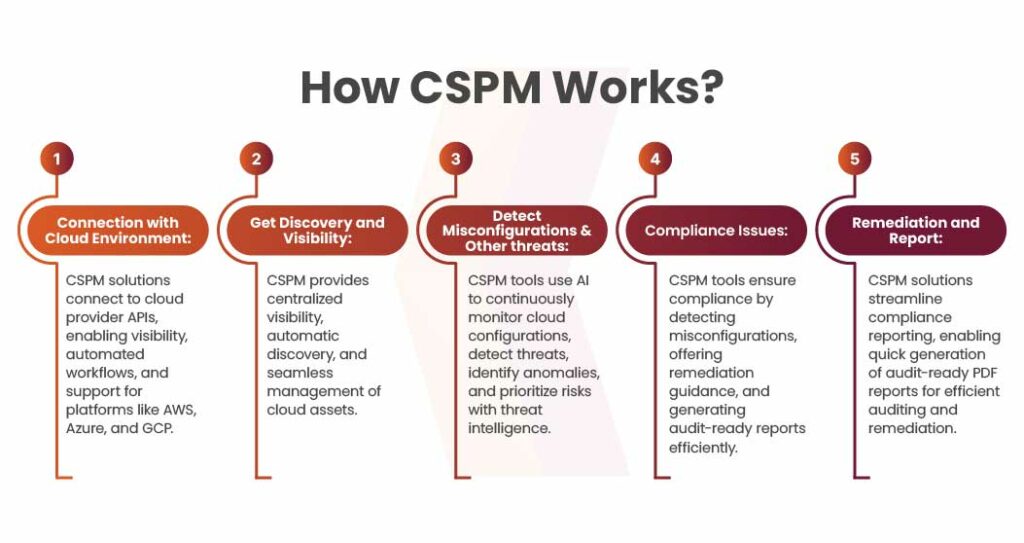
Connection with Cloud Environment
CSPM solutions use agentless security by connecting to cloud provider APIs for visibility. Organizations grant access for automated workflows, choosing between read-only or minimal read-write permissions.
Get Discovery and Visibility
CSPM offers comprehensive discovery and visibility into cloud infrastructure assets and their security configurations. It provides users with a centralized view across multi-cloud environments and accounts. Upon deployment, cloud resources and their details are automatically identified, covering aspects like misconfigurations, metadata, networking, security, and change activity. Security group policies are managed seamlessly across accounts, regions, projects, and virtual networks via a unified dashboard.
Regulatory Risk Mitigation
Many businesses adopting cloud infrastructure must comply with regulations like PCI DSS, GDPR, SOC 2, and HIPAA, which require specific security measures. Failure to maintain proper cloud configurations can result in noncompliance, leading to fines, legal issues, and reputational harm.
CSPM tools like AutoSecT help businesses meet these compliance requirements by automatically comparing cloud configurations to regulatory standards, identifying violations, and providing remediation guidance. Additionally, some tools offer compliance reporting, enabling security teams to generate audit-ready reports quickly and efficiently.
Remediation and Report
CSPM solutions simplify reporting by enabling security teams to generate PDF reports with a single click, verifying cloud infrastructure compliance with specific controls. These reports can be shared with compliance experts for auditing or provided to developers to address compliance concerns and prioritize remediation tasks efficiently.
Get in!
Join our weekly newsletter and stay updated
Conclusion
Cloud Security Posture Management (CSPM) plays a pivotal role in safeguarding public and multicloud environments, making it an indispensable tool for modern organizations navigating complex cloud infrastructures. By detecting misconfigurations, CSPM minimizes vulnerabilities that could lead to data breaches or noncompliance, ensuring a robust security framework. It automates compliance checks against regulatory standards such as PCI DSS, GDPR, SOC 2, and HIPAA, streamlining the effort required to meet industry regulations and mitigating risks of legal or financial consequences.
Advanced CSPM tools, such as AutoSecT, further enhance the effectiveness of cloud security by offering features like automated workflows, periodic monitoring, and centralized dashboards for visibility across multi-cloud setups.
FAQs
- What is posture management in cloud security?
Cloud security posture management involves mitigating risks within the public cloud infrastructure. CSPM tools streamline the process by automating the identification and resolution of misconfigurations across cloud resources, such as Amazon EC2 instances.
- What is a CSPM tool?
Cloud Security Posture Management (CSPM) addresses risks by automating visibility, continuous monitoring, threat detection, and remediation workflows. It identifies and resolves misconfigurations across various cloud infrastructures, including Infrastructure as a Service (IaaS).









Leave a comment
Your email address will not be published. Required fields are marked *